Details of Schoche Boom Can giveaway contest are available by subscribing to the NosillaCast News, the Podcast Award nominations are open at podcastawards.com. Knightwise explains his controversial comments from last week using Batman, Batman’s toothbrush and a pink tutu. Then George from Tulsa weighs in on Knightwise’s crazy ideas about Lion and shows us several ways to fix the “deprovements” in Lion. George provided links to Deeper.app, LionTweaks.app, TinkerTool , Cult of Mac’s Lion Tips, LifeHacker’s Lion Tips, and OsXDaily’s Lion Tips. Rod Simmons from the Simple Mobile Review Podcast joins us with his review of the Motion GPS Drive for iOS . In Chit Chat Across the Pond Bart explains exactly what’s going on with the Security Certificate hacking débâcle (think much much more than Digitnotar being hacked.)

Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday September 18th, 2011 and this is show number 330.
Schoche Boom Can Giveaway
 I really blew it last week. In Rod Simmons review of the Scoche Boom Can, he told us we get to have a giveaway for one. I totally forgot about it though! So here’s the deal. I’ve decided to make the giveaway available to people who’s subscribe to the NosillaCast News. There’s a little form you fill out on the left sidebar at podfeet.com to subscribe, so it’s super easy. The other thing that’s super easy is UNSUBSCRIBING if you find it annoying. I hate things that let you in but like the roach motel won’t let you back out. The current subscribers to the NosillaCast News have already gotten the giveaway contest instructions, but if you subscribe now, I’ll send out another email in a few days so you get a chance to enter as well. Yes, I’m bribing you to subscribe.
I really blew it last week. In Rod Simmons review of the Scoche Boom Can, he told us we get to have a giveaway for one. I totally forgot about it though! So here’s the deal. I’ve decided to make the giveaway available to people who’s subscribe to the NosillaCast News. There’s a little form you fill out on the left sidebar at podfeet.com to subscribe, so it’s super easy. The other thing that’s super easy is UNSUBSCRIBING if you find it annoying. I hate things that let you in but like the roach motel won’t let you back out. The current subscribers to the NosillaCast News have already gotten the giveaway contest instructions, but if you subscribe now, I’ll send out another email in a few days so you get a chance to enter as well. Yes, I’m bribing you to subscribe.
To be fair to those who listen to the show a little later than right away, I’ll probably send out a couple reminders too. The contest will run through the 30th of September, so sign up as soon as you hear this message. The BIG advantage of subscribing to the NosillaCast News is that if something goes wrong – I get sick, my Web site were to get hacked (knock on wood), I win the lottery and give this all up – this is one of the best ways to get notified. Ok, so there’s Twitter and Facebook and Google+, but a direct mail is so much more personal, right?
Anyway, many thanks to Rod Simmons of the Simple Mobile Review podcast for pulling this giveaway together for the NosillaCastaways.
Podcast Awards
The 7th annual Podcast Award nominations are now open. If you’ve got a favorite podcast, and you’d like to nominate it for one of the Podcast Awards, tea on over to podcastawards.com, and choose the award category. There are 22 categories, like Education, Food and Drink, GLBT, Gaming, and even Technology. Over 1 Million people are expected to do nominations during the 15 days the nominations are open. Nominations close on September 30th, so make haste to get over there and nominate your favorite shows! Again, it’s at podcastawards.com.
Knightwise rebuttal
Knightwise got a lot of flack on Twitter for his comments last week about Lion not being good for power users, and he decided he needed to clarify his position. Not that he didn’t enjoy the healthy debate but he couldn’t resist getting back to his mic. Enjoy his unique style as he explains his position with batman, a toothbrush and a pink tutu.
George Take Your Mac back from Lion
Next up, George from Tulsa has some opinions on Knightwise crazy ideas, let’s hear his position.
Love Lion, or jumped ship with Knightwise who told us in show # 328 how he wiped Lion from his Air and replaced it with Linux Mint? Listen to MacGeekGab which has lately been filled with anguished reports of some pretty serious Lion problems?
As to Knightwise, I do have to wonder, “What was he thinking?” Many of Lion’s new features try to make systems work like iOS which depends on 100% solid state memory. Versioning, state saving, and boot app relaunch have to be written then read from disk. Works in iOS and its 100% solid state memory. Not so much on the original Air’s minimal system RAM and 4200 RPM, let’s go watch paint dry hard drive.
Lion sunk its claws into my wallet only because I couldn’t resist the new i5 Air and its much less glossy screen. Yes, it GeekBenchs more than twice as fast as my 11″ Core 2, but in my real world, real life, Lion system friction erases the new computer’s speed advantages. Since it isn’t possible to install Snow Leopard on my new Air, I’ve been working to reverse as many of Lion’s “deprovements” as I can.
On first start, I went straight to System Preferences and restored both normal scrolling and scroll bars. If I wanted an iPad, I wouldn’t have given mine away.
Washing out Lion’s dirty linen took longer and sadly I haven’t killed it all. I used Deeper.App to clean Lion’s linen from my logon screen. Thanks to Deeper, my logon screen is now a lovely photo onto which I added my name and phone number in big clear text, just in case some honest person finds my lost Air and wants to return it.  There’s lots more tweaks in Deeper, which is also available in versions for Snow Leopard back through Tiger. In many ways similar to Deeper, TinkerTools has been updated for Lion and provides access to otherwise hidden system settings.
There’s lots more tweaks in Deeper, which is also available in versions for Snow Leopard back through Tiger. In many ways similar to Deeper, TinkerTools has been updated for Lion and provides access to otherwise hidden system settings.
Then there’s the LionTweaks.App, written by a 16 year old Norwegian, and downloaded by the tens of thousands. 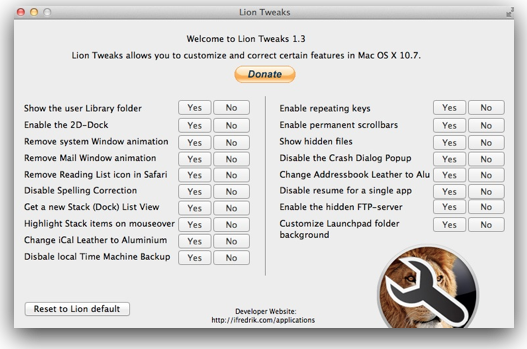 Every day brings more ways to make Lion less Lionesque. Now if someone would just bring back Quicken, Snow Leopard’s speed, and, please, oh, please, File > Save > As
Every day brings more ways to make Lion less Lionesque. Now if someone would just bring back Quicken, Snow Leopard’s speed, and, please, oh, please, File > Save > As
If Lion frustrates you, check the ongoing Lion Tips and Tweaks reports running in LifeHacker, Cult of Mac, and OsXDaily. They frequently tell of new ways to take your Mac back.
As always, links to everything in the Show Notes.
- Deeper is freeware, donations accepted, from the same developers who give us Onyx. Link to Deeper, Onyx, and Maintenance Downloads
- Lion Tweaks is also freeware, donations accepted Link to LionTweaks Download
- TinkerTool is freeware Link to TinkerTool Download
- Cult of Mac’s Lion Tips
- LifeHacker’s Lion Tips
- OsXDaily’s Lion Tips
- “Deprovements” first heard (at least, by me) from Steve Martin in an interview about Twitter and Technology with Leo Laporte. Steve Martin and Leo Laporte discuss software deprovements
- To change the Lion Logon Screen is easy. The image needs to be 72 dpi PNG sized to your screen as set in System Preferences > Display. Detail here: MacObserver on Changing Lion’s Linen and here: T3kd Blog on Changing Lion Login Screen
- How to choose your own background for Mission Control:
MacThemes Blog: How to Change Mission Control Background
Thanks for this George – great information as always!
ScreenSteps
I was listening to Mac Break Weekly this weekend with good friend Don McAllister from screencastsonline.com on the show. He was great as always. I got really excited when he did his pick of the week – he picked ScreenSteps! Don is the master of documentation, normally in video form, but like all of us he has to create written documentation to others from time to time as well. He described how he could do quick screen captures, much like you can with Skitch, but that the tool is built into ScreenSteps so it’s easy to annotate the images while plopping them right down into your documentation. He went on to explain that you can then put in the text explaining each step, and easily export to PDF, HTML, or even upload to their paid for ScreenSteps Live hosting if you get really into it. He described how if you get the Pro version for $80 you can do full manuals. If you don’t need that much horsepower, the $40 standard version lets you export to your own blog if you use WordPress, Movable Type, TypePad, SquareSpace, Blogger, Joomla or Drupal. That’s all of them isn’t it? If you don’t believe me after all this time, for sure you trust DON’S advice, right? You can go over and get a free trial of of ScreenSteps from bluemangolearning.com, but be sure to tell them you heard about it from ME, not Don…even if he does have that adorable British accent!
Motion GPS Drive for iOS
 Rod Simmons of the Simple Mobile Review podcast is back with a review of the Motion GPS Drive for iOS:
Rod Simmons of the Simple Mobile Review podcast is back with a review of the Motion GPS Drive for iOS:
Written review on simplemobilereview.com
Rod I can think of a PERFECT use for this app. Steve and I both have cars with built in GPS units so we don’t need Motion X GPS day to day. However we do travel for work fairly frequently, and drag a Garmin GPS unit with us along with the mount and charging cable. We always have our iPhones with us, so $2 for a month of GPS service is chump change for the couple times a year we would need it.
Smile
I’ve converted over to Lion even though a few of my applications aren’t completely functional yet. One of those applications is WireTap Studio from Ambrosia Software. WireTap Studio is designed to allow you to create a recording of two different sources, and keep them as separate tracks during editing, and do non-destructive editing when you’re done. The problem in Lion is that it won’t let you record a specific application, like say Skype, you have to choose “Mac Audio”, which means it records all sounds coming out of your Mac. This works ok for me, I record Mac Audio on one channel and my microphone on the other. The only problem is that I have to make sure any application that could possibly make noise during the recording is shut off. That means no checking Twitter, or email, or AIM when I’m supposed to be paying attention in an interview.
Why am I telling you all of this? Well because it wasn’t until I was using WireTap Studio in Lion that I realized how much I use TextExpander. I can’t type hardly ANYTHING while I’m supposed to be paying attention! I can’t even respond on Google+ for entertainment. let me explain. In just this short paragraph, I’ve expanded w t s ; to WireTap Studio four times, t e ; to TextExpander twice, and g p ; to Google+ twice. I realized I use TextExpander CONSTANTLY when I’m typing! It’s second nature to me now, it’s just like typing the real word to use the snippets. Let’s check my stats – since January I’ve expanded 7763 snippets saving me over ELEVEN HOURS of typing! They’ve got a free trial over at smilesoftware.com (that was a snippet by the way including all the wrapped around html), and when you’re ready to buy, it’s only $34.95. If you’re REALLY lazy you can just click on the big Smile icon in the left sidebar over on podfeet.com! Be sure to tell them you heard about it on the NosillaCast ok? ( NosillaCast is a snippet too, as is NosillaCastaways…)
Chit Chat Across the Pond
Security Light
- Last Tuesday was Patch Tuesday – MS released 5 updates (all rated Important) covering Windows (all current versions XP→7), & Office (Mac & Windows versions:http://technet.microsoft.com/en-us/security/bulletin/ms11-sep
- Adobe released critical updates for Actobat & Reader on all platforms (also on Tuesday):http://www.adobe.com/support/security/bulletins/apsb11-24.html
Main Topic – (Security Medium) DigiNotar in the Bigger Picture
Some developments since we last spoke about the DigiNotar hack:
- As expected, what we’d heard two weeks ago was just the tip of the iceberg, it was a LOT worse than just one Google Cert
- Hundreds of certs were issued, many to big names, and some very frightening wild-card certs, like *.*.com.
- The hack happened months ago, and DigiNotar KNEW ABOUT IT, but KEPT SILENT, all they did was quietly add some (perhaps all but not sure) of the serial numbers of the fraudulent certs to their revocation list
- The hacker responsible released some statements online, with proof that he is that hacker (an exe file signed with DigiNotar’s private key), saying that he’s also hacked other top-tier CAs, only naming one, Global Sign. This is the same hacker who hacked Comodo a few months ago, and generated 9 fraudulent certs there, which were all revoked. (Comodo, unlike DigiNotar disclosed responsibly, so browsers were patched promptly, and they were not booted from the trusted list by the browser manufacturers)
- When Global Sign were named, they voluntarily suspended the signing of all certs, and called in the same forensics experts who were investigating the DigiNotar hack. Their conclusion is that some of their servers were breached, but that no fraudulent certs were signed. They are now helping other CAs check their systems.
- Firefox have issued another update, their first update surgically removed only some of DigiNotar’s trust, the idea being to protect people without inconveniencing more site owners than needed – when t became clear DigiNotar had known for weeks and kept silent, FireFox released the second update (6.0.2 & 3.6.22) to fully strip DigiNotar trust, making it clear this was not a temporary suspension
- Apple finally lurched into action, releasing Security Update 2011-005 for Snow Leopard & Lion, but NOT for Leopard – 10.5 is now dead, if you’re still using it, you need to move NOW!
- Apple have NOT patched iOS, so all iPhones, iPads and iPod Touches are still vulnerable to fraudulent certs, and SSL/HTTPS cannot be trusted on iOS – you cannot safely bank etc till Apple get their finger out on this one. The only small ray of light is that iOS5 will make small patches like this easier, and hopefully, that will help Apple be more responsive. With iOS 4 each update has to come in the form of an entire new OS, a big download, while in iOS 5 OS X-style delta updates will be possible
This incident serves to highlight the serious challenges facing SSL/TLS (Secure Socket Layer/Transport Layer Security), and the many protocols that rely on it, including HTTPS, secure email, and SSL-based VPNs. The internet is fundamentally insecure at the lower levels, everything from ARP up, including IP, TCP, and DNS, is fundamentally insecure by design (well, by lack of design really). We rely on SSL/TLS to add a layer of security on top of these insecure foundations. SSL/TLS is supposed to give us three things:
1) confidentiality (no eaves droppers can see what we send)
2) integrity (no eaves dropper can alter the data we send)
3) authenticity (we can be confident that we are talking to who we think we are talking to)
All three of these things depend on the assumption that CertificatAuthorities (CAs) are secure and trustworthy, when that assumption fails, all three of those thing are lost, meaning attacker can see and edit supposedly secure data streams, and that attackers can impersonate others, tricking us into sharing confidential data with them.
We’ve known for a while that CAs are not perfectly secure, this is, after all, impossible, noting is perfectly secure. As the Comodo hacks showed though, with proper disclosure, we can work around security glitches at CAs. What we can’t work around is failures in trust. DigiNotar breached our trust by keeping the breach secret, and endangered the lives of literally hundreds of thousands of Iranians, and have done un-told other damage too.
Any one CA behaving in an untrustworthy way breaks the entire system, there are hundreds of root CA certificates in our browser’s trusted key stores, and a failure at any one of those organisations allows fraudulent Certs to be issued for ANYTHING.
Fundamentally there are three problems:
1) there are too many CAs to supervise them all properly
2) there is not enough oversight over security practices at CAs around the world to ensure their security
3) there is not enough oversight of the behaviour of CAs around the world to ensure their honesty
What is being done to address these risks?
One of the biggest responses to the on-going issues with SSL is the so-called SSL Observatory which is being run by the EFF (http://www.eff.org/observatory). They are storing copies of all the certs they see in use on the internet, and building up a searchable database. This is a great resource for spotting problems, and for monitoring the prevalence of bad certs.
How can we protect ourselves?
Firstly, the system, was designed with the possibility of bad certs from the start, so there is provision for the ‘revocation’ of certificates. There is a field within every cert where the CA can include the URL to a validation server which they control. Validation servers use the Online Certificate Status Protocol (OCSP) to answer queries from browsers as to whether or not a given cert should be trusted, or whether it has been ‘revoked’.
Secondly, CAs can run a website which lists all their revoked certs, this is called a ‘revocation list’.
Most modern browsers make at least some attempt to verify certificates:
FireFox – checks certs over OSCP if the cert specifies a server, and provides an interface for users to manually add URLs to revocation lists the browser should respect
Chrome – checks certs, but the interface is not explicit about HOW it checks them. It does not provide the ability to specify your own revocation lists
Safari – does not expose an UI describing certificate validation, or letting you control it, so no idea! (yet another reason why no one who cares about security should use it)
IE – no idea, don’t have a Windows machine to check!
Some very important Caveats:
1) OCSP URLs in certificates are OPTIONAL, so fraudulent certs are very unlikely to contain them
2) If a browser fails to contact an OCSP server, the default is to ‘fail open’ – certs which can be proven to be bad will not be trusted, but certs where no answer can be found one-way or another will be trusted
3) if a browser does use revocation lists, and it fails to contact the servers that host those lists, the browsers also tend to fail open
All this means that the protection offered to us by browsers by default is quite poor.
On FF there are secret hidden settings in about:config that will let you change FF to ‘fail closed’, and you can manually add revocation lists for all the hundreds of CAs, but this is not for the faint-hearted, and takes a lot of time and effort.
A complimentary approach to OCSP and revocation lists is to simply watch the certs your browser uses and look for unusual changes. SSL Certs do not change often. They last for a few years, and cost money, so organisations rarely replace then before they expire, and when they do replace them, they usually replace them with updated certs from the same CA.
This means that a cert changing before it expires, or changing CA is suspicious, and very likely to indicate a fraudulent certificate.
You could, if you had too much time on your hands, watch the details of the certs on all the important secure sites you use yourself, and keep a list of the expiration dates and CAs of those certs written down somewhere. Then, each time you visit your bank you could verify that the cert has not changed. This is utterly impractical, but help is at hand in the form of a FireFox plugin!
Certificate Patrol tracks all the certs it sees at all the servers you visit, and checks each time to see if they have changed unexpectedly, if they have, it pops up a warning!
https://addons.mozilla.org/en-US/firefox/addon/certificate-patrol/
If you’re the curious type you can also set it to pop up ALL certificate changes, not just suspicious ones, but that’s not advisable for regular people.
I was not able to find a similar plugin for Chrome or Safari 🙁
That’s going to wind this up for this week, many thanks to our sponsors for helping to pay the bills: ScreenSteps, and Smile. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter at twitter.com/podfeet. I contribute a fair amount over on Google Plus nowadays so just search for me by name if you want to circle me up. If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.

Is there a download-link to the podcast?
I just checked and am happy to report the .nz TLD will be fully DNSSEC enabled by December 31st, 2011. Yay!
Downloads are through the iTunes link.
When using IE8, the embedded player does not work and there is no download link. When visiting the page from a mobile browser, like opera mini on the blackberry, a download link is available. What I ended up doing was inspecting the HTML of the page, finding the address of the mp3 file, and pasting that address into the address bar of my browser.
It would be helpful to have a simple download link apart from iTunes since not everyone has access to that.