The management at my work often brings up the topic of training. While for many years it was a hollow promise, in recent years there has been a real push on staff to take training courses, and not just those directly relevant to their current roles. Anything that is relevant to our company is considered a good investment.
A colleague of mine had been stumbling his way through building PHP web front ends to various functions we normally just ran through terminal windows. He recently went through an online course in PHP web development, and so that got me to thinking what I might like to try.
My first thought was an iOS development course, to solidify my own learnings, but it turns out that a decent course that I feel would be worthwhile is very expensive and I know that management’s enthusiasm won’t stretch that far.
A few years ago, Allison encouraged me to look at Lynda.com, who offer many courses in business, IT, software development, media production, design and more. More recently I discovered that I can get free access to all of the courses through my local library membership. Late in 2017, I was looking around for something very specific – I forget what – when something else caught my eye.
 At the top of the page, there were featured “Learning Paths,” one of which was titled “Become an IT Security Specialist.” I’ve been listening to Bart and Allison’s Security Bits segments for many years now and I always find them interesting, but also often don’t keep up with all of it. So, I thought, why not give this a crack, as it most certainly applies to my own job, as well as being of wider value in the business.
At the top of the page, there were featured “Learning Paths,” one of which was titled “Become an IT Security Specialist.” I’ve been listening to Bart and Allison’s Security Bits segments for many years now and I always find them interesting, but also often don’t keep up with all of it. So, I thought, why not give this a crack, as it most certainly applies to my own job, as well as being of wider value in the business.
At the beginning of the year, I started spending two mornings a week going through the course material, which is comprised of 11 separate courses. This involves watching a lot of video material – 21 hours in all – and taking notes where interesting, useful, or new concepts are discussed. But this segment is not a review of security training, nor of Lynda.com.
One of the early courses spent a lot of time on security frameworks for businesses. These are comprehensive, structured guides to all the aspects of modern information security and go by names like NIST SP800-53, and the ISO 27000 series. In the example sections from these frameworks, I found many familiar concepts that have been discussed in Security Bits on this very podcast. It soon became apparent that a full knowledge and understanding of one of these standards would be a significant undertaking, let alone having to implement one in a business, but there was one topic that addressed this very issue, and it is this which I want to bring to your attention.
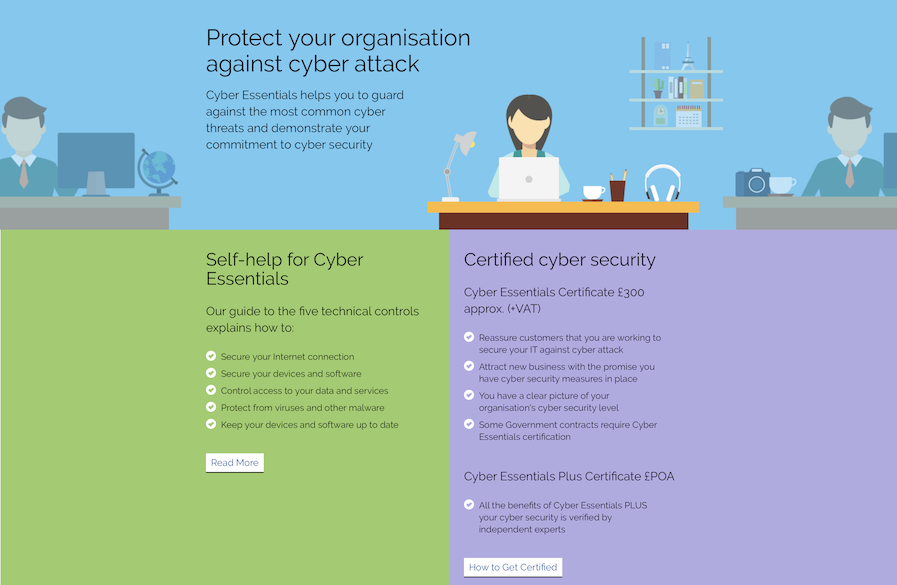
 Cyber Essentials is an initiative from the National Cyber Security Centre, the NCSC, of the government of the United Kingdom, specifically designed to be easy for small businesses to follow while helping guard them against the most common cyber threats. I checked out the website at cyberessentials.ncsc.gov.uk and I immediately saw the value in it.
Cyber Essentials is an initiative from the National Cyber Security Centre, the NCSC, of the government of the United Kingdom, specifically designed to be easy for small businesses to follow while helping guard them against the most common cyber threats. I checked out the website at cyberessentials.ncsc.gov.uk and I immediately saw the value in it.
Cyber Essentials covers just five requirements, each of which is easily described in a sentence. Those requirements are
- that you use and configure a firewall to protect all your devices, particularly those that connect to public or other untrusted Wi-Fi networks.
- that only necessary software, accounts and apps are used.
- that you control access to your data through user accounts, that administration privileges are only given to those that need them, and that what an administrator can do with those accounts is controlled.
- that you implement an approach to protect your devices against malware.
- that you keep your devices, software and apps up to date.
The website gives more information on each of these, including specific actions, yet is written in quite plain language and the whole thing can be consumed in a few minutes’ reading time. Much of it you will have heard before from Bart and Allison, and some of it is just common sense to the geeks among us, but it provides a useful, comprehensive check-list of the essentials and I think it would be a good idea to apply it in your home.
I encourage you to have a read of the site – it most certainly does not belong in the propellor beanie section – and if you know someone who runs a small business, why not ask them if they’ve really thought about their information security and point them there, too.
Once again, that’s cyberessebntials.ncsc.gov.uk. Bookmark it now.