Feedback & Followups
- Last time Bart & Allison waxed lyrical about the DART mission, but we didn’t know yet if it had worked, now we do, it did 😀 — www.nasa.gov/…
- The Matter home automation standard has been released to developers — appleinsider.com/…
Deep Dive 1 — VPN Leaks on Android & iOS
TL;DR no real risk to users.
Two stories broke this week that are being described as bugs or vulnerabilities, but are actually neither, they are intentional tradeoffs. Both involve traffic not being routed through VPN apps on mobile OSes.
Firstly, there is Android bypassing VPNs for its captive portal wifi checks, and secondly there is Apple communicating directly with its own servers on iOS.
On the one hand the Android example seems pretty cut-and-dried to me, there exist wifi networks that force you to go to a web page to log in or to accept terms and conditions before you can use the network. If you use a browser these networks will redirect every URL to their landing page, but if you use an app of some sort that’s not possible, so the connection appears broken. To avoid this Android & iOS added an OS feature that tries to phone home, and if it gets intercepted, it opens a browser pane to allow the users to log in regardless of the app they tried to use. This makes the user experience on these so-called captive portal networks infinitely better.
For the check to work reliably Google bypass VPNs to do it, and that’s the ‘flaw’ that made the news. Note that iOS probably does this too, but that hasn’t been reported, so don’t take that as gospel. The only reason there is even a tiny bit of legitimate criticism IMO is that Google have a setting labeled ‘Block connections without VPN’, and the captive portal check happens even when that’s enabled. Either Google need to add some small print, or disable the check when that setting is on, and then they’ve done everything perfectly IMO.
On iOS meanwhile, some encrypted traffic from iOS to Apple servers bypasses VPNs. Apple haven’t said why, but it’s most likely a decision rather than a bug. All the traffic is from Apple apps to Apple servers, and most of it is very confidential (with the exception of Clips!).
Two possible reasons come to mind:
- Security — Apple make a lot of privacy claims, so it makes sense to ensure that data never leaves Apple’s control, Apple securely handle it every step of the way from phone to server, avoiding handing it over to third-party apps.
- Efficiency — VPNs are inherently slower since they add a wrapping layer and re-route data.
Like in the Google case, there is no real risk to end users here.
Remember, like NAT routers were not designed to act as firewalls, VPNs were not designed as privacy tools. NAT routers’ actual job is to facilitate the sharing of a single IPv4 IP by many devices, and a byproduct of that one-to-many relationship is that unless the router has been explicitly configured to route all incoming connections to a specific device, the router can’t deliver incoming connections, so it drops them. VPNs are encrypted network interfaces that traffic can be routed through. If you choose to route all traffic through them, then you can hide all your network traffic inside them, but that’s just one possible configuration, and actually, a lot less common than most users think. Corporate VPNs only route traffic to the corporation through the tunnel, and most VPNs sold as privacy VPNs make exceptions for LAN traffic so file shares and printers keep working. Apple and Google are choosing not to route some OS traffic through VPN interfaces. That’s not a bug, it’s just a choice some don’t like.
Deep Dive 2 — Bart Gets (Temporarily) Duped by Smishing
TL,DR remember SMS senders can be faked!
Allison makes the point that none of us, no matter how informed we are, or how hard we try, are immune to scams. Allison has shared some stories about how she fell for things, and now it’s my turn!
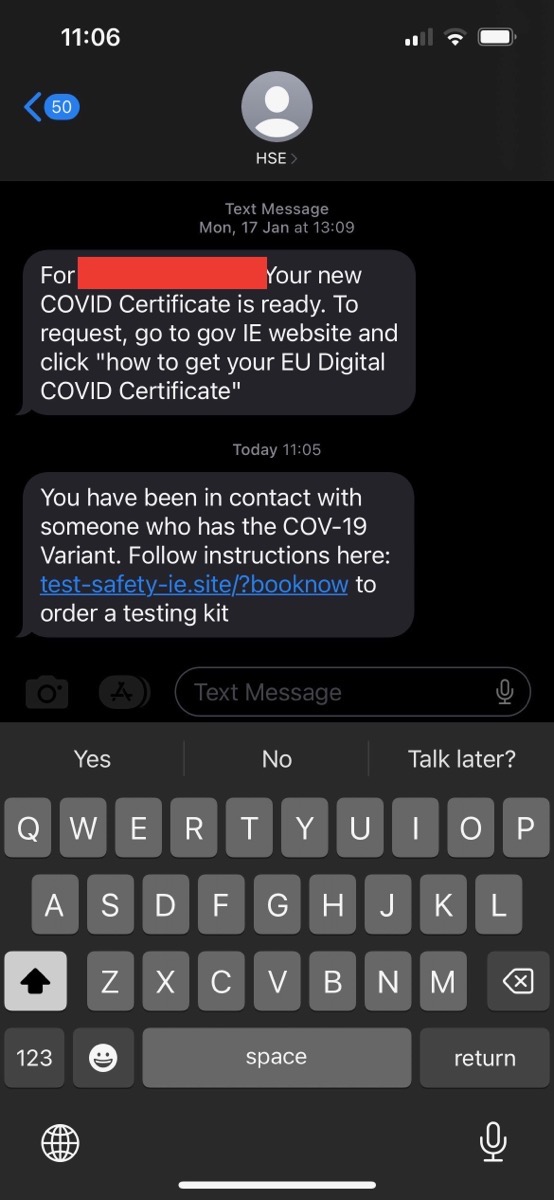
My darling beloved got an SMS message today that appeared in his phone as if it had been sent by Ireland’s national health authority, the HSE, that claimed to be a COVID exposure notification:
Intellectually I know the from number of an SMS message can be faked. I know that just because something appears to be from my bank doesn’t mean it is. I also know that when an SMS sender is faked smartphones will group it into an existing thread if there is one on the device, so the fake message will appear in line with real ones.
I know this, but when my darling beloved sent me the above screenshot I fell for it hook-line-and-sinker. I’ve obscured the PII, but the first message in the thread is 100% legitimate, and it had the correct name and age, but the second message was not. Because the PII was in the thread, the whole thing felt legitimate, and because it was a terrifying topic, the analytical part of my brain was off!
Had my logical brain been functioning, it would have picked this up as a scam immediately for 2 reasons:
- The domain name ends in
.ie.site, the HSE has a real.iedomain, it does not use a pretend one under the generic.siteTLD! - Exposure notifications are via push notifications, not SMS messages!
There is only one reason neither of us clicked the link — we’d picked up 20 COVID tests last week because I was legitimately a close contact of an actual case and had been testing daily for the past 7 days to play it safe (so far so negative, so 🤞). Once I stopped to think I noticed the domain, and when I pointed it out we both laughed about how naive we’d been, but the bottom line remains, we’re both well-informed and vigilant, but we’re also both human, so the fooled us, at least for a while.
Links
- Android leaks some traffic even when ‘Always-on VPN’ is enabled — www.bleepingcomputer.com/…
- Most Apple apps on iOS 16 bypass VPN connections — appleinsider.com/…
❗ Action Alerts
- Patch Tuesday in brief – one 0-day fixed, but no patches for Exchange! — nakedsecurity.sophos.com/…
- iOS 16.0.3 & watchOS 9.0.2 updates arrive with bug & security fixes — appleinsider.com/…
Worthy Warnings
- One million Facebook users had passwords stolen by fake apps — appleinsider.com/… (Over 400 malicious apps with fake Log in with Facebook screens on iOS & Android)
- Toyota says about 296,000 pieces of customer info possibly leaked — www.reuters.com/… (T-Connect users: email addresses & customer numbers, but not names, phone numbers or credit card information)
- No More Security Updates for First-Generation Eero Devices — tidbits.com/… (Editorial by Bart: if you’re still using one of these routers, you should probably replace it ASAP!)
- 🇺🇸 PSA from CISA: Foreign Actors Likely to Use Information Manipulation Tactics for 2022 Midterm Elections — www.cisa.gov/… (PDF)
Notable News
- Mac MDM provider Jamf have released details of a Gatekeeper bypass they found in macOS which the responsibly disclosed to Apple who patched it in July — appleinsider.com/…
- 🇧🇷 🇮🇳 Instagram Expands Age Verification Program Backed by AI to Brazil and India — www.macobserver.com/…
- 🇺🇸 Former Uber CSO convicted of covering up megabreach back in 2016 — nakedsecurity.sophos.com/… (Sentencing hearing to come)
Top Tips
- Some simple practical advice from the SANS Internet Storm Center: What is in your Infosec Calendar? — isc.sans.edu/…
Excellent Explainers
Interesting Insights
- 🇺🇸 Disturbing reporting from Brian Krebs about how Zelle is being added to users account by US banks, and how those same banks are failing to pay back money their customers lose to Zelle-based frauds, which are rampant: Report: Big U.S. Banks Are Stiffing Account Takeover Victims — krebsonsecurity.com/…
Palate Cleansers
- The best Ada Lovelace Day article I read: Move over Patch Tuesday – it’s Ada Lovelace Day! — nakedsecurity.sophos.com/…
- 🎧 Special life episode of a podcast Bart’s recommended before: Lazarus Heist live — overcast.fm/…
Legend
When the textual description of a link is part of the link it is the title of the page being linked to, when the text describing a link is not part of the link it is a description written by Bart.
| Emoji | Meaning |
|---|---|
| 🎧 | A link to audio content, probably a podcast. |
| ❗ | A call to action. |
| flag | The story is particularly relevant to people living in a specific country, or, the organisation the story is about is affiliated with the government of a specific country. |
| 📊 | A link to graphical content, probably a chart, graph, or diagram. |
| 🧯 | A story that has been over-hyped in the media, or, “no need to light your hair on fire” 🙂 |
| 💵 | A link to an article behind a paywall. |
| 📌 | A pinned story, i.e. one to keep an eye on that’s likely to develop into something significant in the future. |
| 🎩 | A tip of the hat to thank a member of the community for bringing the story to our attention. |

