I’d like to tell you about a magical application/service that solves a problem most of us have. I’m using it to solve a problem that is perhaps off of the beaten path but still within the realm of a NosillaCastaway.
The mainstream problem to be solved is that you’re away from home and you want to access some data that’s on your network at home. The more advanced problem I’m trying to solve is how to get my new Synology network attached storage to sync over the Internet to my old Synology which will be living at my buddy Ron’s house 1.5 miles away.
A third problem that could be solved is how to easily screenshare into your loved one’s computer across the Internet without them having to do any extra work.
The solution to all of these problems is a free service called Tailscale from tailscale.com/….
What is Tailscale?
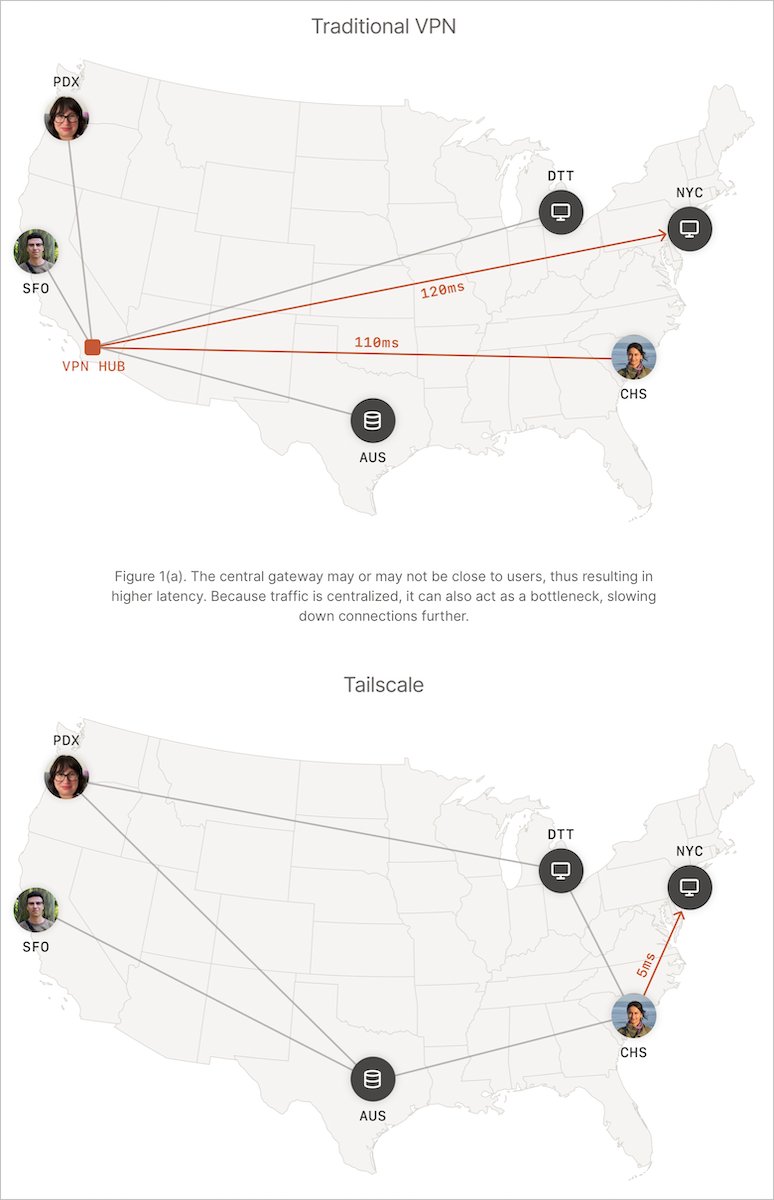
Tailscale at its core is a virtual private network mesh based on the Wireguard communications protocol. Wireguard is an open source protocol that is at the heart of many VPNs, and one of the options in my current VPN, Private Internet Access (my referral link to PIA).
You’re wondering at this moment why I’m recommending a VPN called Tailscale when I just said that PIA is my current VPN. These two applications solve very different problems and yet overlap in some ways.
A traditional VPN like PIA is designed to allow you to protect your traffic from prying eyes but routing all of that traffic through a hosted VPN server. You can obfuscate your country of origin and also obfuscate what data you’re transmitting and receiving.
Tailscale provides a virtual private network of a completely different sort. Let me explain by example. Let’s say you have a desktop Mac at home and you use an iPad or even just an iPhone when you’re on vacation. If you install Tailscale on both the Mac and iOS device, the two devices will be made part of a virtual private network without routing traffic through a third-party server.
I entitled this article “Tailscale is Magical” because that’s how it feels, and it is magically easy to set up. Now that I’ve got your attention, let’s talk about the Tailscale business model. After that, we’ll walk through how you install Tailscale and how you access different devices across the network.
Pricing
Tailscale follows the freemium model. For free, you can, as an individual user, use Tailscale to connect 20 devices on a virtual private network. If you have a small team of people who need to access the same devices over the Internet, for $5 per user per month you can get 5 devices per user. Bigger teams can get 10 devices per user for $15 per user per month and enterprises can get even more. https://tailscale.com/pricing/
The number of devices isn’t the only distinction between the plans. As you work up into the paid plans you can use access control lists and other integrations that are beyond the scope of this discussion.
Now that we know they don’t follow the Freepi model, a term coined by Bart to describe free services that then sell your data, let’s get into the fun part of running Tailscale.
Installation
Tailscale is cross-platform in the most complete sense. They have clients for macOS, iOS, Windows, Linux, and Android. Yes, everyone gets to play.
macOS and iOS clients are in their respective App Stores. Android users scan a barcode from the Tailscale website, Windows users download from the web, and Linux is installed using the curl command.
You can also install Tailscale on a Synology from the Package Center, which is like an App Store except everything I’ve seen in there has been free.
macOS Installation
When you first launch Tailscale on the Mac, it asks for your permission to allow VPN configurations. Next Tailscale will then ask permission to add its VPN configuration.
You’ll be prompted through the Tailscale website to log in and you can choose a Google login, Microsoft, or GitHub.
After the installation, you’ll be shown your admin console in a web interface where you can see your Mac listed as being part of the VPN mesh. The real fun begins when you add a second device to Tailscale. Without more devices, your first device is just sitting on this isolated island with no one to talk to.
iOS/iPadOS Installation
Installation on an iPhone or iPad is just as simple. Download Tailscale from the app store, and the first time you open it, it asks to install the VPN configuration profile just like it did on the Mac. Authenticate with your passcode for your device and it launches Tailscale.
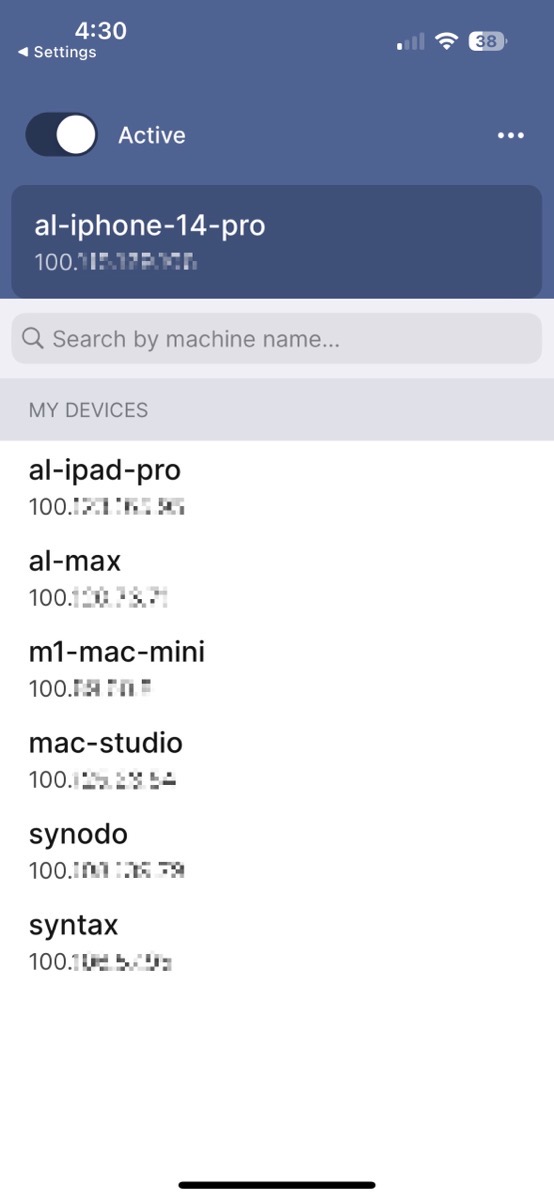
Now things get exciting. Tailscale on iOS shows you a list of devices that are part of your little VPN mesh. For each device, you can see the IP address that has been assigned by the VPN. My home network is the classic 192.168.x.x, but I can see my devices all starting with 100.x.x.x.
All of the devices in the VPN mesh created by Tailscale are living on two networks simultaneously. When you’re away from home, the devices on the VPN mesh will be able to talk to each other even though you’re on a different network. But we’ll get to how to do that shortly.
I have to take a side step here to tell you about one of my favorite things about Tailscale. It creates what it calls MagicDNS. To refresh everyone’s memory, DNS stands for the Domain Name System and at its most basic level, it’s what lets you type podfeet.com into your browser instead of my server’s IP address 172.67.199.198.
MagicDNS from Tailscale creates a mapping between the name of your device and the IP address Tailscale has given to that device. For example, my MacBook Pro is called Al Max in System Preferences → Sharing → Computer Name. Tailscale’s MagicDNS has created an entry for al-max to be a specific IP on my VPN mesh network.
You’re probably asking why you would care about this MagicDNS thing. For one thing, the list of devices in the Tailscale app has real names and IPs so it’s super easy to see which device is which.
But again, why do you need this at all? If you ever need to connect to one of your devices via its IP address, now you don’t need to remember the number, you can just remember its name.
I haven’t talked about how to install Tailscale on a Synology but it’s just as easy as it is on a Mac. You install the Package, open it, authenticate, and now the Synology is on the Tailscale VPN mesh network. My Synology’s name is Syntax, so now I can access the web interface of my Synology by simply entering http://syntax into the URL bar. Pretty dang cool.
Using Tailscale with Anger
How would this be helpful to an iPad or iPhone user in the real world? Let’s say you’re on a beach in the Seychelles having closed a deal to buy a house right before you left on vacation. You get a frantic text from your realtor telling you that you forgot to email her one last critical piece of information. The file is on your desktop at home and all you have with you is your iOS device.
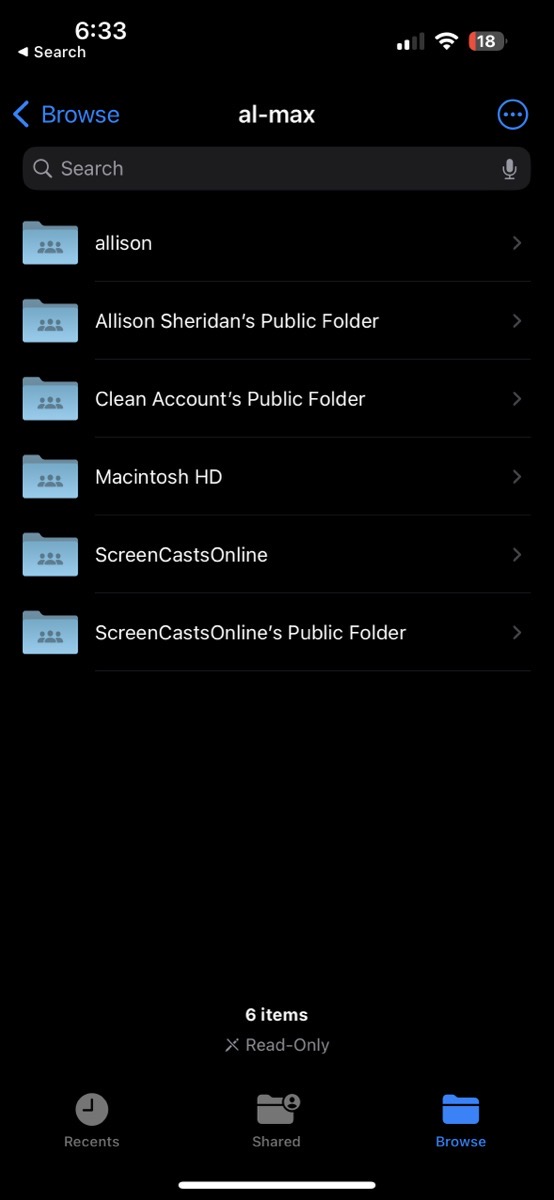
No problem at all. Your iPhone or iPad are both on the Tailscale mesh network and so is your Mac. Open the Files app, and when you’re in Browse, there’s a three-dot menu in the upper right. In that menu is an option to Connect to Server. Simply type the MagicDNS name of your Mac. You’ll be asked to authenticate to your Mac with your normal login, and you can navigate just like you’re in the Finder on your Mac using the Files app.
Seriously, it’s like magic. The next time you need to go to your Mac from your iOS device, your Mac will already be in a list of servers you can connect to and your credentials are already stored.
Let’s say you’re a bit nerdier — like yours truly — and you carry your laptop along on vacations. With Tailscale installed on your desktop Mac, you can access all of your files on the home Mac right from the Finder on your traveling Mac.
While on a different network you don’t see them in the left sidebar of the Finder window like you do when you’re at home. Instead, use the Go → Connect to Server menu from the Finder and type in the MagicDNS name. All your files are there.
Here’s yet another cool thing you can do with Tailscale. Let’s say you do tech support for a family member or friend. If they give you permission to run Tailscale on their computer, you can connect into their Mac using the built-in Screenshare app using just their devices’ MagicDNS name. Heck, you can screenshare into your own Macs if its in Tailscale.
Remember Ed Tobias’s story about his relative who almost lost a lot of money when she got scammed into giving a bad actor access to her Mac? I asked Ed whether Tailscale would be a good solution for him to be able to help her remotely and yet not have her be vulnerable. He and I did some experiments
I talked to Ed Tobias about whether this would be a way he could help his family member remotely without her being vulnerable to someone taking over her machine. He pointed out that if the scammer knew to ask if she was running Tailscale (by describing the icon in the menu bar), they could get her to open the admin console, and from there Tailscale allows you to share the connection to another Tailscale user.
It seemed that the developers of Tailscale would have thought of this potential attack vector and indeed they have. If you pay for your accounts for you and another user (at $5/month), then you have the ability to enable access controls. You can create users who do not have admin rights and therefore do not have the ability to open the admin console and grant access to anyone else.
In Ed’s case, his relative lives 20 minutes away and he’s often there anyway, so it wouldn’t be worth $10/month to him. But if you have remote users you need to help that are farther away, or you need a relatively inexpensive way to help clients, a paid Tailscale account might be something to consider.
While Ed and I were chatting, he was talking about a web server he runs on a Raspberry Pi that he keeps isolated on his guest network. He can install Tailscale on the Raspberry Pi and on his Mac and now he’ll have easy access to it as it will be on his own virtual private network.
What About Other VPNs?
One question I had was how the use of Tailscale might affect my “regular” VPN software PIA. Would I no longer need PIA? Would the two VPNs conflict with each other? Maybe I would have to flip between the two depending on what I was trying to accomplish.
Unless I have a fundamental misunderstanding, which is altogether possible, you will run into problems if you try to run another VPN alongside Tailscale.
I ran some tests to see what would happen. On my Mac, I joined my guest network and turned on PIA while still running Tailscale. I made sure to enable split tunneling in PIA, the technology that allows you to still see inside your local network. I thought perhaps that would allow me to still see my Tailscale network but it didn’t work.
I tried the same thing on my iPad, but in Settings → VPN, it just toggled between the two VPNs. I could not simultaneously run both Tailscale and PIA.
While doing Internetty things on a WiFi network I don’t trust, I’ll continue to run my normal VPN, PIA. When I need to connect to my home network, I’ll disable PIA and enable Tailscale. I know the traffic to my home will be protected from prying eyes while I use Tailscale.
Menu Bar App on macOS
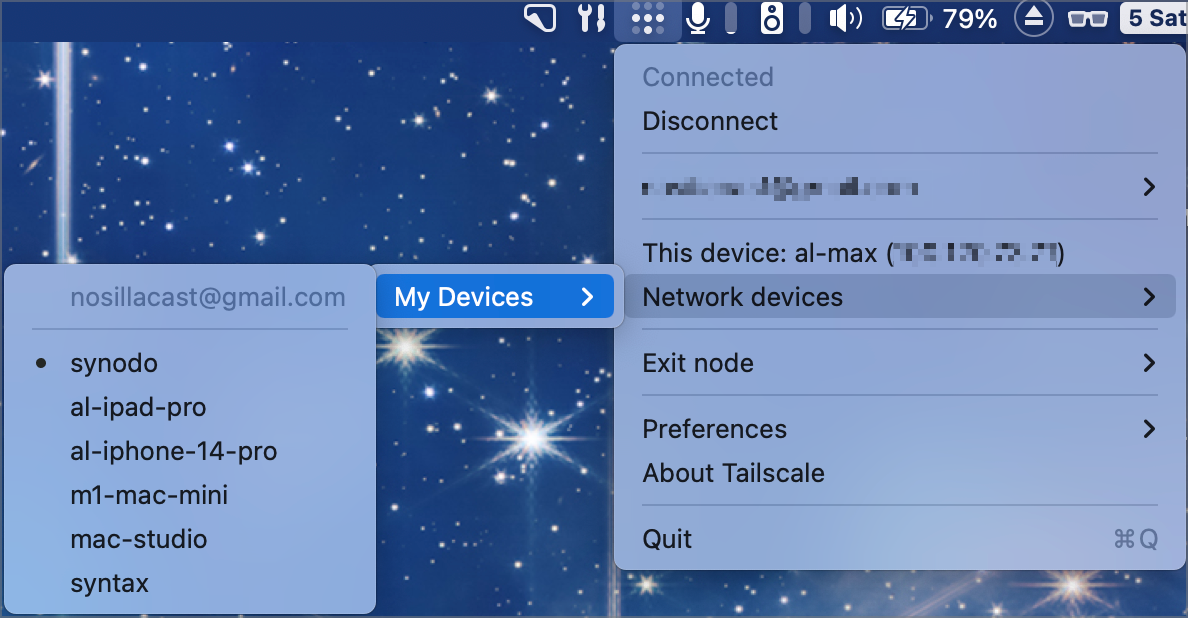
There are a few easy ways to get more information and maybe tailor your use of Tailscale. On the Mac, Tailscale installs as a menu bar app. In the dropdown, you can see your own devices’ Tailscale IP and you can see the MagicDNS names of all of your other Tailscale-enabled devices. If you select one of them in the list, it automatically copies the IP address to your clipboard.
From the Tailscale menu you can also select your login name and from there open the admin console. This is the web page I mentioned right after I explained how to install the app.
In the admin console, the machines tab shows you in a nice table all of the machines you have in Tailscale, along with their IP addresses, the OS they’re running, the version of Tailscale they’re running (and if it’s out of date you’ll see a warning to upgrade), and when the machine was last connected.
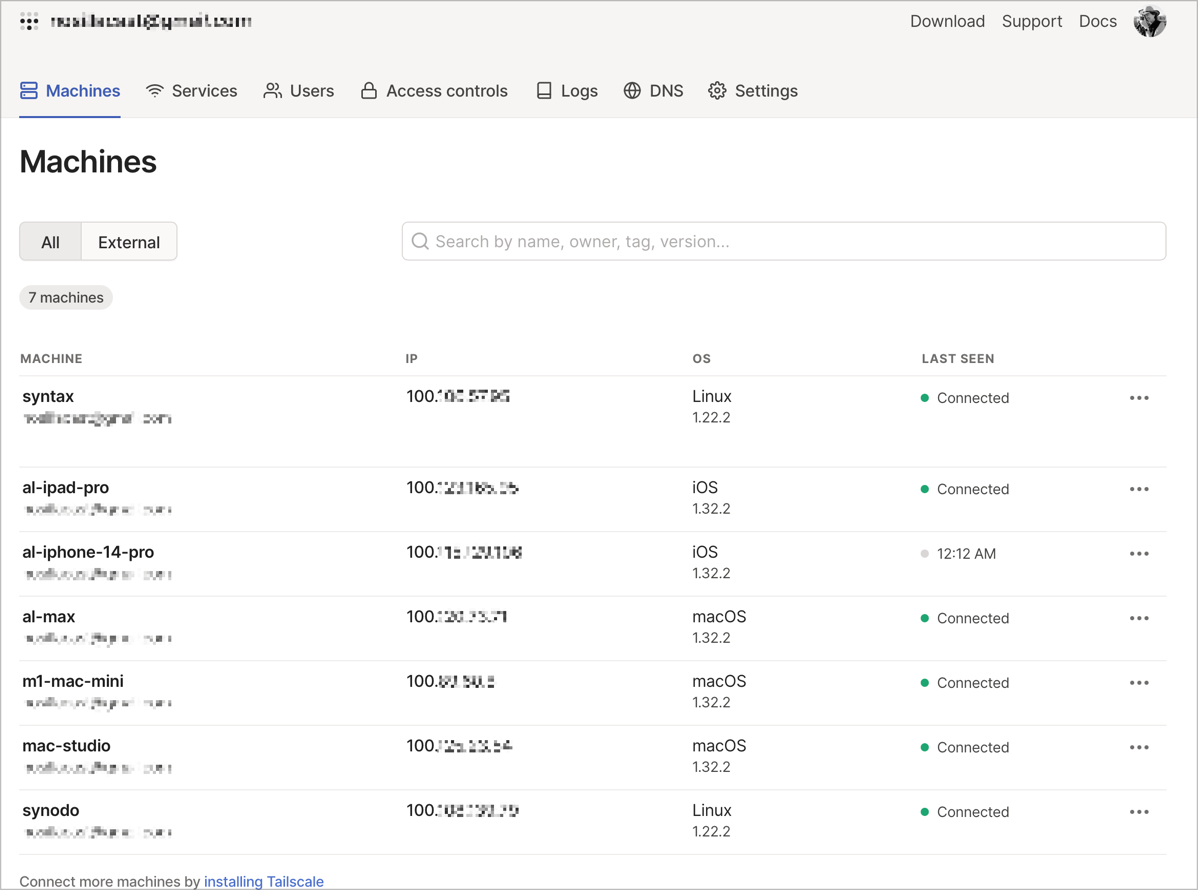
The admin console has a lot of features and most of them are beyond my skill set this early after learning to use it. I highly encourage you to poke around in the tabs of this interface if you want to learn more about what you can do with Tailscale.
The one item I haven’t learned how to use yet but intrigues me is the ability to designate one of your machines as an exit node. If I understand it correctly, I think it might allow you to treat Tailscale as a traditional VPN, using one of the devices in your network to act as a relay to the Internet. In the short amount of time I’ve had to play with Tailscale, I haven’t had time to figure out how to test this feature, but it sure sounds nifty.
Bottom Line
I hope I haven’t made this sound overly complex because it really is super easy to install and configure Tailscale. I had it running in less than 10 minutes after I decided to give it a try. I got curious about how it works and hope that you enjoyed knowing a little more about this free, magical technology.
If you think you might ever want to access data on a device you’ve left behind, or share a screen from a remote network, I highly recommend setting up Tailscale now so it’s ready for you when you need it. MagicDNS alone is worth the price of free even when you’re at home.
Check out Tailscale at tailscale.com/….


This sounds brilliant Alison. So many possibilities – I can give my sister a Mac Mini to run as a headless video streamer and admin it from 4 hours away.
Plus I can access my own devices from anywhere, and I have a lot of experimental stuff I’ve been playing with. It’s even available for the Raspberry Pi, but may have go on the back burner.
Thanks for bringing this to our attention.
Synology has a VPN package. Why not just set it up and VPN into your Synology?
Hi Allison,
Suppose I’m on vacation (again…:-)) in Antartica (say) and I want to Tailscale back to my desktop Mac at home. What conditions are necessary: must to be powered up seems like a must, must I be logged in, must the computer not be asleep, must the screen not be locked? What settings do I need so I can access my Mac from thousands of miles away when no one else is at home? I’ve been fighting with screen sharing when I’m home after surgery and I don’t wanna go upstairs to my desktop. Mac and I cannot keep it consistently accessible from my laptop. Anyways, I’d love to hear what you have to say about Tailscale in this real life situation.
Paul – sorry for the (very) detailed reply – I haven’t been getting notifications of comments from WordPress for ages!
I don’t know all of the conditions I’m afraid, but powered up would of course be mandatory. It’s a pretty light lift to install Tailscale on both Macs and give it a try under different conditions. I don’t have it installed on any local machines that go to sleep and such. Ping me directly if you want me to do some specific experiments.
By now I hope you’re recovered from surgery!