This week we’ve got the last two video interviews from CSUN Persons With Disabilities Expo. We’ve got RSLSteeper from RSLSteeper.com and Autismate from Autismate.com. In Dumb Question Corner, I show Steve Mandala how to record an Internet radio stream using Audio Hijack Pro from rogueamoeba.com. In Chit Chat Across the Pond we’re going to put the nerd beanies on pretty tight. First Bart walks through how to lock all of your preference panes, then we go full speed as Bart answers Ryan Sakamoto’s question on whether email is secure on our smart phones and how to digitally sign and encrypt your email with S/MIME.
![]()
mp3 download
Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday March 31, 2013 and this is show number 412. This week we’ve got the last two video interviews from CSUN Persons With Disabilities Expo. We’ve got RSLSteeper from RSLSteeper.com and Autismate from Autismate.com. In Dumb Question Corner, Steve Mandala asks me to write, or get someone to write him a script to record an Internet radio stream and I get him an even easier and better answer. In Chit Chat Across the Pond we’re going to put the nerd beanies on pretty tight. First Bart walks through how to lock all of your preference panes (and of course he made a Clarify tutorial on that). Then we go full speed as Bart answers what was SUPPOSED to be a Dumb Question Corner from Ryan Sakamoto on whether email is secure on your smart phone. Hang on for that one, but first I have to complain again about trying to watch television.
Watching TV
HBO
Rock of Ages
oh, it’s like TV, not on demand
what channel is HBO?
did a search using TiVo, found it on 398
turns out it’s in spanish
gave up
moved to Netflix
used Type2Phone
not avail on Neflix
switched to iTunes
Type2Phone stopped working
Can only buy, not rent.
Switch to Usual suspects
can only buy, not rent
switch to Amazon instant video via TiVo
Can rent
click rent
needed 5 digit pin
launch LastPass
found the PIN
Clicked pay
“Unsupported Format – this device cannot support the format requested”
Watched Dodgeball on DVD
Happy Mail
I got a letter this week that really made my day, and we thought you might enjoy hearing it. It’s from John Haller. He wrote:
Allison,
I was food shopping and listening to your podcast and you were ranting about the markings on a gadget which were a O and a vertical line you defined as “pipe.” This is a particular marking that I have been confused about about for years. I was so happy that I wasn’t alone. Some dumb person thought this was intuitive. He was wrong. My son’s always give me a hard time. Dad, can’t you remember? No Dammit.And then you referred to your Dad saying that additional car options were just “more things to go wrong.” I about fell over laughing. The other shoppers looked quizzically at me wondering what I was listening to. My Dad always said that about gadgets, and he had a point back in the 50’s. He was referring to air conditioning and power windows. Now I won’t buy a car without it, but I always evaluate an option with him in mind.
And then you ranted about cars and big trucks. I have a big truck and love it. And you little car people annoy me. I had to drive a small car for years until I could afford a real vehicle made in America. I accept your apology.
In any case, I am in awe of your skill in producing a podcast which moves effortlessly and is informative and entertaining. Your honesty in describing you abilities and lack of abilities is remarkable. Makes you very human and easy to relate to.
Ok, that last part was just self serving for me to read but I really enjoyed this entire letter. I wrote back to John and explained that he MUST be my long lost (older) brother, because my dad was ALSO talking about power door locks and windows when he used to say “just something else to go wrong.” I’m so glad he’s forgiven me for my comments about big trucks.
RSLsteeper
I’ve got two video interviews from CSUN Persons With Disabilities Expo. Last year I interviewed some folks who were working on a prototype of a device that would be plugged into an iPad, and which would tap into the VoiceOver controls and allow a mobility impaired person to use physical switches to control the iPad. That company didn’t come to production, but RSLSteeper did just that. I’ll play the audio for you here, and when you’re done listening you might want to head over to podfeet.com and watch the video.
Using a Screen Reader? click here
Autismate
At CSUN Persons With Disabilities Expo there are a lot of cool solutions for those with Autism, specifically using iPads. This device that most of us use for watching videos and checking email or doing important tasks like playing fruit ninja, can actually change the lives of those who haven’t been able to communicate before. It’s mind bending to see what a difference the ingenuity of developers combined with a “magical” device have done for families dealing with these challenges. Let’s listen to the folks from Autismate and hear about their applications. Again there’s a video that’s helpful to watch over on podfeet.com, but we’ll listen to the audio now:
Using a Screen Reader? click here
Dumb Question Corner
Steve Mandala wrote in with a question that wasn’t dumb at all, except I have a much easier answer than he asked for. Here’s his email:
Hi Allison, I love the show, I listen to it every week. I heard on one of your recent shows that you created an apple script to perform a certain task. I’m looking to do the following: Go to a certain website every weekday at 1 PM ET and record a radio station for 20 minutes only. Save the file so I can listen to it later in the day.
Can you or one of your talented listeners create a script like this or do a screen steps so I can create it myself. The website I would like to record is newyork.cbslocal.com/station/wfan/. This might sound strange but I like to listen to the opening of this sports talk radio show everyday but I’m not always available to have it on. Thanks for your help in advance.
My first instinct was to try to do it myself, but since I’ve successfully written one script, and I mostly copied stuff form other people and combined them cleverly, that would probably be a bad idea. Then I thought about trying trick Dorothy into doing it for Steve, but since I gave her an extensive assignment this week involving scripting and using a cronjob, that might not fly with her. The good news is that then I remembered there’s a super easy way to do this that doesn’t require any programming skills at all, just the purchase of one of my favorite applications from a great developer.
The application to solve all of this is Audio Hijack Pro from Rogue Amoeba. I use Audio Hijack Pro every week to help create the live show. This app allows you to “hijack” the audio from any application or hardware device, including system sounds. Once you’ve hijacked the audio, you can pipe it somewhere else. I won’t go into how complex my operation is after that, it would just scare you off. Let’s get to the problem Steve wants solved instead.
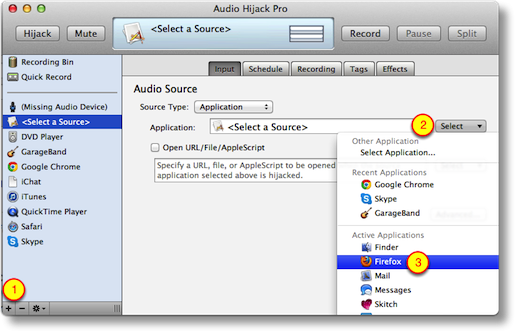 In Audio Hijack Pro like I said you can define an application, so in Steve’s case we’ll choose a web browser to hijack, say Firefox. On the left sidebar of the application, you click on the plus sign in the bottom left, which opens a new hijack source that says simply, “Select a Source” . If you click on the input tab, you get an option to choose the application.
In Audio Hijack Pro like I said you can define an application, so in Steve’s case we’ll choose a web browser to hijack, say Firefox. On the left sidebar of the application, you click on the plus sign in the bottom left, which opens a new hijack source that says simply, “Select a Source” . If you click on the input tab, you get an option to choose the application.
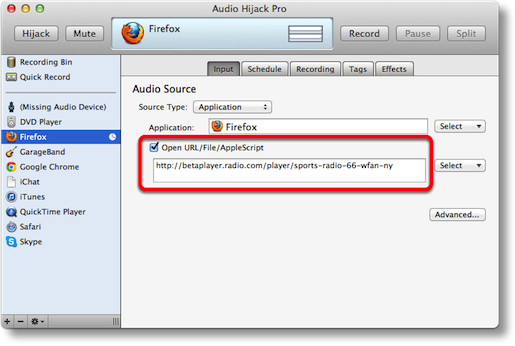 On that same page, there’s a check box to Open a URL/File/Applescript and after checking that box you can drop in the url to CBS Local that Steve wants. Now that’s all well and good to record NOW, but any dope could do that. The real magic is the next tab, which is called Schedule. In there it invites you to click the plus button to add a timer. The default is to be on, and to record from 10-11pm Monday through Friday. I think they do that so it’s real obvious how it works and how to change it. You can easily make it any day and time I want and set the duration.
On that same page, there’s a check box to Open a URL/File/Applescript and after checking that box you can drop in the url to CBS Local that Steve wants. Now that’s all well and good to record NOW, but any dope could do that. The real magic is the next tab, which is called Schedule. In there it invites you to click the plus button to add a timer. The default is to be on, and to record from 10-11pm Monday through Friday. I think they do that so it’s real obvious how it works and how to change it. You can easily make it any day and time I want and set the duration.
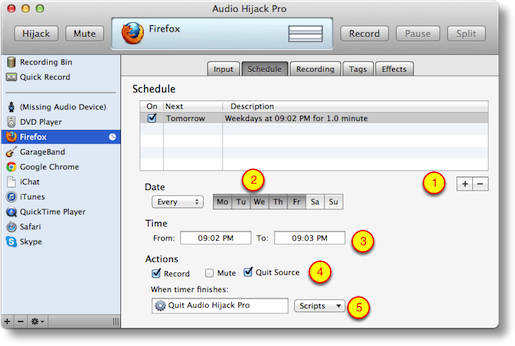
At the very bottom of that window there’s a section that says When Timer finishes: and it defaults to Do Nothing, but you can have it execute some scripts (which we don’t need) or we can set it with the pull down to actually quit Audio Hijack Pro. There’s also a checkbox above that to actually quit the source too, so it will quit Firefox when the recording is done.
 The next tab you care about is the Recording tab, and in there you can set the location for your saved files. You can also set the name of your recordings, and they nicely show you some options on how to name them with things like date and time markers. You can change the quality of the recordings as well; the default is a 128kbps stereo MP3 which is pretty good for most things, but if you’re either chintzy on space, or an audiophile, you might want to fiddle with those settings. There are a TON more options in Audio Hijack Pro, but I don’t want to scare you guys off with too many options.
The next tab you care about is the Recording tab, and in there you can set the location for your saved files. You can also set the name of your recordings, and they nicely show you some options on how to name them with things like date and time markers. You can change the quality of the recordings as well; the default is a 128kbps stereo MP3 which is pretty good for most things, but if you’re either chintzy on space, or an audiophile, you might want to fiddle with those settings. There are a TON more options in Audio Hijack Pro, but I don’t want to scare you guys off with too many options.
One thing I did notice is that Steve will have to get the full url that shows when you click the Listen Live button, which is actually http://betaplayer.radio.com/player/sports-radio-66-wfan-ny. I tested this out by quitting Firefox and setting the timer a few minutes ahead, and sure enough Audio Hijack Pro launched Firefox to the right url and started recording the audio stream. I tested to see if Audio Hijack Pro would launch itself at the prescribed time but that didn’t work, so it appears you do have to have Audio Hijack Pro running so that it’s waiting for the time to record. I suppose if you were clever, you could use the Automator Action I taught you last week to create a calendar event that simply launches Audio Hijack Pro so it’s got time to settle back into an easy chair and get ready to record on time.
Audio Hijack Pro is a grand total of $32 from rogueamoeba.com/audiohijackpro and if you can’t spell Amoeba there is of course a link in the fabulous shownotes. Unfortunately there’s not an app store version of Audio Hijack Pro, because this is just the kind of messing around between Apps that Apple is trying to protect us from now. I’m sure glad there’s still a way to use the interesting applications to solve interesting problems. I like the walled garden but I want a door in it for when I need to go out and play. I hope this answers your question Steve, and I bet you’ll find more and more fun things to do with Audio Hijack Pro.
Clarify
In Security Light coming up next, Bart will be answering what was supposed to be a dumb question about how to make sure preference panes stay locked when you close system preferences. Evidently it’s hidden pretty well, but Bart figured it out. What do you think he did after he figured it out? Well of course he created a tutorial using Clarify from BlueMango Learning. After he created the tutorial, he published it to his Evernote account. I knew you could do that to store the tutorial files, but next he did something I didn’t know you could do. Inside Evernote there’s a Share button that allows you to publish the tutorial to the web. The cool part about that method is that it also gives the Clarify document to people in case you want to share that so they can edit for their own use or to keep locally. It’s good to know it CAN do that but sometimes you don’t want to share your work for editing. If that’s the case, from within Clarify you can click the share button and it goes up to clarify-it.com but you’re just giving people the tutorial, not the Clarify document. I think it’s really cool that Bluemango Learning have created so many different ways you can post your content. If you want to buy Clarify, use the big Clarify logo on the left side of podfeet.com, or if you want to try before you buy, head on over to BlueMangoLearning.com and use their free 30 day trial.
Chit Chat Across the Pond
Followup Regarding Locking System Pref Panes
Last time we talked about locking down the ability to change the time on the Mac as a way of protecting against the sudo bug, and I said “just close the padlock and you’ll be grand” – but it seems that the padlock keeps defaulting back to open unless you change the default for all padlocks in syspref to closed. The option to do that is quite well hidden, so I created this Clarify tutorial on how to lock Preference Panes once and for all.: (thanks to Jim Sewell for the question about this)
Security Light
Important Security Updates:
- Apple release iOS 6.3 (http://support.apple.com/kb/HT5704) – patches two lock screen bypasses, but a new one has since surfaced, though it even more complex, and involves popping out the SIM at exactly the right moment and only affects people with Voice Control enabled from the lock screen: http://www.zdnet.com/apple-ios-6-1-3-fix-contains-another-lock-screen-bypass-flaw-7000012912/
- Apple release OS X 10.8.3 and Security Update 2013-001 – http://support.apple.com/kb/HT5672
- Apple surprise many by patching Safari on OS X 10.6 SnowLeopard – http://www.intego.com/mac-security-blog/apple-shocks-security-world-with-safari-5-1-8-for-snow-leopard/
- Apple release Apple TV 5.2.1 – http://support.apple.com/kb/HT5702
Important Security News:
- It’s been a good news bad news two weeks for Apple ID security – they had to take their iForgot password reset page offline because of a common coding error (http://www.imore.com/anatomy-apple-id-password-reset-exploit), but they also released two-factor auth. The setup process for two-factor auth gives users very clear information about the pros and cons of setting it up, and about how it will work, but I still found this how-to from TMO helpful: http://www.macobserver.com/tmo/article/how-to-enable-two-step-authentication-for-itunes-icloud
- A new Mac Trojan called Yontoo surfaces – Apple respond quickly by blocking it via XProtect – http://www.intego.com/mac-security-blog/apple-updates-xprotect-to-detect-yontoo-adware/
- An anonymous security researcher has mapped the internet using a ‘benign’ worm and discovered that a staggering number of devices on the internet have open telnet ports with default usernames and passwords. This gave the researcher access to millions of internet connected devices running Linux that could leveraged to spread the worm and continue the building up of the map. The worm was about as white-hat as you could make a worm – it didn’t brute-force passwords but just used a few common combinations (things like admin+admin or root+password). Once in the work scoped out the resources on the device, and only ‘infected’ it if it had enough resources that running the worm would be unlikely to kill it. After a certain amount of time the worm then deleted itself. The important take-home is that there are a staggering amount of devices on the internet that could be taken over by any botnet with only the tiniest of effort, and put to malicious use. These are mostly embedded devices that have not been explicitly configured to have telnet on, but have simply been plugged in with their default settings left intact. We are talking mostly things like routers and printers. What should you do about it? Simple – run the “Common Ports” Shields up Test on yourself (https://www.grc.com/shieldsup). If you see all stealth or closed next to the ports, you’re good (even if it says FAILED at the top). If you are interested in learning more Steve & Leo have a great discussion about this on Security Now Episode 396: http://www.grc.com/sn/sn-396.htm
- We need to stop advising people to hover over links to see where they go – that is REALLY easy to fake (http://nakedsecurity.sophos.com/2013/03/26/anatomy-of-a-feature-change-link-after-clicking/) – the best advice is still to get people to type in links in emails, and on the web in general, check the URL bar after you arrive, not before you click. It would be trivial for example to make a link look like it goes to PayPal but instead take you to another site that looks like PayPal to get you to enter your password. If you look before you click you will be hosed. If you look after you will spot the problem before you enter your details.
Suggested Reading:
- Facebook plugs another privacy hole (this one exposed things like political beliefs and sexual orientation by leaking the events users had attended despite having set that information as private) – http://nakedsecurity.sophos.com/2013/03/21/facebook-plugs-timeline-privacy-hole/
- A new tool underscores what has been known for a long time – Skype leaks your IP address to the world – http://krebsonsecurity.com/2013/03/privacy-101-skype-leaks-your-location/
- Google share as much information as they legally can (which is not a lot) about the US government’s spying activities on Google users – http://www.wired.com/threatlevel/2013/03/google-nsl-range/
- Security concerns over Samsung’s custom version of Android – http://threatpost.com/en_us/blogs/vulnerabilities-continue-weigh-down-samsung-android-phones-032013
- Microsoft does a U-turn with regard to Flash in IE10 in WindowsRT/8 – http://news.cnet.com/8301-1023_3-57573755-93/microsoft-backs-away-from-flash-ban-in-ie10/
Main Topic – Understanding Email
Dumb Q from Ryan Sakamoto:
“How secure is email on your iPhone or smart phone?
With people having access to their email 24/7 on their smart phone, what are the odds of a hacker grabbing any information from my iPhone?”
This deceptively simple question is actually very difficult to answer, and I think the best approach is to take some time to explain how email works, and the things you can do to protect yourself as much as possible.
Ultimately though, email is an inherently insecure medium – I like it to think of it as the digital equivalent of the postcard.
There are three protocols involved in sending and receiving email:
- SMTP (Simple Mail Transport Protocol) – this is the protocol used to send email both from your computer to a mail server, and from one mail server to another. This is the protocol used to transport email across the internet. It is OLD, having first been defined in an RFC back in 1982 – http://en.wikipedia.org/wiki/Simple_Mail_Transfer_Protocol
- POP3 (Post Office Protocol Version 3) – this is a protocol for downloading email from a mail server to a mail client. POP is also an old protocol, the first version dating from 1984, and POP3 from 1988 – http://en.wikipedia.org/wiki/Post_Office_Protocol. POP3 really should be obsolete by now, but quite a few people still user it. If you do, consider changing to IMAP.
- IMAP (Internet Message Access Protocol) – this protocol allows a mail client to access email messages stored on a remote server. If modern PR has been around when it was invented in 1986 (http://en.wikipedia.org/wiki/IMAP) it would have been called “cloud email”, because it gives a view into a “cloud” server rather than pulling messages down from the server to store them in a local email client. If you have more than one device that needs access to your email then IMAP is for you. In the modern connected world, IMAP really is for almost everyone!
The thing to notice about these three protocols is that they are OLD! They date back to the early days of the internet, and suffer from the same problem as all the venerable old internet protocols do, they were created in a more innocent age when security just wasn’t a consideration. Annoyingly, with the exception of Telnet which has now been mostly replace with SSH, most of these insecure-by-design protocols are still in use, it’s inexplicable to me that ANYONE would use FTP in the 21st century, but we do, and, we also still use SMTP, POP3, and IMAP, despite their inherent insecurity. We have put some bandaids onto these old protocols, but they are of limited user – more on them later.
The life cycle of an email:
So – lets say I want to send an email to Allison – how does that work?
I start by opening a mail client of some sort, be it an app on my Mac, phone or tablet, or by using a web-based email client like GMail, and typing the email. I enter Allison’s address, which will be of the form [identifier]@[domain_name], I enter a subject, I type my message, and I hit “Send”. My mail client will then contact the SMTP server it has been configured to use (it might be an SMTP relay belonging to my ISP, or an SMTP server belonging to my email provider). The SMTP protocol is entirely in plain text, and is so old that it is actually written to be human-readable! When lecturing Information Processing a few years ago one of the assignments I gave my students was to send an email by telnetting to port 23 on the university’s mail server and manually issuing the SMTP commands – it is staggeringly easy!
Below is a sample SMTP conversation:
Client: HELO
(Server responds with version header and greeting message)
Client: MAIL FROM: [email protected]
(Server responds with OK message or error message)
Client: RCPT TO: [email protected]
(Server responds with OK message or error message)
Client: DATA
Subject: My Subject
Mail Message
.
(Server responds with OK message or error message)
Client: QUIT
(Server closes connection)
This all happens over and unencrypted connection – so you can see how trivial it is to eves drop on an email it is it being sent to the SMTP server.
Once the SMTP server gets the email, it makes a DNS query to get the MX (Mail Exchanger) record for the recipient’s domain name. It then has the same SMTP conversation with the SMTP server specified in the MX record as the client had with it – so again, your email is flying through the internet unencrypted.
The SMTP server pointed to by the MX record is often not actually your recipient’s mail server, but some form of mail gateway that process the mail in some way (e.g. spam filtering and/or virus scanning) before using SMTP yet again to pass the mail on to your recipient’s actual mail server (there could be anywhere from one to infinity hops between the originating SMTP server and the recipient’s mail server).
Once the mail is on the recipients server their mail client (again, it could be an app or a web app) will then retrieve the email by using POP3 to transfer the mail from the server to their client, or IMAP view it on the server. POP3 and IMAP are also human-readable plain-text protocols just like SMTP, so again, eves dropping is trivially easy, and worse still, you have to send a username and password to the server over POP3 or IMAP!
Security Bandaids:
If you are in an internet cafe sending and receiving email then all your fellow diners, and everyone outside but still within wifi range can:
1) read any email you send
2) read your username and password (and if you re-use those elsewhere …..)
3) read any email you download via POP or read via IMAP
Bandaid 1 – SSL/TLS:
Clearly, something had to be done, so there have been some updates to try retro-fit come security to these protocols. The approach was very similar to that taken with HTTP, SSL/TLS was bolted on, to give encryption between clients and servers. HOWEVER, not all email providers provide SSL/TLS support, so you need to check your mail settings to see whether or not you are using these optional security bolt-ons.
The biggest risk is that communications between your mail client and your mail servers will be intercepted by someone else on the same network as you, so the things you need to check are:
1) that your mail client is configured to use Secure SMTP (AKA SMTP+TLS/SSL) when sending email
2) that your mail client is configured to use Secure POP3 or Secure IMAP (AKA POP3+SSL/TLS or IMAP+SSL/TLS) when downloading/viewing email
HOWEVER – you have no control at all about what happens between your SMTP server and the recipient’s mail server – there will be one or more hops between those servers over which you have no control, and which could be sending the email in plain text, so you have to assume that your email is being read, and never ever email anything sensitive to anyone with one exception – if the sender and receiver use the same mail server, and if that server uses SSL/TLS for all it’s communications with clients, then you can be sure your mail is not flying around the internet unencrypted.
Bandaid 2 – S/MIME:
If you need to send something sensitive via email to someone who does not share your mail server, then you MUST encrypt it using S/MIME (or something like PGP or GPG). To do this you’ll need an S/MIME certificate signed by a trusted CA and it’s matching private key. This certificate is basically the same as the certificates websites use for HTTPS, but it authenticates to an email address rather than a domain name.
To get started encrypting email with S/MIME you’ll need to get a certificate from a trusted CA. You COULD spend money and get one from Verisign or someone like that, or, you could get a one-year one from startSSL.com for free (they charge for longer duration certs). Bonus tip – if you are doing this from a Mac, use Safari, because it uses the OS X keychain rather than it’s own custom keychain like FireFox does, and this will save you two steps later on.
If you don’t have an account with startSSL already you’ll have to set one up, which will involve the installation of a certificate in your browser (if you use the email address that you plan to encrypt then the cert generated to sign up will actually be an S/MIME cert for that email address so you won’t even have to generate a cert).
If you do already have an account, and you didn’t sign up with the same email address you want to encrypt from, then you need to first validate the email address using their Validation Wizard, then, generate the cert using their Certificate Wizard. When the cert is generated it will be installed into your browser’s keychain along with it’s matching private key. If you use Safari and Mail.app then you don’t have to do anything with the cert after it is installed. If you use any other browser and mail app combination you’ll have to export the certificate and key from the browser as a .p12 file and then import it into the OS X keychain and/or your email client. Even if you use Safari + Mail.app you should export a copy of the cert from the OS X Keychain as a .p12 file (an encrypted format) and save it somewhere safe (I stick it in 1Password).
Once you have your S/MIME certificate installed in your mail client you can immediately begin to digitally sign your emails. This will not protect the content of your messages from being seen as they pass through the internet, but it will prevent them being altered, and prove to your recipient that the email really is from you, and not from an impostor. The added bonus of sending signed emails is that it means your recipients get a copy of your S/MIME cert, which they will need if they want to send you encrypted mail.
To use S/MIME for encrypting email both you and your intended recipient must have S/MIME certs, and you must each have a copy of each other’s certs (if you each sent one signed email to each other your mail clients should have saved those certs). You can then encrypt emails between each other if your mail client support S/MIME.
Our OS X ( and iOS) Mail.app is great for this – Mail.app saves every S/MIME cert it receives from your contacts automatically, and it finds your S/MIME cert(s) in your OS X Keychain automatically as well. If you use Mail.app to send an email from an account that you have an S/MIME cert for, you will see two extra buttons in the compose window – one that looks like an old-fashioned seal – this controls whether or not you digitally sign the outgoing email (IMO you should ALWAYS do this if you have a cert), and one that looks like a padlock – the padlock will be greyed out until you type a recipient for which Mail has a cached S/MIME cert, but if if has a cached cert for your recipient you just click on this icon and the padlock will close, signifying that the email will be encrypted.
Tip – to get your S/MIME cert onto your iPhone or iPad, email it to yourself as a .p12 attachment and open that attachment in iOS’s Mail app, it will then install the cert.
As we mentioned in the chat, Bart had me walk through creating the certificate and installing it, and I’m working on making it a pretty Clarify tutorial for you to follow along. I hope to have that done for you early next week, so stay tuned.
That’s going to wind this up for this week, many thanks to our sponsor for helping to pay the bills, Blue Mango Learning at bluemangolearning.com makers of ScreenSteps and Clarify. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter at @podfeet. Check out the NosillaCast Google Plus Community too – lots of fun over there! If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.

I have a “well actually” to add to today’s CCATP. Bart said that if an email is destined for someone within the same company, then you’re fine, as the mail does not have to traverse across any public networks, and is thus immune from snooping. This may be true for smaller companies, but may NOT be true for some mid-sized companies, and is most likely NOT true for large (and especially multinational) companies. Most large companies and even many mid-sized companies run multiple mail servers to segregate different departments, better manage server load/resources, etc. So even if an email is destined to someone within the same company as you, that person’s mailbox may not necessarily be on the same mail server as you, which means then that your email would be sent through the corporate intranet and is vulnerable to being snooped on while it is traversing through the corporate network. Granted, this is much smaller of an attack surface than the whole of the Internet, but it is still significant.
Also, even if the mail stayed on one server, it is still vulnerable to being read by anyone with an admin account on that server (or any miscreant who gains illegal access to an admin account on that server).
And finally, many companies, especially smaller ones, have increasingly started outsourcing their IT functions, including mail, to third parties. Which means your data is once again whisking across the whole of the Internet.
Great CCATP on certificates. Thanks.
I got my free cert from startSSL. It seems to be installed, and I get the encrypt and digital sign button when creating a new mail. However, when I look at my certificate in Keychain it is marked in red with “this certificate was signed by an unknown authority”. That doesn’t sound good! How do I resolve this?
Not sure what extra info you need. The cert is installed in my login keychain. Also in the login keychain are private and public keys named ‘Key from http://www.stratssl.com‘. The cert states ‘issued by: StartCom Class 1 Primary Intermediate Client CA’.
My certificate is named ‘ (letters and numbers)’ and if I try to export it the Personal Information Exchange (.p12) option is greyed out – only the .cer, .pem and .p7b options are available.
I signed up for and installed the cert using Safari.
Did I break it?
Donald: In the case of a large company though the communication between the many mail servers belonging to the organisation are all within the control of that organisation, so you’re not leaving a trusted environment. Assuming the company care about security and have employed good technical people the communication should be secured by either keeping all the communications within a secured network segment, and/or, enabling SSL/TLS on the SMTP traffic between the various servers. You’re right that the traffic is not staying on the one server, but it is staying within the organisation’s infrastructure.
Gavin – I think you’ve found the wrong certificate. When we were experimenting the same happend to Allison, and the symptoms were the same, she couldn’t export the cert as a .p12 file. In Keychain Access, make sure you have the Login keychain selected in the top section of the left sidebar, and “My Certificates” in the bottom section of the left sidebar. Your certificate from S/MIME certificate’s name will start with the email address you used, and then be followed by some random glop. I’ve uploaded a very redacted screenshot of my cert in the hope it helps you find yours: http://cl.ly/image/0P1E3Q0e0m3V
Thanks, Bart and Allison. That description of how to rather painlessly send encrypted email has great appeal.
But how about attachments? Do they send encrypted, or just remain attachments outside the email?
I referred back to Show #384 in which Allison described using the Terminal to create encrypted files to email, sending the password to her financial adviser through a separate channel.
For that I again recommend the free Keka program
http://www.kekaosx.com/en/
Which may also be available on the Mac App Store. Keka creates and opens Windows compatible deeply encrypted 7zip files.
Hi Bart,
I’m pretty sure I’ve got the right certificate. Here’s a link to a screenshot of the certificate in my keychain access: http://cl.ly/image/0y180n3Q1N30.
It looks very much like yours, except it’s signed by an unknown authority and my private key looks different and uses http://www.startssl.com rather than StartCom Ltd.
Any ideas?
Hi George,
Attachments do indeed send encrypted (tested this by sending an encrypted mail with an attachment to myself and trying to open it on a computer where I hadn’t installed my certificate yet).
I can second your recommendation of Keka – it will give much stronger encryption than using zip on the command-line – the biggest problem with the command line encrypted zip is that it’s only the files that get encrypted, not their names, which can leak a lot of information. I use Keka myself when I want to create properly secured zips.
Bart.
When I was sending the cert to the iOS devices I got a message saying
The container “Identity Certificate” must contain only one certificate and its private key.
??? Any ideas – Anyone else the same?
I got that problem sorted – I had show – All Items selected in the left section of the KeyChain. When I selected just Keys I was able then to hit a disclosure triangle – Select the certificate and then to the export.
The wrong one was only 2kb in size and the right one was 4.5kb
Now it all works on iOS just as on the Mac. I have been able to send and receive encrypted emails.
Thanks again Bart.
Gavin – that doesn’t look like the right cert because it’s not showing as valid, and because what I can see of the description text on the key is wrong, but, looking at the dates on the certs listed, there doesn’t seem to be another candidate. This sounds silly, but you did generate the cert from the same account as you are accessing the keychain from yes? Oh – also, what version of OS X are you using? I only have access to Mountain Lion, so maybe something is subtly different in older versions.
Hi Bart, I definitely generated the cert from the same account I’m accessing the keychain from. I’m using Mountain Lion OS X 10.8.3.
Here’s a link to a screenshot of the first part of the actual certificate: http://cl.ly/image/0r372l472F3b.
Could there be a problem with the certificate itself? Looking at the startSSL website FAQ, there doesn’t seem much I can do to get a new cert issued, without handing over cash etc. Perhaps I just have to put this down to experience and forget about it until the cert expires in a year’s time and they issue a renewal.
I’m seeing something similar on the iPhone Bart. Here’s a link to what my cert looks like on iOS: https://www.evernote.com/shard/s1/sh/d56882df-4670-457f-802b-d71c4d9f3719/946d5dafc080ca816a9d82f0bff6b6ed
I’m getting a tad confused here at this stage, so I’m going to try clarify some things.
Firstly, Gavin, can you still not export your cert as a .p12, or were David Allen’s instructions able to sort that part of the problem out for you?
Secondly – it seems odd that OS X does not trust your StartSSL Cert Gavin, when it does trust mine – you haven’t manually removed any CA certs from the system root have you? (seems unlikely, but worth asking all the same).
Thirdly – the untrusted thing is iOS is a red herring because it seems iOS marks just about everything that is not signed by Apple as untrusted for some reason. For work I have a very much paid-for S/MIME Cert from the top-tier CA and iOS also shows it as untrusted. It does the same with the certs for a VPN I use which are also all properly signed by a top-level CA.
Finally – does your cert allow you to authenticate to StartSSL’s web control panel Gavin? If so, you might be able to use they Certificate wizard to generate a new cert, if not on that exact email address, perhaps on another email address you control.
Bart.
Bart,
Thanks for persevering with this 🙂
Answers to your questions:
1 – I now seem to be able to export the cert as .p12 from various Keychain categories i.e. My Certificates, Keys and Certificates. Although the resulting .p12 file is only 3KB, not 4.5KB as David states.
2 – I haven’t knowingly removed any CA certs from the system root. I have 2 system root certs from StartCom. Both are named StartCom Certification Authority and expire 17 Sep 2036 20:46:36.
3 – Not too worried about iOS at the moment!
4 – I can get to StartSSL’s web control panel using the cert. Using the Validations wizard I validated a sleeper gmail address I have. I then generated a cert for this email address (I was using Safari). The StartSSL Certificates wizard is reporting success but during the process the Keychain Access app fired up and reports the following error: http://cl.ly/image/0J0Z3J072I0y. I can’t remember if I got this error when creating my first cert.
Gavin
The size of the file does seem to vary. I did another email address on the StartSSL site and it was slightly smaller, still worked out OK though. I have been doing this using Chrome and it didn’t make it more difficult than using Safari.
so David, when you used Chrome did it automatically add the certificate to the Apple Keychain?
I went to the set up page in Chrome -> Preferences -> Show Advanced Settings then hit the Manage Certificates button and – It immediately opened up the keychain to accept it.
https://www.evernote.com/shard/s2/sh/ea2f57d3-56a7-44d4-b9cd-1d13924a3abe/f5cd777cc4c624158a5e695750e77bd6
This is the button that you are looking for on the Chrome Prefs page.
Question –
When the certificate expires after 1 year does that mean that all of those emails sent or received using it will no longer be readable?
Thanks for the info Bart that iOS always shows as untrusted, but it’s also not working. When I send email from my iPhone from Podfeet.com (the cert is on podfeet.com email) it does not come across as signed like it does if I send from my Mac. So I think something else is wrong. To reiterate the steps:
in Keychain, clicked on Login in the top left, Certificates in the bottom left, and right clicked on the cert for [email protected] and chose export as .p12. Emailed that to myself from podfeet.com to podfeet.com, and opened on the iPhone. It asked for my lock screen code, then the pw I’d put on the cert and then installed it.
Steve and I did 237 more tests and figured it out. On the iPhone you need to go into Mail/Contacts/Calendar, select the email account, go into Advanced, turn on the switch that says S/MIME, click on sign (which will be saying no) and flip the switch to yes. After all that, back out until you see DONE at the top right and make sure you tap that or all of your changes will not be recorded. NOW I have a cert that says it’s trusted and I can send signed mail from my iPhone. tired now.
Bart,
Hi. The name is John but I go by NASANut on the castaways chat room. However, Allison knows me as Joe or Tim or Jim, or what ever she wants to call me that week ;-).
I enjoy your episodes on Allison’s show, especially the security & protocol related ones. I just finished listening to podcast 412 were you talk about email security.
I thought you might have a solution for a problem I have. I use Apple Mail 5.3 on Lion at work and we use Exchange 2007 server. It seems that when I add an attachment to an email and I then encrypt that email (using the lock button), most of the Window’s users I send it to will not be able to see the attachment. They can open the email, their Outlook shows the little paperclip indicating there is an attachment and the file size will be appropriate for the attachment. They just can’t see and open the attachment.
Any thoughts?
John – I got close this time didn’t I? I got the J…(love your comment)
Hi,
Late into this thread but finished latest Podcast today.
Have been playing with S/MIME & GPG that I have installed in mail.
I have a few e-mail addresses but what makes it a little more difficult when playing around with e-mail encryption is that I have 4 iCloud Alias accounts. So when testing by sending e-mails to myself it is quite tricky remembering exactly what I have certs for & what not. Also does an alias respond to the “root” e-mail address certificates. In other words if I have a iCloud e-mail of [email protected] & an alias of [email protected], will the alias recognise the certs. I have installed on [email protected]? If you see what I mean?!!
One little trick to prove the e-mail is encrypted as it arrives de-encrypted in the clear is to go to Mail – View – Message – RAW SOURCE. And there is the encrypted data!
Quite reassuring.
All good fun!
Hi Nick,
There is no way for a cert to just “know” that something is an email for something else. A certificate binds a public key to an email address in a notarised way. You basically take the key, you take the email address, you add in some metadata, compose all the information into a standard format, and then the certificate authority digitally signs this formatted information to create the certificate. I can’t say for sure that you can’t get one cert that contains more than one email address, but, what I can say is that if that were possible you’d have to enter all the email addresses at the moment the certificate is created.
I know that for websites which use the same CA architecture as S/MIME you can get a special kind of web server certificate that covers multiple domain names in one cert (called a SAN Cert, where SAN = Service Alternative Name). I’ve not heard of such a thing for S/MIME certs, but that doesn’t mean they don’t exist.
Bringing it all back to your original question, will the cert just work on aliases – nope.
Bart.
Hey there would you mind letting me know which web host
you’re working with? I’ve loaded your blog in 3 completely different web browsers and I must say
this blog loads a lot quicker then most. Can you suggest a good web hosting provider at a honest
price? Thanks, I appreciate it!
I loved as much as you will receive carried out right
here. The sketch is attractive, your authored material stylish.
nonetheless, you command get bought an nervousness over that you wish be delivering the following.
unwell unquestionably come more formerly again since exactly the same nearly very often inside case
you shield this hike.