I had the fun of being on The Mac Show on the British Tech Network this week. Interviews from Macworld include Chore-inator from binaryformations.com, and Handy Photo from adva-soft.com. Then we get a real review of Handy Photo from Mark Pouley, aka switcher mark. Rogue Amoeba from rogueamoeba.com shows off Fission 2, and we hear about advancements in Cloak 2 VPN service from getcloak.com. I gave Cloak 2 a try from the App Store and it was amazingly easy! In Chit Chat Across the Pond Bart explains Heartbleed to us and why it was so important.
![]()
mp3 download
Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday April 13, 2014 and this is show number 466. Holy cow do we have a PACKED show for you today! We’ve got a bunch more interviews from Macworld, we’ve got a review from Mark Pouley, and in Chit Chat Across the Pond Bart is going to give us the straight story on Heartbleed. You’ll really understand it afterwards and also understand why it was such a big deal.
 Before we kick into that, I wanted to let you guys know that I got to be on the Mac Show on the British Tech Network, hosted by Ewen Rankin with guests Adam Christianson, Paul Kent, Jean MacDonald, Ken Ray and Paul Wheatley. There’s a direct link in the shownotes, or you can just go to britishtechnetwork.com and click on the big MAC icon on the left. Large Mac, not Big Mac. Ok, let’s get started on those interviews!
Before we kick into that, I wanted to let you guys know that I got to be on the Mac Show on the British Tech Network, hosted by Ewen Rankin with guests Adam Christianson, Paul Kent, Jean MacDonald, Ken Ray and Paul Wheatley. There’s a direct link in the shownotes, or you can just go to britishtechnetwork.com and click on the big MAC icon on the left. Large Mac, not Big Mac. Ok, let’s get started on those interviews!
Chore-inator from Binary Formations
Debbie Quetsch from Binary Formations at binaryformations.com was very enthusiastic about their app Chore-inator and I couldn’t help but catch her excitement. I think it could make it much more fun to assign chores to children, and have them get rewarded for what they do. If I had young children I would definitely give it a try.
Handy Photo from Mark Pouley aka SwitcherMark
The second interview we’re going to play is for a product called Handy Photo from AdvaSoft at adva-soft.com, but there will be a twist afterwards. Mark Pouley, aka SwitcherMark bought Handy Photo and he has a review for us too. So we’ll play the audio from the interview and then hear how well it works in real life from Mark. Let’s have a listen.
=== Insert audio interview===
Hello Castaways, this is Mark Pouley reviewing the iOS photo processing app Handy Photo. I picked this up at Macworld and Allison just played her interview with the developers. I was so impressed with the demo I saw at Macworld that I bought the app as I walked away from the vendor’s table in “tiny town.”
Handy Photo is a universal iOS app, but you’ll want to use it on your iPad to take advantage of the full real estate of the screen. I can’t imagine using this on a phone screen.
There are many, many, photo processing apps available on iOS so what’s the problem to be solved by Handy Photo? One of the downsides of having so many photo processing apps, is that good apps often do one or two things well, but sometimes that forces me to move an image from app to app to complete a project. There are several apps that do a nice job of correcting exposure, contrast, color, etc. (Snapseed comes to mind as my favorite), but I’d also like an app that was able to do a little more “heavy lifting” editing, such as removing unwanted objects from an image. In other words, I’d like a single app that gives me many of the features I’m used to in desktop image processing, but with a UI that takes advantage of the touch interface on the iPad. Finally, I’d like an app that gives me these features at a reasonable price. I think Handy Photo meets these criteria.
 Handy Photo is a full featured image processor. In fact, it does so much that I can only mention the highlights in this review. Like many editors, it does a nice job adjusting brightness, contrast and saturation. More then some apps, Handy Photo also adjusts levels, shadows, highlights and warmth. These can be global adjustments, but even better, you can apply linear and elliptical gradient filters to apply the adjustments to portions of an image, (changing the color of the sky from dark blue to lighter blue from the top to the horizon for instance) or use brushes and masks to control the areas of the image being processed. One of the things I like about these tools is an “edge aware” process that limits adjustments to areas of an image with the app recognizeing changes in color and contrast to contain the editing. There’s also a “color picking” tool so you can limit the adjustments to particular colors in an image (let’s say you just want to boost the red flowers in an image without over saturating the other colors). These are powerful tools normally found in professional level desktop applications and they work really well as implemented in Handy Photo.
Handy Photo is a full featured image processor. In fact, it does so much that I can only mention the highlights in this review. Like many editors, it does a nice job adjusting brightness, contrast and saturation. More then some apps, Handy Photo also adjusts levels, shadows, highlights and warmth. These can be global adjustments, but even better, you can apply linear and elliptical gradient filters to apply the adjustments to portions of an image, (changing the color of the sky from dark blue to lighter blue from the top to the horizon for instance) or use brushes and masks to control the areas of the image being processed. One of the things I like about these tools is an “edge aware” process that limits adjustments to areas of an image with the app recognizeing changes in color and contrast to contain the editing. There’s also a “color picking” tool so you can limit the adjustments to particular colors in an image (let’s say you just want to boost the red flowers in an image without over saturating the other colors). These are powerful tools normally found in professional level desktop applications and they work really well as implemented in Handy Photo.
The feature highlighted in the Macworld demo, and mentioned in Allison’s interview, also caught my eye. That’s the ability to erase & move objects in photos and do basic retouching to clean up images. Handy Photo does this using a process that Adobe calls “content aware” editing in Photoshop. Explained simply, it’s a tool to erase objects and allow the program to automatically fill in the newly created empty space with content the app thinks is consistent with the space it is filling. A step up from content aware erase and fill, is cutting an object out and moving it to another location in the photo, using basically the same process. Similarly, Handy Photo allows for what they call smart uncrop and straighten. Let’s say you straighten an image so that it creates empty space in the corners. Ordinarily you would have to crop the image to eliminate the empty space. Handy Photo instead uses the content aware process and tries to fill that space with appropriate content. For intense, if you straighten an image with sky at the top, creating an empty space in the corner above the sky, the App fills the space in with more sky.
All of these “content aware” edits can be a huge time-saver and can do a really good job. But not always. This works with varying degrees of success, even in very expensive applications, depending on the image content and the application algorithm. The more complex the image the less likely it is to work. Handy Photo is not the first or only app to offer this technology in an iOS app, but it is one of the better implementations of the process I’ve tested. It’s not perfect, but I was impressed often enough to recommend the app.
I particularly like how well the features work on the touch screen of the iPad. Most corrections are completed by “painting” with a finger and swiping to increase and decrease effects. The app enables very precise actions when necessary by calling up a magnifier that blows up the image and shows a cross-hair target just next to where your finger is drawing so you can see what you’re doing. I really like this. It is very well implemented and addresses one of the frequent problems encountered trying to process images on the iPad.
In general, the UI is refreshing and takes advantage of the real estate and clarity of the iPad. The controls look good and are easy to activate, but not the controls and icons are not immediately intuitive. Also, since the app includes so many features there’s a bit of a learning curve. I think this can be expected, as the app does more things, it will become slightly more complicated. Even so, I found myself picking it up fairly quickly. As a bonus, the app includes handy pop up tips as you open new areas of the application or hit the help button at any time. Even better, there’s a whole section of video tutorials in the app that link you to you tube videos demonstrating all the main features. The tutorials are short and clear. I easily learned how to use the app watching them.
In addition to the learning curve, which I don’t really consider a critique, I found what appears to be a bug. At Macworld and on line the developers tout the app’s ability to handle RAW files. In my test, the app sees RAW files in the camera roll, but when I tried to open any of them it didn’t work. I contacted the developer and they confirmed that not all cameras are supported, but they intend to release updates. Most users won’t be processing RAW images on their iOS devices so I don’t know that this is a major flaw, but it’s an advertised feature that doesn’t work for all users.
This is a powerful and full featured processing app with a bargain price. It’s just $1.99 (on sale for 99 cents?) in the app store. There’s a free version that doesn’t include some advanced features but it will let you check out the UI. The price for the full app is much less then other apps, like Photoshop touch that have similar features.
I’ll continue to process my important photo projects on my computer using professional grade applications. But the ease and power of Handy Photo encourages me to process more images on my iPad beyond simple tone adjustments or the application of simple filters. I recommend this app to anyone that is looking for that increase in photo processing power in iOS.
Wow, Mark, now I understand why you were saying how hard it was to make a short review! I thought all Handy Photo did was the content aware editing you talked about to remove things from photos, I had no idea it was a full featured editor. As soon as I heard your review, I raced out and bought Handy Photo, definitely going to enjoy this one.
Rogue Amoeba
Rogue Amoeba’s Paul Kafasis shows me what’s new in Fission 2. Rogue Amoeba is at rogueamoeba.com. I love Rogue Amoeba, could you tell from my gushing all over Paul about how awesome his products are? When I got my new MacBook Pro, I discovered that I no longer had a separate audio in and audio out jack, which meant a big problem for how I piped the audio for the live show. I contacted Paul and he spent a ton of time teaching me how to use Audio Hijack Pro to do what I was doing in hardware before, and it actually made cleaner audio and a much simpler setup. Great products and great support, Rogue Amoeba is one of my favorite vendors!
Cloak 2
 Last year I interviewed the guys from Cloak, the VPN service, but this year Peter Sagerson took it up a notch. You can find Cloak at getcloak.com.
Last year I interviewed the guys from Cloak, the VPN service, but this year Peter Sagerson took it up a notch. You can find Cloak at getcloak.com.
I’m going to save the last two interviews for next week because I really want to talk about the VPN thing. When I heard that Cloak 2 was available a la carte for $3.99 for single week or $9.99 for a month for all of your devices, that really started to sing to me. The ability to buy a cup of VPN just when I need it via an in app purchase is perfect. Having ti work on all my devices is awesome, and then throw in being able to tell it which networks you trust or don’t trust – what the heck more could you want?
I decided to give the Cloak 30 day free trial a test. I downloaded it from the App Store, and I’ll give you a little hint – it has a blue logo with a white wifi signal on it and says it’s from Bourgeois Bits. Make sure that’s the one you choose because there are several apps called Cloak. I put a link in the shownotes so you’d be sure to find it.
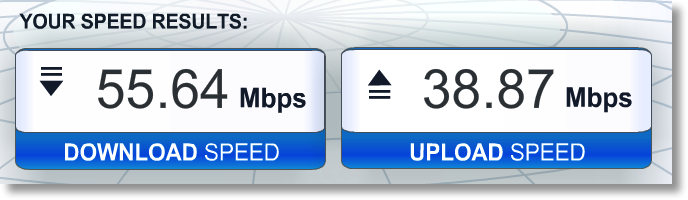
I loaded it up, and I have to say, they’ve made this completely dead simple. I installed on the iPad, it told me to sync my settings, which opened Settings and asked to install a profile, and somehow took me right back to a page saying to start using Cloak. Not actually sure how they did that! They had a few instructions, one being how to tell it what networks to trust, so I told it to trust my home network and to trust Cellular networks since those aren’t shared like public wifi. I can’t wait to go to Starbucks tomorrow and verify if it kicks in automagically like they said. Another question you might have is whether it’s fast enough. I only have one data point but when I tested it, I got 55Mbps down and 39Mbps up. I’d say that’s acceptable.
OpenVPN
I decided to test out Cloak for another reason other than the mere fun of it. This week after all heck broke loose with Heartbleed, Leon Sargent wrote me a note asking a very intelligent question – he asked if my fancy home VPN that Donald taught me to build was vulnerable to the same OpenSSL bug. I forwarded the note to Donald who wrote up some awesome instructions. I’ve put them up as a page on Podfeet.com, so if you want to check your own OpenVPN installation there’s a link in the shownotes https://www.podfeet.com/blog/tutorials-5/how-to-update-openvpn-for-heartbleed-openssl-vulnerability/.
Basically all I had to do was:
- Figure out whether I was running a vulnerable version
- Tell the server to look for self updates
- Ask the server to compare what ports are installed to the updates to see which ones are outdated
- Upgrade the SSL port in question
- Uninstall the old SSL port
- Go through the 126 step process of recreating a new certificate for the five devices we use to connect to our home VPN server, put them in Dropbox, open them in the respective devices and install them
So easy peasy right? I did a lot of whining about having to do all this but I’m glad I went through it because I learned two things. 1) this is what every web server admin on the planet had to do this week, and 2) now I’m CERTAIN I want to use Cloak whenever I’m on untrusted wifi. I bet I even go for the monthly $3.99 plan eventually because of that auto-detect feature. I do want to give many thanks to Leon for putting the pieces together and asking the right question, and to Donald for taking the time to write up such great instructions as always.
Clarify
A couple days ago I was chatting with a neighbor of mine and he told me that his aunt had passed away and he wanted to create a playlist in iTunes for her service but couldn’t figure out how to do it. He’s got a new Windows 8 machine but iTunes is pretty similar between the two operating systems so I figured I could help. I also was pretty darn sure I knew what was making it hard; in the later versions of iTunes they hide the left sidebar by default so you’d never be able to find the whole Playlist thing in the first place. Maybe he was stuck on something else but I still figured I could help. I went home, whipped open Clarify and in a few minutes (while I was on a call with someone else actually) I took a few screenshots, used timed screenshots even so I could capture some pulldown menus, dropped in some arrows and text boxes as annotations on the graphics, and even a couple of sequence numbers to help him follow along. I tapped the Upload to Clarify-it button and in a few seconds I had a web page showing him with a beautifully formatted tutorial. I know he’ll be tickled pink when he sees it, and you can delight and amaze your friends and family too if you head on over to Clarify-it.com and check out the free trial. You can even test the beta of Clarify 2 by going to the link in the shownotes, it’s AWESOME!
Chit Chat Across the Pond
Security Light
Important Security Updates:
- Two patch Tuesdays since the last security lite:
- March – patches from MS (Windows, Silverlight & IE – including a patch for a nasty zero-day) & Adobe (Flash & Shockwave) – http://krebsonsecurity.com/2014/03/adobe-microsoft-push-security-updates/
- April – patches from MS (Windows, IE & Office – including a nasty zero-day) & Adobe (Flash & AIR) – http://krebsonsecurity.com/2014/04/adobe-microsoft-push-critical-fixes/
Some important Security ‘News’ debunking:
- Last month there was a big hubbub about how WPA2 had been cracked – it was parroted all over the media, but had no actual foundation in fact. It all started with one news report about one scientific paper that was hidden behind a paywall. Media outlets around the world just parroted this one un-substantiate report, without checking the original source. When security researchers forked over the €30 to see what the paper actually said they found that it contained nothing new. We’ve know for years that WPA2 needs long passwords to be secure. As is usually the case when the media get something wrong, I couldn’t find any clear retractions to link to. Best I can do is point anyone interested in what this was all about to Security Now episode 448 – https://www.grc.com/sn/sn-448.htm
- There was also a big hubbub about nothing when some tech sites mis-understandings of how DropBox works led to a lot of miss-guided outrage – short version, nothing to see here – http://techcrunch.com/2014/03/30/how-dropbox-knows-when-youre-sharing-copyrighted-stuff-without-actually-looking-at-your-stuff/
Important Security News:
- There was a big MS Word zero-day which allowed attackers to run arbitrary code on a system by getting Word (Windows & Mac) to read an RTF file, either directly, or via the Office preview feature in Outlook – http://krebsonsecurity.com/2014/03/microsoft-warns-of-word-2010-exploit/ – there was initially only a FixIt patch, but a full patch was released as part of the April MS Security bulletin – https://technet.microsoft.com/security/bulletin/MS14-017
- Microsoft got into some hot water by choosing to read a blogger’s email because it happened to be hosted on an MS server. Their motive – to track down a leak – http://www.cnet.com/news/microsoft-sniffed-bloggers-hotmail-account-to-trace-leak/. After the web went rabid for a while, MS announced a change in policy, promising not to do it again – http://blogs.technet.com/b/microsoft_on_the_issues/archive/2014/03/28/we-re-listening-additional-steps-to-protect-your-privacy.aspx
- A fake TOR browser laced with adware and spyware got through Apple’s vetting process and made it’s way into the iTunes store – http://arstechnica.com/security/2014/03/fake-tor-browser-for-ios-laced-with-adware-spyware-members-warn/ – TOR say they first alerted Apple to the problem in December, but Apple did not act until XXXXX –
- Apple have released a document detailing how iOS security works (including iCloud) – http://images.apple.com/iphone/business/docs/iOS_Security_Feb14.pdf (Security Now did a three-part analysis of what the document means – the short version is that on the whole, Apple’s security architecture is superb, with just a few notable exceptions. Rich Mogull did a detailed analysis of how iCloud Keychain works on tidbits – http://tidbits.com/article/14557)
- GnuTLS, a commonly used open source crypto library found vulnerable to a bug very similar to Apple’s epic Goto Fail bug – if you’re using Linux, be sure you patch – http://arstechnica.com/security/2014/03/critical-crypto-bug-leaves-linux-hundreds-of-apps-open-to-eavesdropping/ (a totally different library to OpenSSL, so not related to Heartbleed at all)
- Yahoo will stop supporting 3rd party authentication to it’s services – no more logging into Flickr with your FaceBook account etc.. This is a disappointing retrograde step IMO – the re-balkanisation of the web – http://www.reuters.com/article/2014/03/05/us-yahoo-login-idUSBREA2407820140305
- A 5-year old discovered a password by-pass (now patched) in Xbox live – http://nakedsecurity.sophos.com/2014/04/07/microsoft-xbox-pwned-by-5-year-old-security-researcher/
- Google add single-signon to their iOS apps – convenience at the price of privacy (shock horror) – http://qz.com/194032/googles-sneaky-new-privacy-change-affects-85-of-iphone-users-but-most-of-them-wont-have-noticed/ (I liked to stay signed out of stuff like maps, but signed in to stuff like Youtube – not possible anymore, if I want to see my videos, I have to tell Google where I am and where I’d like to go)
- Facebook introduce “Privacy Dinosaur” (cute little cartoon character) to help you get your privacy settings right – http://nakedsecurity.sophos.com/2014/04/07/the-privacy-dinosaur-urges-facebook-users-to-check-their-privacy-settings/
- For a while, the #1 paid app in the Google Play store (Virus Shield) was a scam – http://www.neowin.net/news/the-1-paid-app-in-the-google-playstore-virus-shield-is-a-complete-scam, Google did remove it after it got media attention, but not before 10,000 Android users were scammed – http://nakedsecurity.sophos.com/2014/04/09/google-takes-down-fake-anti-virus-app-that-duped-10000-users-on-play-store/
Noteable Data Breaches:
- ComiXology suffer data breach – if you’re a user, reset your passwords (credit cards not exposed, and passwords were hashed) – http://www.macobserver.com/tmo/article/password-reset-time-comixology-loses-user-data-in-security-breach
- California DMV reportedly suffered credit card breach – http://krebsonsecurity.com/2014/03/sources-credit-card-breach-at-california-dmv/
- Sally Beauty breach reportedly bigger than previously admitted, affecting all 2,600 stores across US – http://krebsonsecurity.com/2014/03/zip-codes-show-extent-of-sally-beauty-breach/
- An EA website was hacked and then used in a phishing scam to try get people’s Apple IDs – http://news.netcraft.com/archives/2014/03/19/ea-games-website-hacked-to-steal-apple-ids.html
- Texa liquor chain Spec’s leaks over half a million credit cards over 17 months – http://nakedsecurity.sophos.com/2014/04/02/texan-liquor-chain-specs-leaks-550k-card-details-in-17-month-breach/
Suggested Reading:
- Great article about the intricate key-signing ceremony that underpins the security of DNSSEC – http://www.theguardian.com/technology/2014/feb/28/seven-people-keys-worldwide-internet-security-web
- The US to hand over control of ICANN to the international community by the end of 2015 – http://recode.net/2014/03/14/u-s-to-give-up-key-internet-governance-role/
- The EU & Brazil agree a new €135M transatlantic internet connection that will by-pass the US – http://nakedsecurity.sophos.com/2014/03/31/transatlantic-cables-will-bypass-usa-to-avoid-nsa-spying/
- A nice article collecting together instructions for setting up 2 factor auth on popular web services – http://thesweetsetup.com/quick-tip-enable-2-step-verification-popular-web-services/
- Lapse at Experian allowed ID Theft services access to 200 Million customer records – http://krebsonsecurity.com/2014/03/experian-lapse-allowed-id-theft-service-to-access-200-million-consumer-records/
- Dendroid, the latest Android RAT (Remote Administration Tool) malware toolkit raises eyebrows because it can sneak into the play store, and, because it’s so cheap – only $300 for an unlimited license – http://appleinsider.com/articles/14/03/07/new-android-rat-infects-google-play-apps-turning-phones-into-spyware-zombies
- The Washington Post report that the NSA can record “100%” of a foreign country’s phonecalls and re-play them up to a month later – http://www.washingtonpost.com/world/national-security/nsa-surveillance-program-reaches-into-the-past-to-retrieve-replay-phone-calls/2014/03/18/226d2646-ade9-11e3-a49e-76adc9210f19_story.html
- James Clapper (US Inteligence Chief) admits what we all knew already, that the NSA conducted warrantless wiretaps on Americans (4th amendment be damned) – http://nakedsecurity.sophos.com/2014/04/02/james-clapper-confirms-that-nsa-conducted-warrantless-searches-on-americans/
- Airplane internet provider GoGo Wireless may be going above and beyond the call of duty and spying on users to make lifer easier for the feds – the EFF and not best pleased – http://nakedsecurity.sophos.com/2014/04/11/in-flight-wifi-providers-go-above-and-beyond-to-help-feds-spy-on-us/
- Reporters Without Borders add the US & UK to their “enemies of the internet” index (joining countries like China, Iran & North Korea) – https://www.eff.org/deeplinks/2014/03/short-guide-internets-biggest-enemies
- NEST have to withdraw smoke alarms after discovering they made a bad UI decision – using hand waving as a signal to turn off an alarm is a bad idea, because in a real fire, people wave their arms around – http://www.wired.com/2014/04/nests-smoke-alarm-stumble-is-a-ui-lesson-for-everybody/
Main Topic – Heartbleed
What Heartbleed is:
- On April 7 details were released of a vulnerability affecting some versions of OpenSSL (specifically 1.0.1 to 1.0.1f)
- The vulnerability has existed for 2 years, but was only discovered recently (though of course some people could have known about it for longer and kept their mouths shut)
- OpenSSL is an important open-source crypto library used throughout the internet – the popular Apache and NGINX web servers use OpenSSL for their HTTPS implementations, many open source mail servers use OpenSSL to add TLS security to their SMTP and IMAP implementations. OpenSSL is also used by other Linux/Unix services including OpenSSH, TLS in OpenLDAP and OpenVPN.
- While there are clearly a lot of affected clients, servers and services the media are of course over-stating the numbers – e.g. you’ll see lots of articles stating that 70% of websites are affected because 70% use Apache or NGINX – that’s not true because many versions of Apache and NGINX use versions of SSL that are too old to be affected by this bug while still being supported and current (there are three currently supported branches – 9.8, 1.0.0 & 1.0.1, ONLY 1.0.1 is affected). E.g. RHEL 6 (and hence CentOS 6) is affected, but not RHEL 5 (and hence CentOS 5).
- The vulnerability allows an attacker to read a random slice of memory – the attacker has no control over what part they see, but, they can run the exploit over and over again – a good analogy would be spying through a keyhole – you can only see a small amount of what is going on in a room at any one time, but if you look long enough you’ll see quite a lot all the same.
- The vulnerability is in OpenSSL’s heart-beat functionality (hence the name) – the heart-beat is a fairly new addition to the protocol, and was added for optimisation. Once an SSL connection is up and running, there is not much overhead to it compared to an un-encrypted connection, but getting a new connection up and running is a much more resource-intensive process. The idea of the heart-beat is to allow connections to be kept open, without timing out, so they can be re-used, saving resources.
- Because Open SSL sits below the application layer in the network stack, heartbeats do not show in application logs, so sysadmins have no way of knowing whether or not their servers have been attacked, or, what the attackers have seen.
- Since the vulnerability exposes a slice of memory, anything the web server stores in memory could be revealed – including usernames and passwords, private keys, and credit card numbers.
- The vulnerability is symmetric – a malicious user can use it to attack servers, but malicious servers can equally attack clients, reading contents from the RAM on their computers!
- The US-CERT page about the vulnerability – http://www.kb.cert.org/vuls/id/720951
How it works:
- A heartbeat request can used to generate traffic at a given interval to stop timeouts in NAT routers or proxy servers closing idle SSL connections. As well as acting as a keep-alive, the heartbeat is also a test of the encrypted tunnel – no point in keeping a connection that’s not working any more open!
- A heartbeat tests the encryption by sending some random data, and asking the server to send it back. If all is well the a reply will come back, containing an exact copy of the random data which was sent. If something has gone wrong, then either there will be no reply at all, or the random data will come back altered.
- A heartbeat request starts with a header that specifies that it is a heartbeat request, and, a statement of how much random data will be sent as part of the request, followed by the random data.
- On receipt of a heartbeat request, the buggy version of OpenSSL ignored the length specified in the header and just read all the data out of the request and wrote it to memory.
- When assembling the reply, the buggy version of OpenSSL used the header data to determined how much information to read back from memory, if the actual data written was less than what the header specified, OpenSSL just kept reading, returning a random slice of memory to the attacker.
- The amount of data leaked per request is finite (limited by the SSL protocol), up to a maximum of about 64Kb.
The best human-friendly explanation I’ve seen comes from the geniuses at XKCD:

The most understandable in-depth nerdy description I’ve seen is from Naked Security: http://nakedsecurity.sophos.com/2014/04/08/anatomy-of-a-data-leak-bug-openssl-heartbleed/
What does this mean for people who run servers?
- You need to check your version of SSL ASAP
- If you have a vulnerable version of SSL, you need to patch it ASAP
- since it is possible that the private key of your SSL Cert has been leaked, you should give serious consideration to replacing all your SSL certs (for big sites the risk is high, for a little VPN server sitting at home on a MacMini the risk is really really low, and everyone else on the net is somewhere in between). Every sysadmin needs to make an informed judgement based on the risks, the value of the information being protected, and the time, energy & money needed to replace all certificates.
What does this mean for users?
- Firstly, your computer or device could be vulnerable to this – remember, this vulnerability is symmetric – so malicious servers can attack you! If you run Linux, Unix, or a derivative there-of, patch you device (if you can).
- Microsoft don’t use OpenSSL (remember, it’s open source), so Windows users don’t have to worry about their devices
- Neither iOS nor OS X were ever vulnerable, so Apple users also don’t have to worry about their devices – http://www.macobserver.com/tmo/article/apple-confirms-heartbleed-vulnerability-doesnt-effect-ios-os-x-or-key-servi
- MOST (but not all) versions of Android are unaffected, so most Android users are fine, but a few MILLION Android devices are NOT fine – if you’re running Android 4.1.1 you have a problem, and, given how many barriers to patching there are, your only option may be to get a new device – http://www.bloomberg.com/news/2014-04-11/millions-of-android-devices-vulnerable-to-heartbleed-bug.html
- Remember, this did not affect every server, so, you can probably rule out needing to do anything on a whole bunch of services. Some googling will help you find out who was, and who was not affected. I found the following list to be very useful: http://mashable.com/2014/04/09/heartbleed-bug-websites-affected/ (note that some of the big names like Google, Yahoo, and Steam were vulnerable, with Google being quick to patch, and Yahoo and Steam slow out of the gate)
- Before you update any password, check that the site/service has actually been patched before you do! If they are on the list linked above, that’s easy, if not, you’ll need to test the site yourself. There are lots of checkers showing up all over the web. Noteably SSL Labs have added a Heartbleed test to their fantastic SSL tester: https://www.ssllabs.com/ssltest/. The SSL labs test is very comprehensive, and hence takes a few minutes to complete, so if you want something quicker that only checks for Heartbleed, you can use this one: http://filippo.io/Heartbleed/. There is also a Chrome plugin called Chromebleed that you can install which will tests sites as you visit them, and pop up a warning if you browser to a vulnerable site.
- You don’t actually have to update everything – you need to make a value judgement based on whether or not you re-used the potentially compromised password elsewhere, whether or not the service offer two-factor auth, and the value of what ever is being protected by the password.
- Remember – OpenSSL is NOT JUST WEBSITES – you also need to check email and VPN providers, as well as any other encrypted services you might use.
- Jeff Gamet compiled instructions for OS X (which covers Safari & Mail), Chrome & FireFox on TMO: http://www.macobserver.com/tmo/article/dealing-with-heartbleed-what-you-need-to-know/P5
- While browsers are important, don’t forget about your mail clients! Mail.app on OS X will be covered by the KeyChain (see link above), and Thunderbird should be almost identical to FireFox in the instructions above. IE & Outlook will be covered by the setting in Internet Options in Windows, which some Googling this afternoon leads me to believe has validation enabled by default.
Quick-links to Useful Resources:
- Heartbleed hit list – who was vulnerable and who wasn’t? – http://mashable.com/2014/04/09/heartbleed-bug-websites-affected/
- Test your sites to see if a) they were affected, and b) is it safe to update your password yet: https://lastpass.com/heartbleed/
- A quick and easy Heartbleed tester – http://filippo.io/Heartbleed/
Further Reading:
- A great (long) article by Jeff Gamet from TMO which explains things clearly and simply – http://www.macobserver.com/tmo/article/dealing-with-heartbleed-what-you-need-to-know
- Page 5 tells you how to make sure your browser isn’t using the revoked certs
Something Fun to end on (and cleanse our pallet after all that security stuff)
A great visualisation to drive home just how big our solar system is – if the Moon were 1px: http://joshworth.com/dev/pixelspace/pixelspace_solarsystem.html
That’s going to wind this up for this week, many thanks to our sponsor for helping to pay the bills, Blue Mango Learning at bluemangolearning.com makers of Clarify. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter and app.net @podfeet. Check out the NosillaCast Google Plus Community too – lots of fun over there! If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.

[…] You know how you get angry every time you get a notification of a monthly bill? There’s ONE bill I don’t feel that way about, and it’s my monthly $3 bill from Cloak knowing it’s protecting my Mac, iPhone, iPad, Steve’s Mac and his iPhone. For $3. Seriously. How could you not put that app in your top 5 menubar apps? If you want to hear or read more about Cloak, I did a full review of it back on Show #466. […]