One of our goals in Home Automation has been to buy HomeKit-compatible devices whenever possible for security reasons. I’ve even created an elaborate network setup to isolate non-HomeKit (and Windows) devices from the rest of my gear.
One of our goals in Home Automation has been to buy HomeKit-compatible devices whenever possible for security reasons. I’ve even created an elaborate network setup to isolate non-HomeKit (and Windows) devices from the rest of my gear.
Last year we bought the first HomeKit-compatible webcam, the Omna 180 Cam HD from D-Link. At $150 it wasn’t cheap but buying from a reputable company like D-Link who clearly have been in the business of network gear for ages gave us peace of mind.
The camera hasn’t been a huge success for us for a few reasons. The video isn’t as sharp as we’d expected. It was supposed to be 1080p but it’s pretty fuzzy. It doesn’t store information anywhere but on its own SD card, which might be a plus for some people but for us it limits the usefulness. It gets pretty hot which concerns us, and it is simply offline sometimes and we have to unplug it and plug it in to get it running again.
But we have used it to discover that when we’re away from the house, Tesla happily sleeps on the couch. We NEVER let her do that so it’s been eye-opening for sure. But none of these complaints are why I’m talking about the D-Link Omna webcam today.
Last October, you may remember that a problem was discovered in the way the wireless protocol WPA2 was designed that caused all wireless clients to be vulnerable to attack. That attack was named KRACK.
Over the next few months, we all watched for updates to our devices. The one device I was worried most about was the Omna webcam but I never got a firmware update for it. In January, I received an invitation from the D-Link folks to come by their suite at CES to talk to them. That sounded swell to me.
Steve and I and Joe LaGreca trooped over to their suite at the Sands Convention Center. I asked to speak to someone about network security and as luck would have it, Senior Vice President and Chief Information Security Officer, (CISO) William Brown just happened to be there.
I asked Mr. Brown when the Omna webcam would have the KRACK vulnerability mitigated, and at first, he said that the Omna wasn’t vulnerable. I reminded him that all wireless client devices that correctly implemented WPA2 encryption were vulnerable.
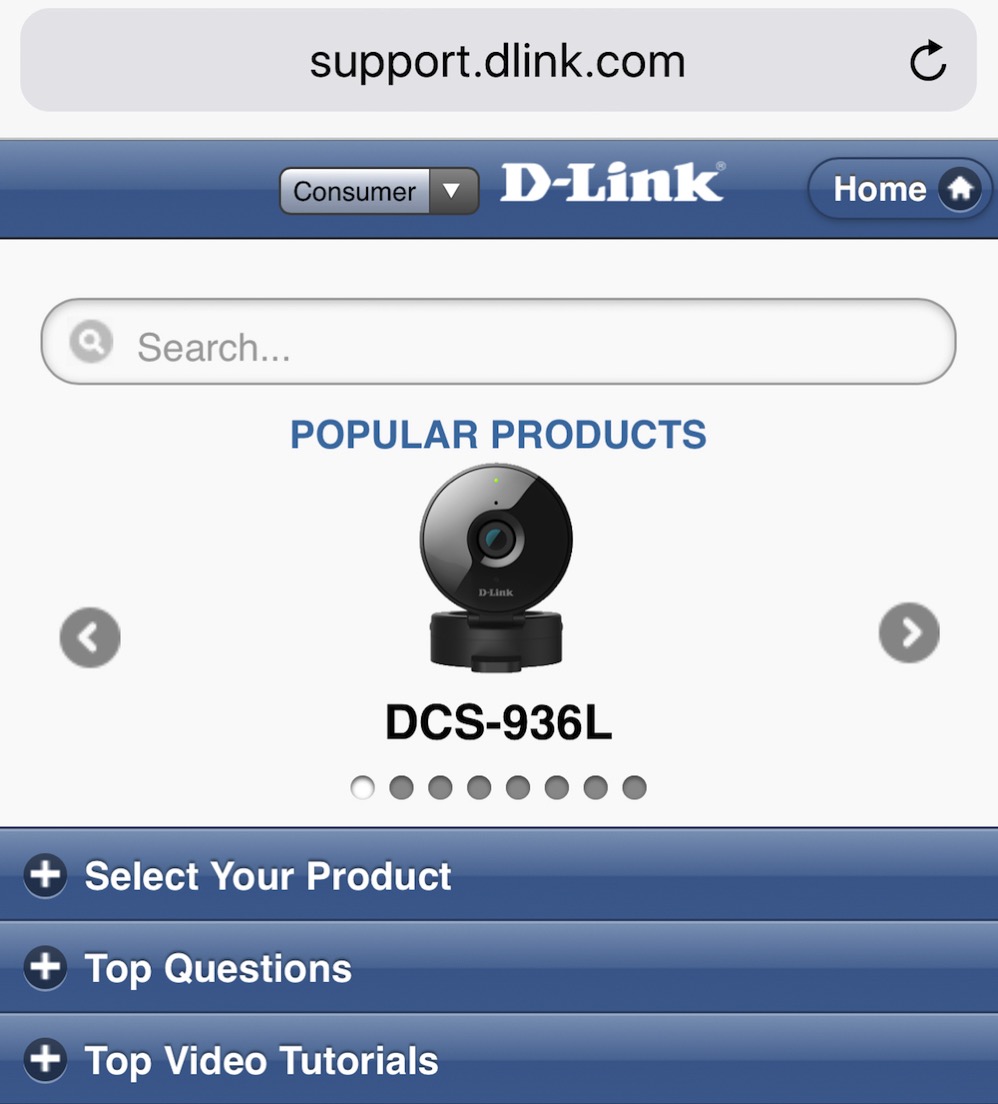 We kept chatting and he asked me whether I had even gone to support.dlink.com to look for a patch (I had, but I humored him). I pulled out my phone and typed support into the URL field, and it auto-filled support.dlink.com. I suggested that indicated that indeed I had been there before.
We kept chatting and he asked me whether I had even gone to support.dlink.com to look for a patch (I had, but I humored him). I pulled out my phone and typed support into the URL field, and it auto-filled support.dlink.com. I suggested that indicated that indeed I had been there before.
We looked together at the mobile site and it had three pulldowns, the first of which was “Select Your Product”. I tapped on that and It revealed two pulldowns, one for Model and one for Number. I tapped on Model and I was shown a long list of three-letter Models, and the number pulldown showed a long list of numbers. I asked him which one of these models was the Omna, and he said, “You can find the model number on the packaging.” I didn’t even have to give him a snarky look for him to realize that was a less than helpful response as we were standing there.
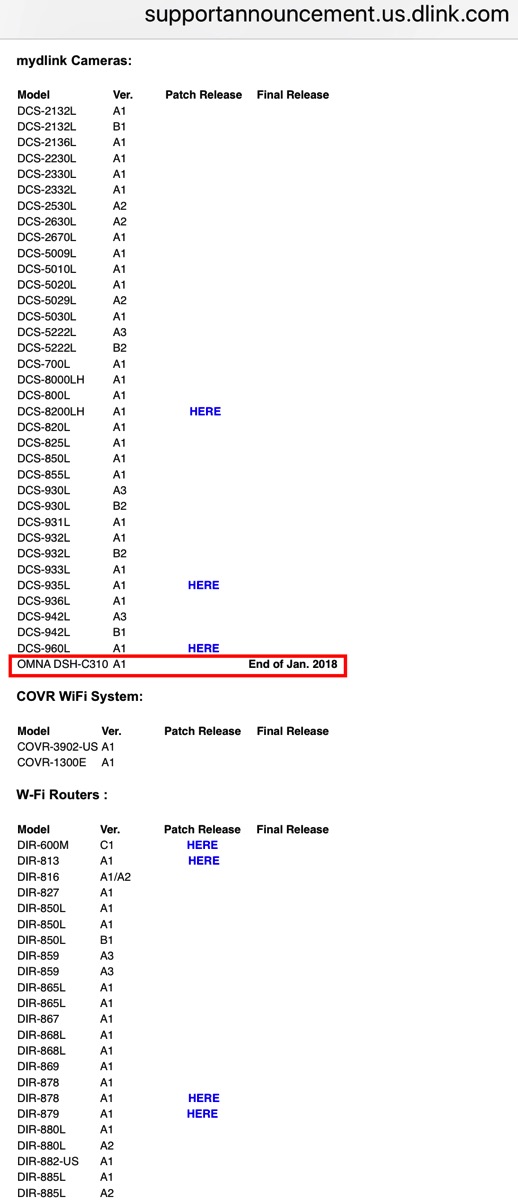 He then hunted around on D-Link’s website until he found the desktop version of the support page about the KRACK vulnerability. This was the page I had been refreshing for three months in hopes of finding a patch for the Omna webcam. The page has a column of part numbers then a column with links to the beta versions of the patches for each device, and a third column for the final versions of the patches. We both looked at the page and saw no reference at all to Omna.
He then hunted around on D-Link’s website until he found the desktop version of the support page about the KRACK vulnerability. This was the page I had been refreshing for three months in hopes of finding a patch for the Omna webcam. The page has a column of part numbers then a column with links to the beta versions of the patches for each device, and a third column for the final versions of the patches. We both looked at the page and saw no reference at all to Omna.
He said that meant the fact that the Omna wasn’t on the page meant it didn’t need the patch. I was confused, because the vast majority of the devices on that page did not show any updates, and I said that those must also not be affected. He said no, anything not showing an update meant it did need a patch but the patch wasn’t out yet.
There are 107 devices listed on that page, and only 27 have beta patches for KRACK and a grand total of zero show final patches. I thought I must be misunderstanding him, it could not possibly be true that 80 devices hadn’t been patched, but he said it was true. He said he’s really frustrated with how long it’s taking.
Yeah. As CISO, it’s kinda his job.
Over the past couple of weeks, I’ve had communications from the D-Link PR people getting me updated information that’s better than what we heard at CES. The good news is they did do a few things because of my conversation with Mr. Brown. First, they added a link to the mobile version of the support site where you can get to the recent news, including the KRACK update page.
They also found the part number for the Omna and discovered it was, indeed on the KRACK update page (but hadn’t been patched). They changed the name to include the word Omna instead of just the three letters followed by numbers, and in that way others could find it. Most importantly, they committed to me to get a patch out for the Omna webcam by the end of January 2018, and they put that date commitment on the KRACK update page.
I’m pleased that my particular device is getting patched, and I’m pleased to make an impact like this, but when they get the Omna patched, there will still be 79 D-Link devices not patched for KRACK.
I wondered how other companies were doing, so I searched for the KRACK security advisory page for Netgear. They show 45 devices vulnerable, and all range extenders, webcams, mesh routers and wireless access points have been patched. There are some other devices that haven’t been patched but the most vulnerable devices have been patched. So it’s not an industry-wide thing that this is taking forever.
I guess I was naïve in thinking that if I went with a big-name router company with a HomeKit-compatible webcam, I’d have some protection in the event of a big vulnerability, but I have to say I’m really disappointed in D-Link.