Long time NosillaCastaway John Shaffer wrote in what he called a Dumb Question a few weeks ago that caught me by surprise. He told me that the VPN service Encrypt.me was combining with one called StrongVPN. He wondered how the change was going to affect the commitment to privacy and security.
I’ve been using Encrypt.me since it was called Cloak, so for at least 15 years and I’ve been a big proponent of it on the podcast. My loyalty to Encrypt.me is so strong that for the roughly 18 months I didn’t leave my house, I kept paying for Encrypt.me because I wanted them to stay in business and still be around when I poked my nose out of the front door. This news from John that they’d combined with StrongVPN was news to me and like John, I was very interested in the future of this product.
I made some inquiries and engaged in a video teleconference with two representatives for StrongVPN. I spoke to Subbu Sthanu, VP of Consumer Product Strategy, and Erjona Asllani, VPN Product Management & Product Marketing. They each brought different perspectives that provided a good background on what has happened so far and where they see the future product development going.
Before I get into any details of the future, the main takeaway from our conversation is that Encrypt will stay in place for current customers for the foreseeable future, but new customers will be directed towards StrongVPN. I believe they really will keep Encrypt around for a fairly long time, and I’ll elaborate on why I believe them.
Background
The biggest thing I didn’t understand coming into this blind is that there have been a lot of mergers and acquisitions over time. I didn’t know that Encrypt had been bought by J2 Global over two years ago. Subbu described a series of VPN-owning company mergers, and I won’t even attempt to replicate how we got here, but J2 Global just changed its name to Ziff Davis.
Now that we have a name for the company that owns Encrypt I can explain why you care if you care about Encrypt. Ziff-Davis now has a portfolio of VPN tools with an array of capabilities from end users who simply want to protect their web traffic when in a coffee shop to higher-level capabilities such as threat intelligence and analysis, security and backup for businesses and more. Subbu emphasized that they’re all about privacy and security. I think at this point, John’s original question about whether the new stewards of Encrypt would continue the commitment to security and privacy was answered.
I asked Subbu whether we could end up in a situation like what Dropbox did to its customers. Dropbox won the Internet’s love by letting us store our data in a cloud service that synced to all of our devices. But then they got more aspirational and started trying to force more capabilities on us, creating a bloated app and providing services many didn’t need or want.
Subbu had a great answer. He explained that while they will be consolidating their end-user VPN tools from three down to one, they are committed to serving this specific market while advancing their broader tools for the business customer.
The three VPN tools they own now are Encrypt, IP Vanish, and StrongVPN. Subbu explained these three brands:
- IPVanish is for the home user looking for a highly customizable and powerful VPN brand
- StrongVPN is for a more technical home user
- Encrypt is for the home user who is looking for a “set it and forget it” option.
The next part of the conversation is what gave me hope as an Encrypt user. Subbu explained that Encrypt has an incredibly loyal user base, and it’s a very lucrative user base, and so they want to make sure they don’t do anything to lose those customers.
Their long-term goal is to learn from the Encrypt customers what it is about the tool that keeps them so loyal and then build those features into StrongVPN. Only when StrongVPN can provide what the Encrypt users need will they start any kind of migration effort to StrongVPN. I don’t think this will be any time soon because they said that StrongVPN had had no new development in four years.
However, he said that Encrypt has a very loyal user base and they don’t want to do anything to disrupt those users. He also said that the revenue from those users is significant. That’s the part that made me believe him that they wouldn’t be dropping Encrypt.me without a clean way to migrate users.
The best part of the call was when Subbu and Erjona asked me to talk about why I’m so loyal to Encrypt and what I find important about it. I explained that the main reason I have been a long-time user is that it’s set it and forget it. I walk into a hotel in Nepal, and my iPhone, Mac, and iPad all turn on Encrypt automatically. Just like a good backup strategy has to be automatic, so does a good VPN tool.
I also said that a critical feature of Encrypt was the ability to add networks to be trusted. When I go to tech-savvy Grandma’s house, I know I can trust her network, and Encrypt lets me set that up so I’m not going through a VPN when I’m visiting her. Once I tell Encrypt to trust her network, I don’t have to take any action when I visit.
I asked to see what StrongVPN looked like.
StrongVPN
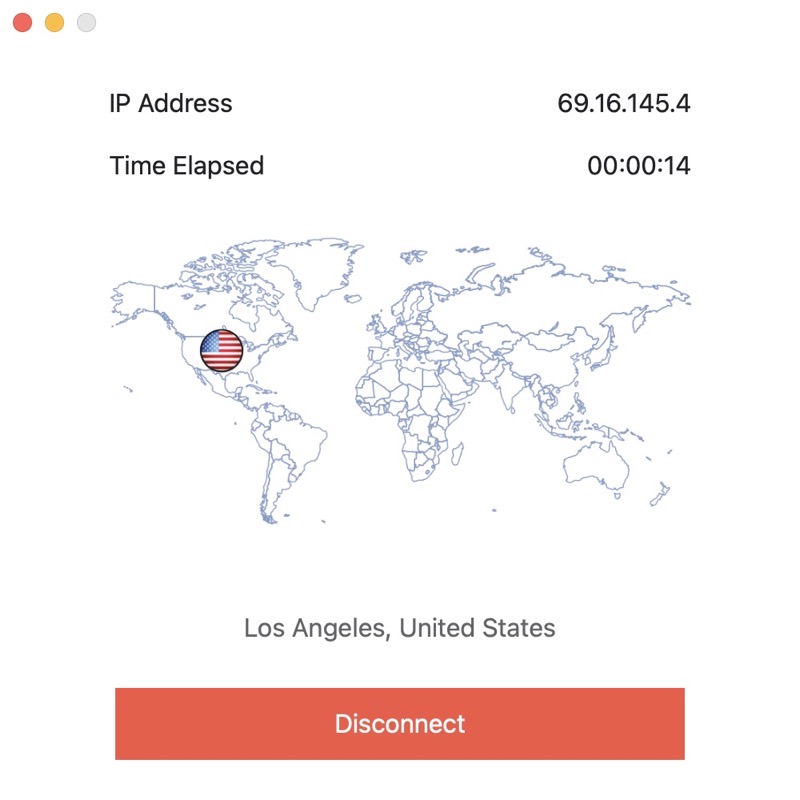
Erjona demonstrated StrongVPN on her PC and her iPhone. StrongVPN also runs on Android and the Mac and iPad. It even runs on the FireTV stick. If you’re comfortable setting up OpenVPN with Linux you can use StrongVPN with it.
Erjona gave me a license for StrongVPN and I’ve been testing it out on my Mac and iOS. The main interface is quite simple. It shows a flattened globe, a country icon over your location and you can choose a server location or Best Available Server, and hit Connect. You can see your IP address changed and the time elapsed you’ve been connected. It’s that easy to use.
If you only go that deep into StrongVPN, you don’t have to worry your pretty little head about anything else. But if you go into Preferences it immediately gets geeky. It’s got a section on OpenVPN/L2TP (which I’ve heard of but don’t understand), you can select IPV6 leak Protection and there’s a Kill Switch. I kinda want to click that just to see what would happen. It gets even deeper on the Advanced tab where it talks about IKEv2 and IPSec and more.
You can set it to launch at login and connect at launch, but on macOS, StrongVPN doesn’t have a way to save certain networks as safe places where it doesn’t need to launch. On iOS, however, buried in a very oddly-named setting, you can tell it what networks to trust. I knew it was in the settings somewhere but I had to ask Erjona where it was. It’s inside On Demand Settings.
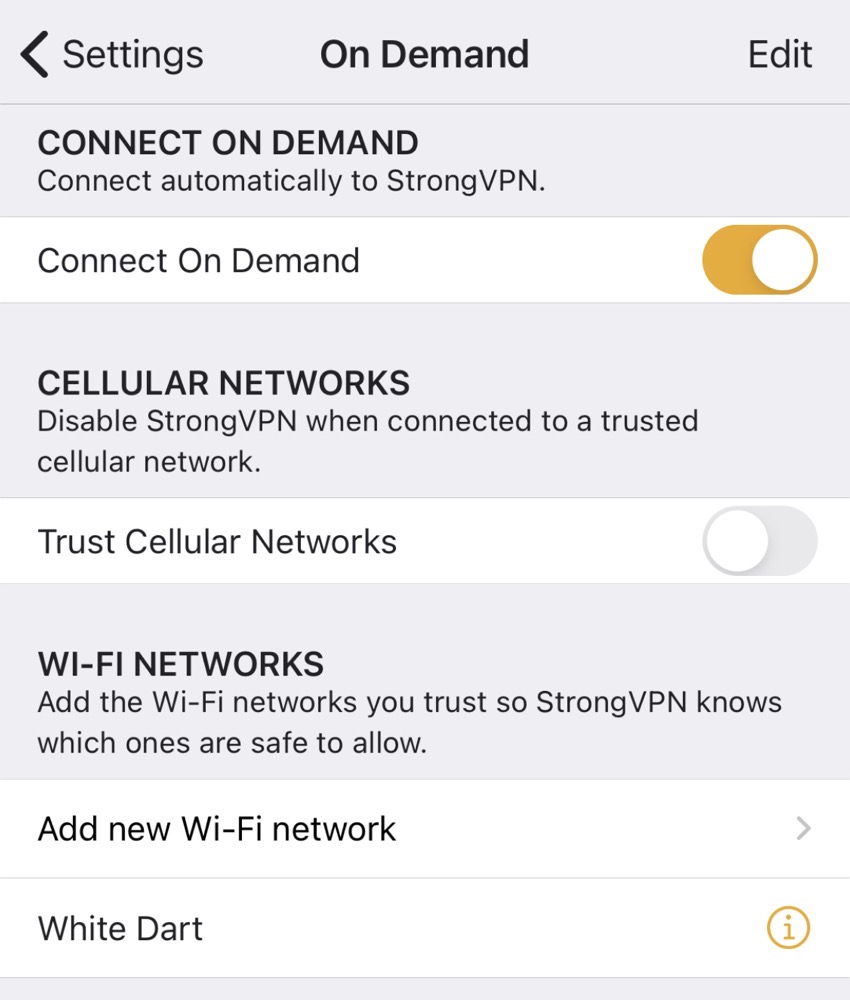
By default when you go into On Demand Settings, you simply have a toggle to connect automatically to StrongVPN. That’s the set it and forget it menu that’s my primary requirement. I never would have guessed, though that this is where I tell it to trust networks because the menu never mentions anything about that feature.
Only once you toggle Connect on Demand, will two new options reveal themselves. You can now choose to trust cellular networks, which is a good switch to have if you don’t think you can trust your ISP to not sniff your traffic. Below that, you’ll now see the option to add WiFi networks you trust.
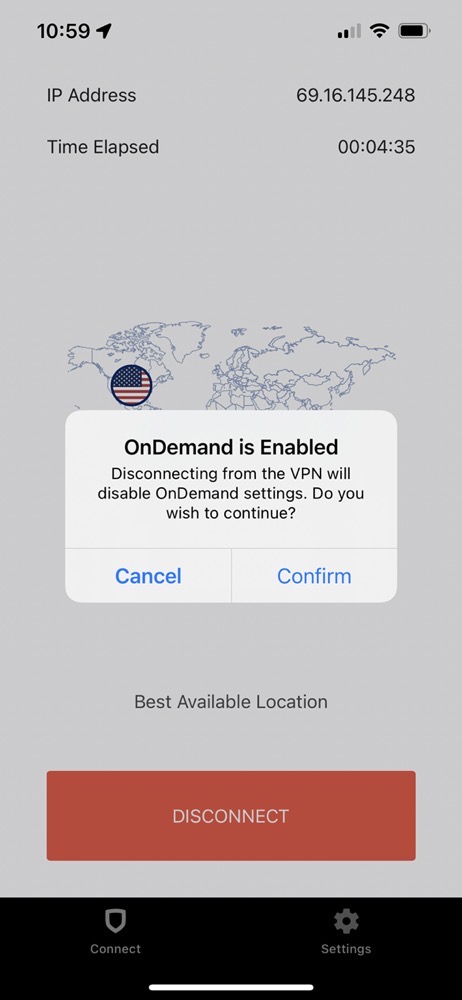
This checks the box for my second requirement, but it’s not as easy as with Encrypt. On Encrypt you’ll see a list of the WiFi networks you’ve trusted in the past, and the one you’re currently connected to is at the top. It even slides itself right to left a little bit inviting you to pick it as the network to trust. With StrongVPN you have to type in the name of the network. I know that’s not a HUGE deal, but it’s a bit tedious sometimes to exactly transcribe a network name with capitalization and spaces and such.
I tested adding my home network White Dart as a trusted network to StrongVPN, and for some reason, StrongVPN took that as a signal to protect my traffic, rather than allowing it. I tried disconnecting StrongVPN and I got a pop-up telling me that disconnection from the VPN will disable my OnDemand settings. Either I completely misunderstand how this works, or I’ve run into a bug.
Either way, as both Subbu and Erjona explained, StrongVPN is not ready for the Encrypt users to embrace. I’m very glad that they’re not going to disrupt Encrypt until StrongVPN is ready.
The good news is that Erjona’s team really wants to hear from you on what you like about Encrypt to help her team drive the changes to StrongVPN to get it ready for us. She gave me an email address for users to send in their feedback directly to the team, so I hope if you are willing to help you’ll write to them at the link in the shownotes:
Bottom Line
The bottom line is that I think you’ll be fine running Encrypt.me for quite a long time, as they’re just now gathering their strategy on how to proceed. You have the opportunity to help guide them in their decisions as well.
With all that said, when a product has been declared end of active development, I really like to move to a new product on my own schedule rather than wait until I have to make a choice in a hurry. Encrypt isn’t abandonware, but it’s also never going to be enhanced, and it will be quite some time before StrongVPN will be enhanced to be good enough for Encrypt users to migrate to it.
I was very encouraged by my conversation with the new team members stewarding this project, but it might be time to see what else is out there that could meet your needs.

I got an Email from customer support that they may not fix bugs in the Encrypt.me iPhone client in the future. Currently the ‘Trusted Networks’ feature does not work because of a change in Apple’s APIs. If they don’t get that fixed it is a total dealbreaker for me
Sigh. That’s a REALLY bad sign, Victor. Would you mind sharing the email with me at [email protected]?
I did see it stumble on trusted networks yesterday when connected to my new iPhone from my Mac, but then I got it to work. Maybe in email (or here) could you describe how it didn’t work for you?
I agree, 100% deal breaker if that doesn’t work (which is what I told them when I talked to them.)
Hi Allison. Taffy and I have been using Encrypt ever since you gave a presentation at SBMUG. We enjoyed it’s automatic operation. However, every so often it reports that the certificate has expired and we would. be off line for a few days, and would have to reset our devices. Not happy with that. Lately, we have not been able to use Encrypt when using Zoom, Webex or Microsoft Teams. It causes constant freezups in all three. So we have to turn it off to continue the conferences. And I also run it at home, even though I know I should not need to, and while reading email, it would stop downloading messages, periodically, and I’d have to wait 30 sec or so before continuing. I’m using Cox ISP, but I don’t think it’s them, because turning Encrypt off solves the problems. So, bottom line, I’m really looking for another VPN. Glenn recommends HotSpotVPN which is what I used to use many years ago. The pricing would work if I include my daughter and her other, for 5 users with 5 devices each. I need 5, Taffy 4 and the other two 3 each. So their pricing would work.
Dick
That’s good to know, Dick. To be honest I’ve only used it once in the last two years and it seemed to work just fine. I’ll add HotSpot VPN to my list of options to try.
Was there any mention about changes to Encrypt.me’s contract with Eero?
No, Charles and I didn’t even know they had a contract with eero!