Last October, alert NosillaCastaway John Shaffer let me know that the VPN I’ve been recommending for many years, Encrypt.me, had been sold to Ziff-Davis. He wanted to know what this meant for the product. I reached out to the folks at Ziff-Davis, and had a nice conversation with them about their plans to incorporate Encrypt.me’s feature into one of the many other VPNs they had purchased.
In my article about the conversation, my bottom line was that I was cautiously optimistic, and that you could keep using Encrypt.me for the foreseeable future. I also said that since it was pretty much end-of-lifed, I’d be looking around for alternatives. Dan Moren came up with a great way to think about end-of-lifed apps during an episode of Clockwise. He said, “I like to quit software applications before they quit me.” I also heard from a few NosillaCastaways that they’d tried to get support for Encrypt.me and they got nowhere. It’s clearly time to find a new VPN after all.
Refresher on VPNs
Before I describe my hunt for a new VPN, let’s make sure we’re on the same page about what problems a VPN solves. This may be a refresher for every single one of you, but I’d hate to leave anyone wondering about this.
When you’re at home, behind your password-protected WiFi (or wired Ethernet), you’re on a private network. But when you go to a coffee shop or hotel, you’re either on a public network or at the very best a shared network with everyone else in that hotel or coffee shop. VPN stands for Virtual Private Network. A VPN allows you, as the user, to send and receive data across public or shared networks as though you were directly connected to a private network.
When on a shared network, man-in-the-middle attacks can easily occur where bad actors spoof real websites in hopes of getting you to give up your login credentials to your bank or worse. With a properly-configured VPN, you won’t be susceptible to those attacks.
Another main use of a VPN is to “tunnel” into your employer’s network. With a VPN from your house to your employer, you can function exactly as though you are at the office with access to internal servers and services.
Many security-minded NosillaCastaways also choose to always run a VPN, even if they’re at home just surfing the net. This use isn’t as much about security as it is about privacy. Our Internet Service Providers (ISPs) see all of the destinations of our network activity. But with a VPN running, they only see that you tunneled out to your VPN provider’s server, but after that, they can’t see where you went.
There are also those who use a VPN to obfuscate their IP address. It could be for nefarious purposes, but it could also be to protect one’s identity in a political regime that is problematic. It can also be used to view content that is restricted in your geographical location. I haven’t ever done that to bypass paying for something (I’m looking at you, Star Trek in Canada on Netflix), but I did once use it to tunnel into Britain because the idiots running the Olympics in the US didn’t air the US women’s gymnastics competition!
Hopefully, that foundation helps you get your brain around why you might want to use a VPN.
The Hunt for a New VPN
It was time to start evaluating VPN offerings that were in active development. This is much harder than you would think. You pretty much have two choices:
- Buy one of the ones advertised by your favorite tech podcasters
- Choose from one of the many “Top Ten Best VPN Provider” lists
The first option isn’t a terrible way to go, because if you hear about a VPN from a tech podcaster, it’s reasonable to assume they’ve used it themselves and done some sort of evaluation. But do you really know anything about those VPN providers? Do you know that the podcaster evaluated them thoroughly from a security perspective? Or are they just the ones that offered advertising money?
The second option is possibly even worse. Unfortunately, many, if not all of these “Top Ten” lists are either paid for by the VPN vendors or are all affiliate links. You know I love me a good affiliate link, but I am pretty good at making sure you know when there’s something in it for me. These Top Ten lists often do not disclose the fact that they are getting paid for what you choose. You really have no way of knowing whether these lists are of good VPNs or only ones that were willing to pay the site owner to be on the list.
I started looking at a few of the podcaster-recommended VPNs and in general, they were quite a bit more expensive than what I have been paying for Encrypt.me. It was pretty obvious that I would need to start paying more, and I was willing to do that but I still wanted to find a way to choose a VPN that truly provided security and privacy.
Consumer Reports White Paper Evaluating VPNs

I was paralyzed about how to proceed. Then a couple of months ago, listener Lynn attended a Consumer Reports session about VPNs. They conducted an exhaustive study on current VPN providers, and published an open white paper on their findings. You can view it at digital-lab-wp.consumerreports.org/… It’s 48-pages long so I mean it when I say “exhaustive study”.
They started by analyzing 200 VPN providers. They culled that list down to 51. Then through their evaluation, they narrowed it down to 16 into which they did a deep dive. And I mean a really, really deep dive. The white paper takes you through, in detail, the security criteria they used to evaluate each of them and how they were quantifiably measured.
They evaluated these 16 VPNs on 6 security criteria:
- Build Quality: Best Build Practices Authentication
- Encryption
- Known Exploit Resistance
- Security Oversight
- Security Over Time
- Vulnerability Disclosure Program
And 6 data privacy criteria:
- Access and Control: Data Control
- Data Use and Sharing
- Data Retention and Deletion
- Overreach/Collecting Too Much Data
- Governance: Privacy Policies and Terms of Service
- Governance: Privacy Policy and Terms of Service Update Notification
As if that wasn’t extensive enough, they also have a list of other issues they looked into on each of the 16:
- Local Logging
- Dark Patterns
- Human Rights and Corporate Social Responsibility
- Logging
- Inaccurate Presentation of Products and Technology
- Ownership
- Transparency Reports
- Complaints
- VPN-Owned VPN Review Sites
- Response to Breaches
- VPNalyzer Issues
It’s a fascinating report, filled with bar graphs showing how each VPN fared on each of the criteria, but there’s a lot of detail I’ll admit I didn’t read. It seemed like a terrific study, but to be sure about that, I posted about it in our Security Bits Slack Channel podfeet.com/slack and asked Bart if he’d take a look. His response was:
First impressions are excellent — these people are on my wavelength, excluding VPNs for ‘hyperbolic ad copy promising “100% security” or “military-grade encryption.“’ is perfect. “Military Grade Encryption” is a particular red flag, it SOUNDS good, but the military is not about cyber security, so it’s like “cheese grade acceleration”, nonsense!
He came back a day or so later:
My curiosity got the best of me. I looked through all the graphs and explanations to figure out why Express VPN didn’t make the top of the list. While they were actually #1 in many categories, these are the ones that they got dinged for. The graphs are color-coded, with descending green down to red. If all apps did well in a category, the range might only be green to pale green, but if some did badly you’ll see all the way to red.
- Pale green (almost yellow) on best build practices
- Bottom of pale green on Authentication
- Orange on Security over time
- Middle orange on Data control
- Super red on Data Retention and Deletion
- Takes three separate button pushes to cancel
I liked Bart’s response for several reasons. Primarily because he’s a good litmus test on whether someone is blowing smoke about security. But he also took a look at a VPN provider that he liked, and found where they fell down. Since I wrote about this in our Slack, a few people told me how they chose their VPN providers and it wasn’t based on this level of fact checking for security and privacy.
If you are content with your current VPN provider, you might want to cover your ears and say “la la la”, or you may want to take a look at this report and see how they did and reevaluate your decision if necessary.
Consumer Reports Bottom Line Recommendation
While all of this detail and nifty graphs were really interesting, I was really hoping they had a bottom-line answer for us. I was not disappointed. The last paragraph of the 48 pages is entitled “Recommendations for Users”.
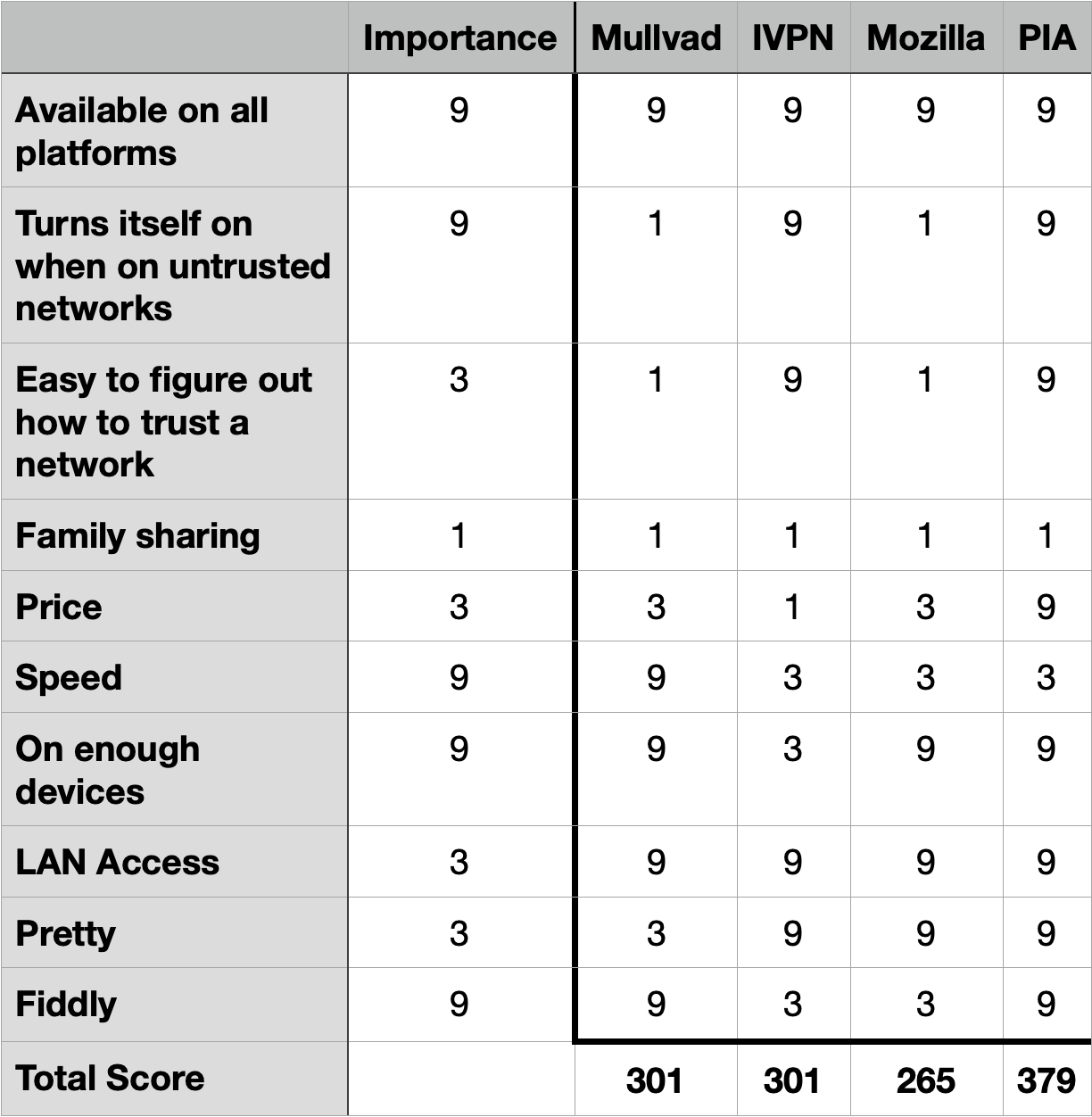
Of the 16 VPNs we analyzed, Mullvad, PIA, IVPN, and Mozilla VPN (which runs on Mullvad’s servers)—in that order—were among the highest ranked in both privacy and security. However, PIA has never had a public third-party security audit. Additionally, in our opinion, only IVPN, Mozilla VPN, and Mullvad—along with one other VPN (TunnelBear)—accurately represent their services and technology without any broad, sweeping, or potentially misleading statements.
Allison’s Evaluation of the Top Four
Now that Consumer Reports had done all of the heavy lifting to narrow down the playing field, my plan was to pay for and install the four finalists and evaluate them against my own criteria. PIA was ranked second of the four, but with a caveat that they’ve never had a public third-party audit. Knowing that these companies had done well in such rigorous evaluation of their security and privacy practices, I knew I didn’t have to worry my pretty little head about that part of the decision process.
All of the four are open source, which is cool because it means security researchers can poke their curious little noses into the code to see how it works.
QFD Process
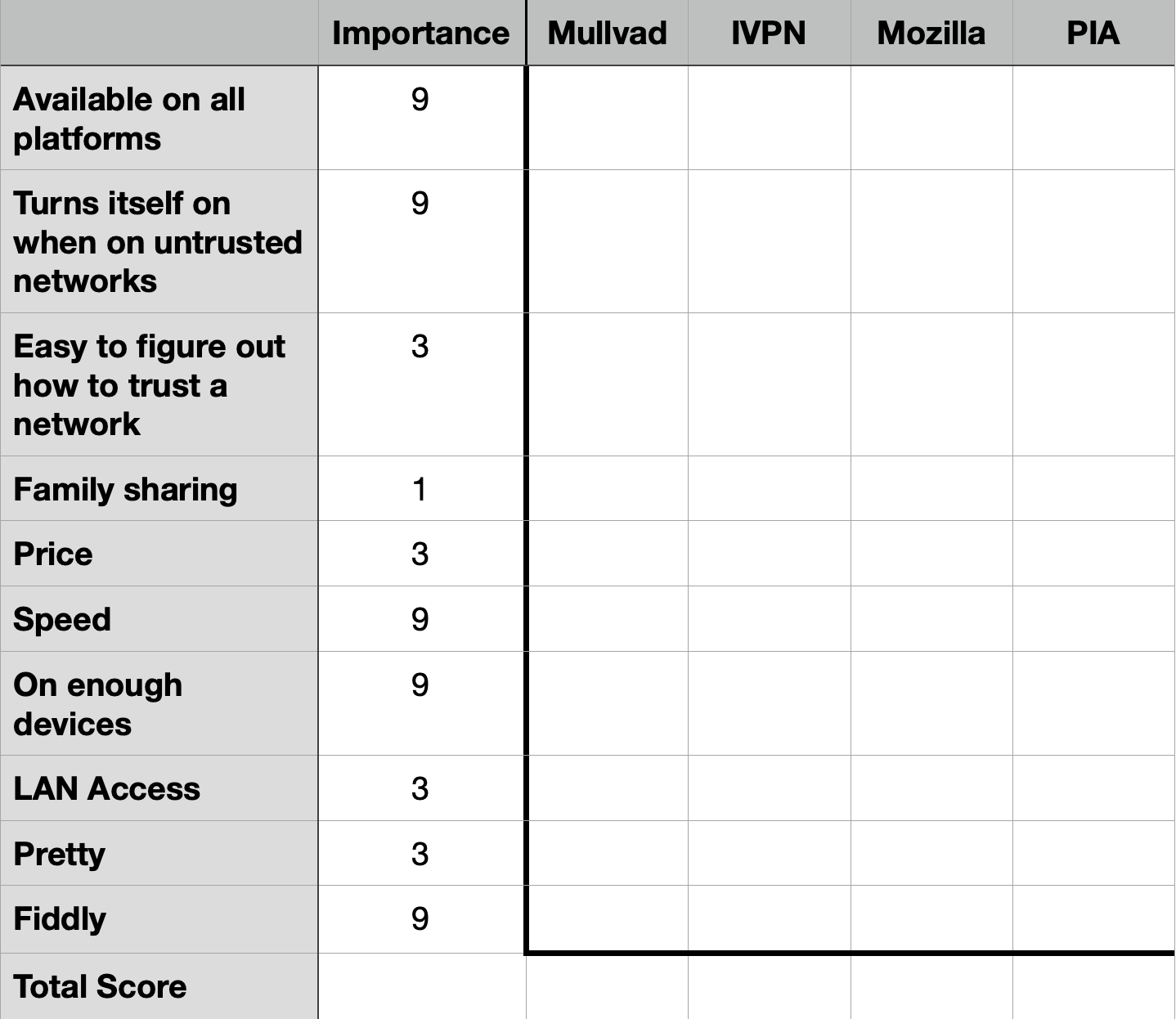
When embarking on a project like this, I think it’s important to lay down the criteria before you start testing. It’s very easy to change the criteria to match the one you like, instead of evaluating every option on its own merits. I like to use a process called a QFD (Quality Functional Deployment).
I made a video back in 2015 demonstrating how you can use a QFD to make decisions. For the serious QFD experts, this will annoy the heck out of them, but I like my heavily simplified version of the concept.
At its very basic level, you create a list of criteria. You give each criterion a weighting value based on its importance to you. You are only allowed to assign a weighting of 1, 3, or 9. You can’t use 1, 2, 3, or 1 to 10; it has to be 1,3,9. The purpose of this odd numbering system will become obvious in a moment.
Once you have the criteria and their associated waiting values, you start to evaluate your different options (in this case the four VPN apps) and assign a 1, 3, or 9 to how well that option meets each criterion. When you’re done evaluating an option against all of the criteria, you multiply how well an option met a criterion against its weighting factor and then add them all up. By using this 1, 3, 9 method for both the weighting and how well an option met the criteria, the final tallies for each option should spread farther apart than with linear values, making the one true answer more obvious.
Describing that QFD process is much clumsier than if you just see the math, and, trust me it works really well. Be careful not to get overly zealous and say everything is a 9, or you won’t get any differentiation. Sometimes you must, but try to avoid it if possible. Also, remember that while I’m using this rigorous math to help my decision process, the values I’m assigning will be in many cases subjective. Sometimes a feature exists or doesn’t exist but often it’s squishier than this. The importance value is also subjective, but this decision tool can help reveal an answer you didn’t expect.
Since I don’t have to worry about evaluating the four VPN offerings for security or privacy, I’m free to make up my own criteria. I chose:
- Available on all platforms (macOS, iOS, iPadOS, Linux, Windows and Android)
- Turns itself on when on an untrusted network. This is so I can set it and forget it, and if I walk into a coffee shop it turns itself on, but never at home.
- Easy to figure out how to trust networks (Encrypt.me had this feature but it was baffling each time I had to find the setting.)
- Family sharing – I want to cover Steve and me at a minimum; my kids if it’s affordable (it was affordable with Encrypt.me)
- Price – with or without family sharing, price does matter
- Speed when connected to the VPN
- Available on enough devices at a reasonable price (some are for 2 devices only; isn’t that adorable?)
- Pretty – hey, it’s my list, I can ask for pretty too!
- Fiddly – the last thing I want in a VPN is fiddly or I’ll turn it off
You may have completely different criteria, but these are what’s important to me. I set weighting values of 1, 3, or 9 for each of these criterion and got to work.
Testing
I paid for one month’s usage of each of the four VPNs: Mullvad, IVPN, Mozilla VPN, and PIA. I installed them on my Mac and on at least one iOS device. Probably the most important lesson I learned was that on iOS, only install one at a time! Sure, that sounds obvious now, but I still had Encrypt.me’s profile on my iPhone plus I added 2 or 3 more before I realized it was the root of the fiddliness I was starting to experience.
We’ll get to my quantified analysis in the QFD at the end, but I’d first like to describe my experience with each one.
Mullvad
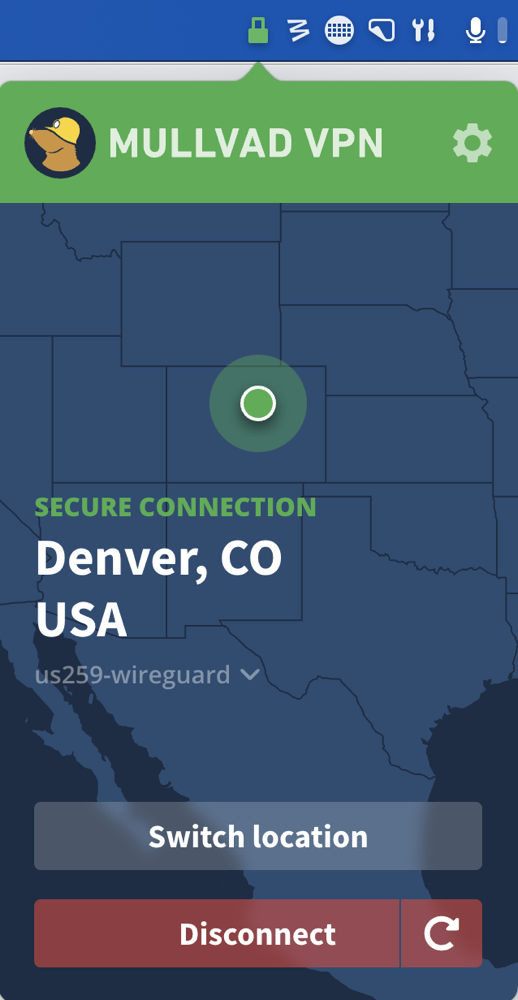
Mullvad doesn’t require you to create an account; they simply give you a unique account number. They don’t even get your email address. You can pay with a credit card but you can also pay with cash or cryptocurrency. In fact if you pay with crypto it’s actually 10% cheaper than any of the other methods.
For some reason, Mullvad’s credit card payment page would not work with Safari, so I had to fall back to using Microsoft Edge. Their pricing is 5.50€ per month no matter how many licenses you want, or however long you want them. They are very proud of this static pricing system that has been in place for many years without an increase. 5.50€ is currently $5.37US per month, which works out to $64/person, or $129/year for our family of 2.
I downloaded and installed Mullvad and was delighted by the icon for Mullvad. It’s a mole wearing a hard hat with a light on it. Get it? Tunneling?
Mullvad also includes ad blocking, malware blocking, and more, all within the VPN app. This was the first app I tested, and I noticed that I could choose either WireGuard or OpenVPN to make my VPN connection. As I worked through the 4 different VPNs, I realized that with the exception of Mozilla VPN they all offered both, while Mozilla VPN offered just WireGuard. I didn’t know why I’d care about that so I asked Bart. He said:
WireGuard is newer, more efficient, and better designed. It’s the cream of the current crop. It’s So good Linus incorporated it straight into the Linux kernel!
Luckily all four of the contenders have an option of WireGuard, so if it’s good enough for Linus Torvalds, the inventor of Linux, it’s good enough for me! The one reason I can imagine you might want to use OpenVPN is that you can put it on many home routers and NASs, so maybe a client that supports OpenVPN would be an advantage. If so, eliminate MozillaVPN from your list.
With Mullvad, you explicitly tell it where you would like to connect. For example, I am in California, and I can choose Los Angeles. From there I can choose from 20 or more different servers in Los Angeles. However, I am not shown any information on whether that is a good choice. With some of the other offerings, servers in Las Vegas often had less latency than the ones in California. I’ll give Mullvad high marks for lots of servers, but low marks for information about those servers.
The interface is very bold and striking. Mullvad is a menu bar app like some of the others, and it has a bright red unlocked lock as an icon that turns bright green and locked when you’re connected. If those bold colors bother you, you can make it muted and less recognizable in the Settings. Mullvad has a dark map showing your location with a bright red banner and a bold, green “secure my connection” button.
If you prefer a subtle, modern UI, you’ll hate Mullvad. If you long for the days when you could tell your application windows apart and your menu bar items apart, you’ll bask in the glory that is the Mullvad UI. I would have trouble calling it pretty but you could call it bold. As the Podmom used to say, “beauty is in the eye of the beholder.”
As I mentioned earlier, one of my criteria was that my VPN should automatically protect my connection when I’m on an untrusted network, but not engage when I’m on a trusted network. I couldn’t find any settings for that with Mullvad, so I reached out to them.
Eric from the Mullvad team got back to me very quickly and explained,
We do not have such a feature as we don’t believe it’s good practice for security. It’s easy to spoof an SSID to trick your device into being in “safe mode”.
I decided to run this by Bart, because my initial thought was that there’s no way that a bad actor in a coffee shop would know the name of my home WiFi SSID, so the chances of them being able to spoof it is significantly lower than the chances I’ll forget to turn on my VPN if it’s not automatic.
Bart’s answer was really interesting. He said I was correct that they wouldn’t be able to figure out my home SSID, but the answer could be very different for other people. He said that large companies (and even small companies) can have the same SSID for the entire company. He suggested someone could go into the lobby at an Intel office, see the SSID being offered, and then go to a nearby coffee shop and set up that SSID spoofed. If you trust your work network and don’t VPN, then your VPN might not turn on.
He also said that Universities throughout the Western world have one single SSID: “Eduroam”. The idea is that if you’re doing research at a university, you should be able to just hop on the network.
I had no idea that SSIDs were so broad! When I retired from a defense contractor, WiFi was not a thing, and may not even be a thing for that kind of company.
I’m still going to keep this as one of my criteria because the danger probably doesn’t apply to me and because the chances of me forgetting are so much higher. I encourage you to think about whether you want to use this kind of feature based on Bart’s explanation.
Mullvad, and many, if not all, of the other three I tested, have a feature where you can enable local area network sharing. This is pretty nifty because it lets you have access to things like printers and other networked devices. When I mentioned it to Bart, he pointed out that turning it on is essentially the same as saying you trust everyone on the network. I hadn’t thought about that! I asked him what the point of it is then.
He reminded me that some users choose a VPN for privacy so their ISP can’t see where their traffic is going, and some users want to appear to be from a different IP address, thus changing their apparent location. In both of these cases, you might want to maintain your local area network access.
But if you are going to use a VPN to protect yourself from ne’er-do-wells on open WiFi networks when traveling, you’d be best to keep that LAN access switched off.
IVPN
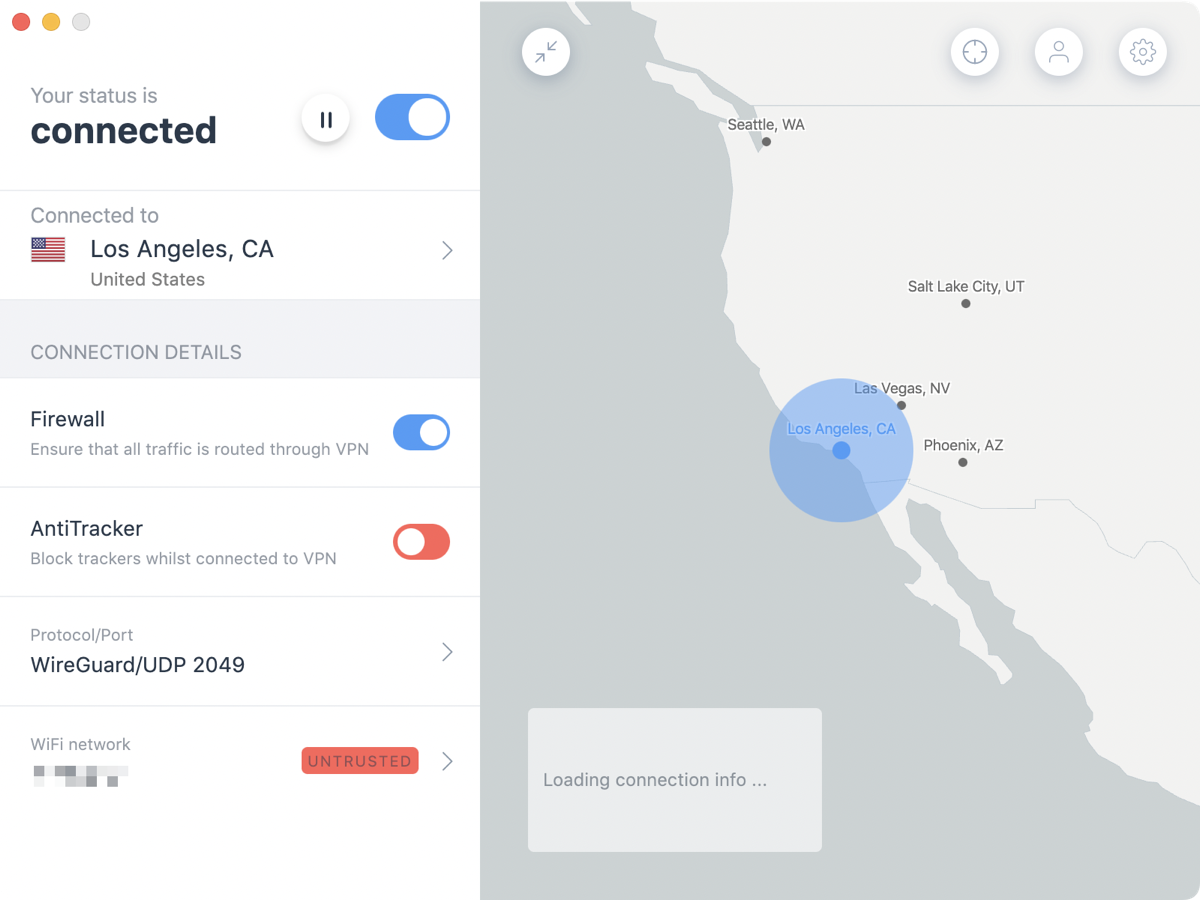
Not only does IVPN work on Windows, macOS, Linux, iOS, and Android, they have versions for compatible routers, along with Synology and QNAP network attached storage devices using OpenVPN.
They have two pricing plans: Standard is for 2 devices and Pro is for 7 devices. I suppose I’m a pro because I travel with at least a Mac, iPad, and iPhone. If you pay annually, the 2-device plan is $60/year, and the Pro plan is $100/year. Steve only travels with 2 (he hates the iPad), so for the two of us it would be $160/year. That makes IVPN the most expensive of the four offerings, at least for our family of two.
Like Mullvad, IVPN is an Electron app. IVPN is beautiful. It is smooth and responsive, and the menus are very clear and obvious to follow. IVPN does allow you to trust networks and will automatically toggle on and off as appropriate. I have a guest network on my Eero router, so I was able to easily test switching between my trusted main network and the untrusted guest network.
Sadly, IVPN on the Mac got fiddly on me. I’d try to toggle it on, and the toggle would flip on and then immediately off. At the same time, I was testing it on the Mac, I was testing it on my iPhone, and the phone worked without any trouble.
I wrote to IVPN and Edward got back to me very quickly. His response was:
Networks are different. If you cannot connect or experience connectivity issues while being connected, this may indicate a network issue. The issue may also occur if the network provider (ISP) is shaping or throttling the VPN traffic on a certain protocol/port. One way to get past such restrictions might be to tune the connection. Fortunately, our app makes this tuning very easy:
https://www.ivpn.net/knowledgebase/176/How-do-I-change-the-port-or-protocol-used-to-connect.htmlOpenVPN and WireGuard both offer a selection of ports. It might be prudent to test all of these ports to determine the one which works best on your current network and allow the connection through.
You might also consider trying a different server location or two. Network routing can be weird and using a server location that is far or farther away might bypass whatever is restricting the traffic.
While this was very helpful and specific, it doesn’t explain why the iPhone was working and the Mac was not. He suggested that maybe the iOS app was running a different protocol or port that was allowing the connection.
The second problem with this answer is that I don’t want to have to know all of this. I don’t want to know about protocols and ports. I am capable of understanding this, but I don’t want to. I want to walk into Starbucks and my VPN go on, and walk into my house or tether from my phone and have it go off.
I was sad about IVPN because it really is beautiful, and it has the trusted networks option, and I love that it has a simple “Fastest Server” option so I don’t even have to figure out whether Las Vegas is faster than Los Angeles, it did all the work for me. It’s very expensive if you need more than 2 devices, and I verified that their terms don’t allow multiple users to share a 10-device plan.
Mozilla VPN
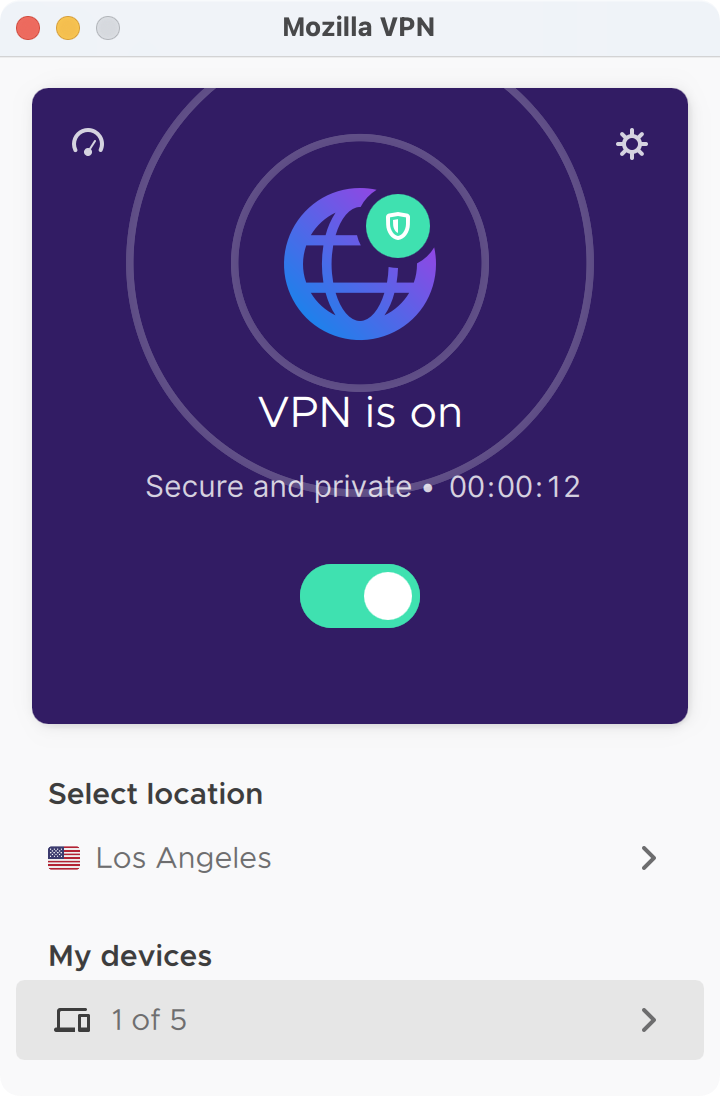
Mozilla is a name that’s near and dear to all of our hearts as the creators of Firefox, so I was glad to see Mozilla VPN in the top four contender list.
Mozilla’s pricing is simple and in the mid-range at $5/month if paid yearly which works out to $60 per year per person, for a very reasonable 5 devices per person. For the two of us, we’d be looking at $120/year.
Mozilla VPN has probably the simplest interface. It’s also a menu bar app and has a simple toggle to turn on the VPN. It shows you how many devices out of 5 you’ve connected to the service, and you can trash them right from the interface to free up some slots if you need to.
To choose a server, you can search by country, and then you’ll be shown a list of servers in that country. The tool doesn’t provide you any information on the latency of the server you’ve chosen, but in my speed test of the Lost Angeles server it provided was right in the pack with the other VPN providers
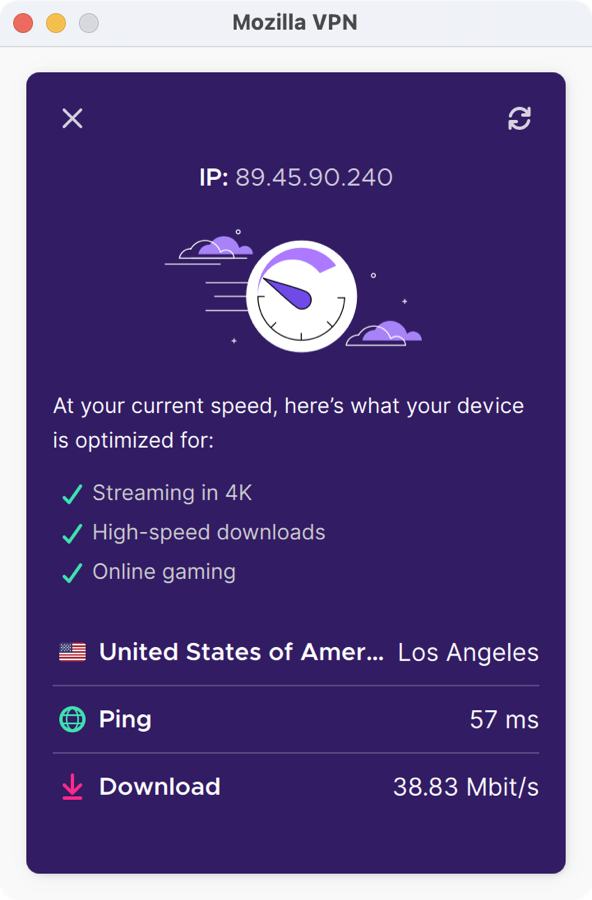
Mozilla VPN has a built-in speed test tool. I didn’t find that in any other of the VPN tools I studied. I wish they all had this feature.
There are very few options with Mozilla VPN, and I couldn’t find a way to trust networks. I reached out to Mozilla and like the others, I got a very quick response to my query about the feature. Ed explained that they don’t have that feature, but suggested that I share that request with the development team. That’s a really great answer for an open source project. He thanked me and he explained how to add this to their tracking system for requests.
While that was swell, I don’t really want to wait around for a feature request, I need a solution right away.
There’s one more interesting thing about Mozilla VPN. It runs on Mullvad’s servers. Not a ding on it, just an interesting thing to note. If you’re not happy with Mullvad’s server selection for your area, then Mozilla VPN wouldn’t provide you with better service.
PIA – Private Internet Access
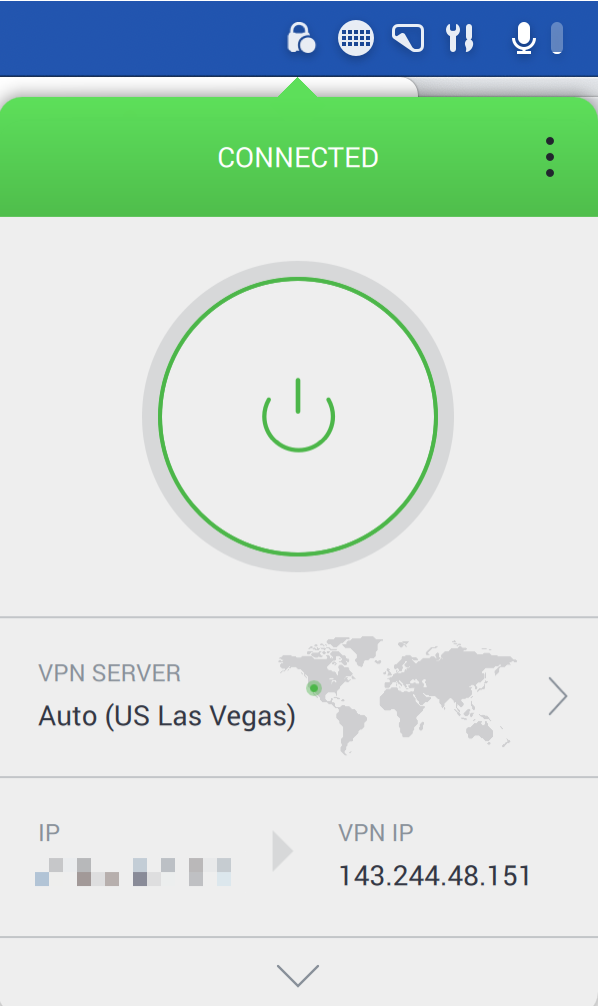
The final contestant in the top four is PIA. This offering, like all of the other VPN providers, works on all of the major operating systems, but they had one more that might meet your needs; PIA has a ChromeOS client.
PIA offers different commitment lengths that can help decrease the cost. They have options for month-to-month, six-months, two years, and three years with correspondingly decreasing pricing. Month-to-month is around $12/mo, going all the way down to barely over $2/month for a three-year commitment. I do need to give one caveat on the pricing. As of the time of this writing (May 2022), PIA is working on some problems with the promotional page pricing. Steve discovered that when we went to privateinternetaccess.com/…, he was offered a two-year plan and a six-month plan, while I was offered a one-year and three-year plan. We also saw slight differences in the prices we were offered (off by a nickel). I reached out to PIA and they explained that they were aware of the problem and actively working to fix it.
In any case, the one-year price of $3.33/month for 10 devices, is only $40/year. For Steve and me, that would be $80/year. If we wanted to go even cheaper, they have a 3-year plan for only $2.19/month or $26/year per person. Even at the 1-year commitment level, that makes PIA significantly lower than the next lowest VPN. It’s half the price of IVPN, the most expensive of the four. When I saw the price of PIA, I was really hoping I’d like it. I kept using my QFD though to make sure I was consistent with what I said was important, and the price was only weighted with a 3, not a 9.
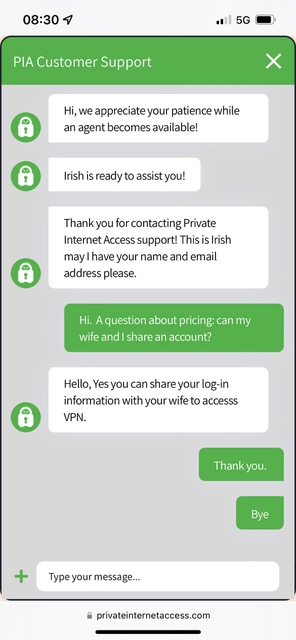
When I created my account with PIA, they sent me a user name and password in plain text through email. That seemed pretty odd. The password they created was only 12 characters long with no special characters. I’m not sure how critical it is to have a secure username and password, since we know from Consumer Reports they don’t do any logging of information, but I immediately changed the password to something much more secure. I discovered that they offered two-factor authentication which I also enabled.
PIA has a very pretty interface. As a menu bar app, it’s very smooth and clean-looking. There’s a giant power button on the screen with a colorful ring around it, designating your connection status on the VPN. Below that is a flattened earth map with a green dot to show you your chosen server’s location. By default it set itself to “Auto” which was perfect, finding that Las Vegas was the fastest server near me.
A chevron to the right reveals the servers it has listed in ascending milliseconds of latency. Interestingly, Panama was the same latency (60ms) as Las Vegas. Ironically, the fastest California had to offer was 91ms, and Honolulu, Hawaii was faster at 77ms! In later tests on my iPhone, Melbourne Australia was responding faster than Los Angeles! I think this is an important lesson that it’s not necessarily the closest server that’s the best server, so a VPN that chooses for you might be the best way to go.
One of my favorite features of PIA is that it shows you your real IP address and the IP you have through the VPN. A colored ring telling me I’m connected is swell, but seeing that VPN IP saves me a trip to ipchicken.com to verify my VPN IP as I’d been doing with other VPN apps.
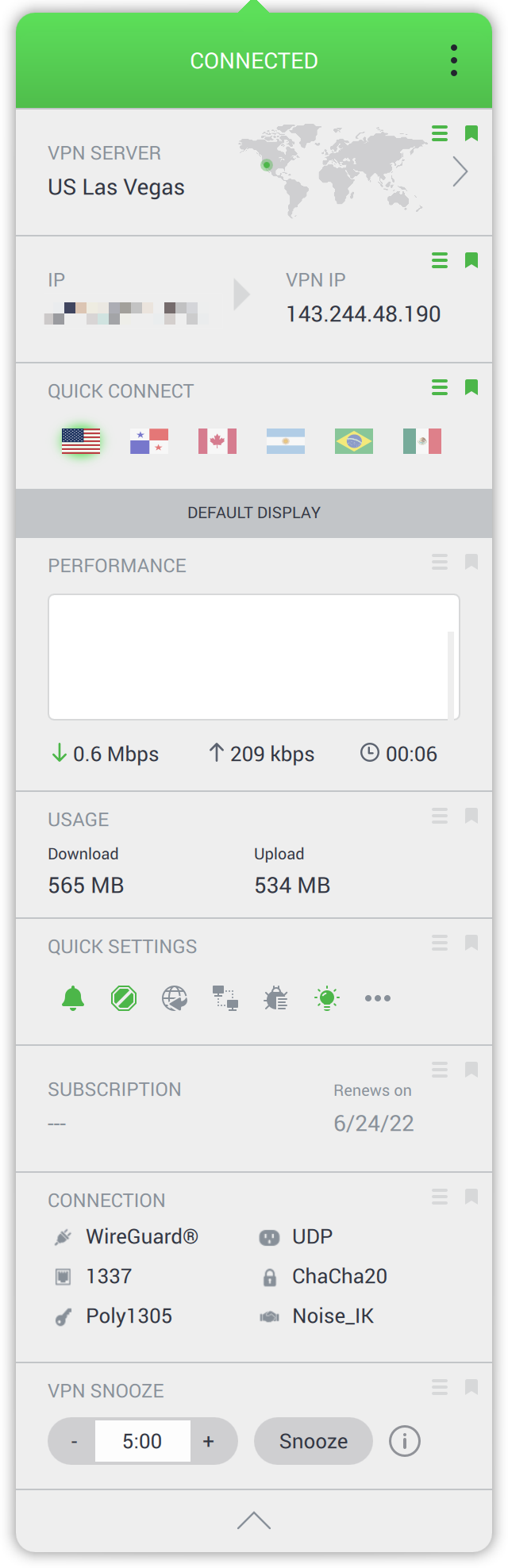
Next is a set of country flags for Quick Connect so I can tap on Panama to connect if I want. Below that is a chevron to reveal more real-time information than any of the other VPNs. You get a graph of performance. You can see how much usage you’ve had both down and upload.
PIA has a plethora of easy-to-understand settings in its main settings window. But you can also access six of the most common settings in the menu bar app as little buttons you can toggle for quick changes. You can toggle desktop notifications, light vs. dark theme, allow LAN access (remember it’s dangerous but if you need it, it’s a quick toggle away), and more.
You can see when your subscription renews too which is pretty darn polite of them. You can also see a lot about your connection and the protocols it’s using. Finally, you have a little VPN snooze button. You know sometimes you just need to get off the VPN for a minute or two to do something locally, so this is a real handy feature. There’s a 5-minute timer you can change to set how long you want to snooze so you don’t forget to turn it back on.
Each of these sets of info I’ve described has a little grab handle on the right which means you can rearrange them to put them above the fold and even all the way at the top. It’s a fabulous and intuitive interface with tons of information if you want it, and very minimalistic when you don’t.
After all that, I haven’t even told you about the actual Settings! There are nine separate settings panes. Luckily for you I’ve already gone pretty long in this article so I’m not going to explain them all.
I will tell you that they have a section entitled Automation, and that’s where you can set up trusted networks. They have two stock automations – what to do on protected WiFi and on open WiFi networks. If you would prefer being disconnected on protected WiFi and connected on open WiFi, you can do just that with automations. I chose to always turn the VPN on for both of those scenarios and added an automation rule to trust my home network. I didn’t even have to type it in as it was the network to which I was currently attached.
The only thing that would have made me like PIA better would be if those automations synced across to my iOS devices as they did with Encrypt.me. I’m betting the carefulness they have with our data, like not logging information, keeps them from being able to do that. It’s really easy to make these automations so it’s not a big deal.
Speaking of automations, PIA also offered to set up a Siri Shortcut to connect and disconnect from the VPN. That was really nifty.
Once I was in love with PIA, I got serious about testing it on my Mac and iPhone, and iPad. I wanted to make sure that it was actually reliable about connecting and disconnecting correctly on the two WiFi networks I used for my tests.
I promised I wasn’t going to tell you about every feature, but there’s one more I want to at least draw your attention to. PIA has created a technology they call MACE. The purpose of MACE is to stop cross-site script tracking, but they don’t do it the way an ad blocker would. The explanation is rather involved so I put in a link to the article explaining how clever it is. helpdesk.privateinternetaccess.com/…
I didn’t test every one of the VPN offerings for accessibility, but I’m delighted to report that I found no features that I couldn’t access via VoiceOver on PIA. Every button was labeled, and there wasn’t excessive faffing about to get into each of the settings from the menu bar app to the dedicated Settings panel.
Speed Tests
As I went through each of the VPNs, I filled in my little QFD decision tool, and there was one more thing to check – how fast are these VPNs? I found a site called fast.com which will very quickly run a speed test and show your download speed. It doesn’t have anything else on the page except the speed and a retry button, so it’s an easy and quick way to find your speed.
I ran three tests of my network without any of the VPNs and found my average speed at that moment. I also made a note to call and shake my fist at my ISP Frontier because I’m only getting 59 Mbps when I’m paying for 100 symmetrical. Anyway…
I then turned on each of the VPNs and ran 3 tests and averaged those results. Mozilla VPN was the fastest at 52 Mbps using a Los Angeles server, while the other three were all clustered from 40 to 44 Mbps. Mozilla VPN is supposed to be using Mullvad’s servers but for some reason, Mozilla VPN was actually more than 25% faster than Mullvad in this rather limited test. I think more data points from more locations would have been more scientific. I think the important point is that all of the offerings, while slower than my un-VPN’d connection, were all pretty darn fast.
The Bottom Line
It’s time for the bottom line. I’m guessing you can tell which one I’m going to go with, and if you guessed PIA you would be right. It scored a 379 on my QFD, while Mullvad and IVPN tied at 301, with Mozilla VPN bringing up the rear at 265.
PIA is gorgeous, easy, and intuitive to use and configure, it’s fast, it’s accessible, it offers trusted networks, and it’s by far the least expensive of all the offerings.
I wanted to choose my VPN provider with completely unbiased security and privacy review and Consumer Reports gave me with exactly what I needed to get started. I hope you find a VPN provider you can trust and if you haven’t yet, hopefully, this article will have helped you consider how to do your own research into the best one for you.
If you decide to blindly follow me and go with PIA, they gave me a referal link that will add 30 days of credit to your paid account and to mine: Allison’s Referral Link to Private Internet Access. I am not in any way suggesting you should blindly follow me, but if I made a compelling argument for their service, why not share the savings?


Allison, as a long-time Cloak VPN / Encrypt.me user I, too, am wondering where to move next. The Encrypt.me homepage clearly states that ”Encrypt.me is combining forces with StrongVPN” and users are directed to ”head to StongVPN to get started” by clicking on the Big Orange Button labeled ”Continue to StrongVPN”.
I wonder about PIA because it is owned by Kape Technologies, which also owns Express VPN and CyberGhost. As with Ziff, Kape has to develop a future strategy for multiple VPN products. Will Kape cause PIA and Express VPN products to ”combine forces” as Ziff is doing with Ecrypt.me and StrongVPN? Also, Kape Technologies has a history of malware problems when the company was known as CrossRider. (See article referenced by link below.)
https://www.cloudwards.net/kape-technologies-buys-expressvpn/
Thanks Allison, I joined on the back of your reasonably vigorous analytic work, as it’s time consuming work looking at all the details of these things.
After signing-up to PIA last month –3-years deal: £65.00 ($80)– I just received an interesting email about their latest privacy audit, competed by Deloitte (one of the so-called ‘Big Four’ auditing firms), confirming their “100% No Logs policy”.
Here’s the ling to their blog about it, for anyone interested:
https://www.privateinternetaccess.com/blog/privacy-audit
I have discovered that PIA, even when it is not turned on, conflicts with iCloud Private Relay. I understand that when a VPN is enabled that iCloud Private Relay will not work. However, I was surprised that just by installing PIA causes the conflict on the Mac with iCloud Private Relay. I did not have that problem with ExpressVPN.
Have you experienced that as well or do you not use iCloud Private Relay?
Mullvad got a 9 on speed and Mozilla got a 3. You stated in the text that Mozilla was the fastest VPN though. Did I misread something?
Even if Express VPN and CyberGhost are both owned by Kape Technologies, I have my doubts about PIA. Kape, like Ziff, must plan ahead for numerous VPN offerings.