ConnorP reviews Instacast (the greatest podcast listening solution EVER) from vemedio.com. I review the HP Veer 4G cellphone running WebOS. Sign up for early notifications from Blue Mango Learning about Clarify at bluemangolearning.com/clarify. In Dumb Question Corner, David asks for the right application to create a logo for his school club, and Professor Albert asks how to send an email to all of his Facebook followers. In Chit Chat Across the Pond Bart explains Digital Signatures by explaining the building blocks of asymmetric encryption (AKA public key encryption) and hashing functions (AKA digital digests).

Hi this is Allison Sheridan of the NosillaCast Mac Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Macintosh bias. Today is Sunday June 12th, 2011 and this is show number 316. We have a lot of fun in store for today, include Bart again on Chit Chat Across the Pond where he’s going to teach us about hashing functions, asymmetric encryption, digital signatures and digital certificates. It’s fascinating! We’d better get the show on the road.
Instacast from Connor
Let’s start off with a listener review by our old pal Connor:
Instacast – $1.99 – greatest podcast listening solution EVER:
Link to Instacast at vemedio.com and
Link to Instacast in iTunes
How to get your Podcasts out of iTunes and into Instacast: vemedio.com/support/instacast/faq/how-to-get-your-podcasts-out-of-itunes-into-instacast
Connor P can be found at: http://connorp.me/, @connorpj1 on Twitter and on the International Mac Podcast at impodcast.tv
HP Veer 4G Cellphone
I’ve had a chance to test out the HP Veer 4G cell phone – the baby brother of the HP Pre3, both of which run WebOS (the operating system for which they bought Palm). The HP Pre3 isn’t out yet (and neither is the promised TouchPad which will also run WebOS) but you can actually buy the Veer 4G today. This is a smart phone, a really really tiny smart phone. It’s 3.3 inches tall by 2.1 inches wide and six tenths of an inch thick. Let’s make that a little more vivid, it’s the size of a credit card, and a little thinner than a deck of cards. It’s got a nice curved back and corners, with a real nice soft surface. It pretty much feels like a pleasing worry stone in your palm.
The real question is whether you can make a usable smart phone in a package that small? Let’s take a look at the OS and the device to get that answer.
The screen covers the entire front of the device, which means it’s screen is the size of a standard Blackberry screen, but about half the size of an iPhone screen. It’s a very responsive touch screen with a slide out keyboard.
On the first day of the All Things Digital Conference, my iPhone dropped out of my purse onto a brick walkway and the screen shattered. Luckily I had just gotten the Veer 4G so that forced me to see how easy it was to use.
The Veer launches apps quickly and the app store at least passed my test of finding a free Twitter client, I chose the one called Spaz. That’s a good name right there. Having a Twitter client means it beat the Blackberry Playbook, right?
The WebOS didn’t seem too hard to get used to, but a lot of the people I show it too think it’s not very intuitive. The main thing to get used to is that you swipe up from the black area under the screen to get to your applications. You’re presented with a classic grid of apps, and swiping right and left lets you move through the categories of apps. Once you have a few apps running, you swipe up from the bottom which reveals your running apps as “cards”, and now swiping right and left flips between the apps. It took me a while to figure out how to actually close an app (I think I might have had to google for it), you swipe up on the card for the app. This gesture was the only one I found a bit dodgy. At first I was sure you had to do it fast enough or it would bounce back on screen. Then I thought it was that you had to go slowly or it would bounce back, then I tried sort of a flick of the wrist…but I’ve decided it’s random now whether it will actually close the app or bounce back on screen. Try enough times and it eventually goes away. One more gesture to learn – to go back within an app, you swipe to the left. For some reason I always wanted to swipe to the right instead though.
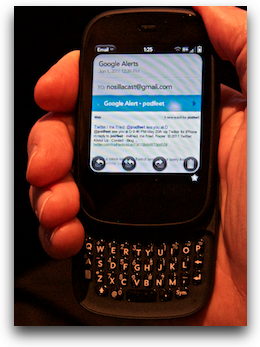 The keyboard is about as tiny as you can imagine, but the keys are made out of this sort of sticky plastic, so you can push the keys with your fingernails and they don’t slip off. I can’t pretend it was a good experience, but it wasn’t nearly as bad as you would think when you first look at the keyboard. I did a fair amount of tweeting during the conference and I actually got pretty good at it. I’m also not going to lie to you, that screen is really small. If I’m wearing my glasses I can read it easily but the text is teeny weeny. I set up my gmail in the built in email client (see RIM? you have to put this in your OS) and for some reason the text was microprint. I searched all through the system for some way to control the font size but I never found an option. A couple of days ago I went to show someone how small it was, and through no act of mine, the text was suddenly a readable size. I have no clue why it happened, but luckily during the conference I took a picture of how wee tiny the text was so I put that in the shownotes so you’ll believe me!
The keyboard is about as tiny as you can imagine, but the keys are made out of this sort of sticky plastic, so you can push the keys with your fingernails and they don’t slip off. I can’t pretend it was a good experience, but it wasn’t nearly as bad as you would think when you first look at the keyboard. I did a fair amount of tweeting during the conference and I actually got pretty good at it. I’m also not going to lie to you, that screen is really small. If I’m wearing my glasses I can read it easily but the text is teeny weeny. I set up my gmail in the built in email client (see RIM? you have to put this in your OS) and for some reason the text was microprint. I searched all through the system for some way to control the font size but I never found an option. A couple of days ago I went to show someone how small it was, and through no act of mine, the text was suddenly a readable size. I have no clue why it happened, but luckily during the conference I took a picture of how wee tiny the text was so I put that in the shownotes so you’ll believe me!
This little powerhouse of a phone not only runs on the 4G network it has a built in 4G hotspot capability. It was easy to set up and enter a password – your only two choices are open or WPA/WPA2 personal. I liked that – they didn’t bother offering you nasty old WEP and stuff like that.
The WebOS has a feature I WISH we’d seen in the iOS 5 announcement and which is one of the top jail break apps – if you swipe down from the top of the screen you can see your battery life, and right there you can turn wifi and bluetooth off and even jump right into Airplane mode. Wouldn’t you love that on iOS???
Couple more things on the hardware. The phone is so small it doesn’t have a standard connector for charging and USB, it has a little magnet connector. One person I showed it to compared it to the mag-safe connector on the Macbooks, and I guess it is in general concept, but it doesn’t really click into place like you’d hope so a few times after I thought I’d charged it over night the battery was dead. The Veer has a very obvious mute switch on top which I think should be a Federal law. It takes 12 keystrokes on a BlackBerry to mute the darn thing! When you have your ring tone set to Some Enchanted Evening and it goes off in a staff meeting that can be REAL embarrassing.
The device aside, WebOS was pretty nice to use, and with a pretty rich application set in the app store, I think this OS might be really sweet on the upcoming HP Tablets. I would think they could, if not mismanaged, become a worthy alternative to the iPad and Android devices. It seems unintuitive to iOS users, but I bet for most people it wouldn’t take too much effort to learn and become comfortable with it.
Bottom line time. I made sure I did all of my testing and wrote up the review before I looked up the price, because I didn’t want to be swayed. This is a really nice little phone with a pretty darn nice operating system and actual apps available for it. If you’ve got big ol’ sausage fingers, or you’re in your 40s and still trying to pretend you don’t need reading glasses, don’t even think about the Veer. if you want a very small device but you don’t want to sacrifice operating system and app features, the Veer 4G might be for you. The Veer is available at the HP website for $50 with a 2 year contract, or at AT&T’s website for $100…with a 2 year contract, or get this – $0 with a 2 year contract at Best Buy! Gee, where should you go, hard to pick. And one more thing, you can get a white one.
ScreenSteps
Last week I teased you about the new product coming from Blue Mango Learning called Clarify – and they have added just a bit more teaser information to the site at bluemangolearning.com/clarify. If you head over to that link (which is of course in the shownotes), you can add yourself to the early notification list when they go live with the product. I think you’re really going to like what they’re doing with Clarify. In the mean time, if you haven’t bought ScreenSteps yet, why not? I mean, seriously. You’ve got to either hate yourself and as penance you document things using Word because you don’t deserve to be happy, or else maybe you don’t ever help people? Or maybe you like delivering documentation that’s unclear and unprofessional? I guess there’s a lot of reasons you don’t think your time is worth $40. That really doesn’t sound like a NosillaCastaway though, does it? Head on over to ScreenSteps.com and get yourself a copy of ScreenSteps Desktop and make yourself happy.
Dumb Question Corner
David writes in with our Dumb Question today:
I was wondering if you could recommend a computer program for me. See, I’m the publicity chairman of a campus sustainability club at Michigan and we need a logo. Well, so far, searching for art students and whatnot to help me design one has been relatively fruitless. I was wondering if there’s some photoshop type program that would be good for this.
I know this is incredibly open-ended. but eventually I want to create a fairly decent resolution JPEG photo (on my mac laptop! I probably should have mentioned this fact earlier). Eventually the logo for the organization will be placed on fliers, “campaign” pins and t-shirts and the like.
So my question to you is…what are the best (and easiest to use for a simpleton like me) programs for my needs? How much do they cost and are there ways to download them?
That’s about it. Thanks for your time!! -David
Great question, David! You did a fantastic job of outlining the problem to be solved, and the constraints you have. Excellent.
Let me start with a quick lesson on graphics. There are two basic types – bit map and vector graphics. Bit map graphics are where the file defines every dot in the image. You mentioned putting a jpg on a website; a jpg is an example of a bit map image. The file knows what color each dot is but doesn’t know anything more about it. Vector graphic images have more intelligence in them. So if you have a diagonal line in a vector image, the file knows that there’s a line, it knows what color it is, the length and angle.
Now why am I explaining all this? It’s very important to understand if you’ll be creating graphics that you want to put as a small jpg on a website but then also print on a flier or t-shirt where it might need to be much bigger. Bit map graphics do not scale. if you take a small jpg and try to scale it up twice as big, you’ll get jagged nasty looking edges, basically like you took each pixel and made it twice as big so you actually see squares.
So you pretty much have two choices. You can use a regular bit map image editor (and there are a bunch of reasonably priced ones) and create your graphic really really big, say the size you’ll need it on the biggest thing you’re going to use it for, and then just scale it down (which works great) for the logo for the website. Or, you can get yourself a vector art drawing program and never worry about scale. By the way, think about how much detail you’re putting into the logo when you’re creating it – lots of colors and fine detail make a poor logo when small and you’d never be able to use it on an embroidered shirt for example. Blown up big on a print t-shirt it can look good though.
Most of the programs I’m going to recommend have free trials so don’t balk at the prices until you test them out.
In the vector graphics side, I have tested DrawIt from bohemiancoding.com/drawit which would run you $41, I really liked Intaglio from purgatorydesign.com for $89. And then there’s Inkscape from http://inkscape.org/ which is actually open source and free. Might be a good idea to start with Inkscape to see if it works for you.
In the bit map graphics end of things, there are a lot of delightful options. My personal favorite is Acorn from flyingmeat.com. I’ve been reviewing this app every couple years when they come out with a new version and it just gets more and more awesome. Acorn will run you $50. then there’s Pixelmator which is a former favorite from pixelmator.com which is only $30. If you want to go free and open source there’s The GIMP from gimp.org. It’s free but really really really hard to use. I usually swear a LOT when I try to use it.
So with all that, there’s one thing we forgot to talk about. Talent. I have tested all of these tools, i’ve worked with them, played with them, studied them, and I can’t draw something beautiful to save my soul. I have no artistic talent whatsoever. if you have talent then I bet any one of the options I’ve suggested will work for you. Hope that helps, let me know what you decide.
Professor Albert
another dumb question
Please be quiet Bernard, I am trying to record… please yes, Iove you too.
Hello Allison dis is Professor Albert, coming to your from a DOGHOUSE somewhere in the suburbs of Frankfurt Germany. A number of weeks ago, da Nosillacast Goodfellas vere after me for blowing out dere eardrums and destroying your podcast, but you, Allison SHeridan da very best podcaster in da vurld taught me how to do da levels for recording so all of da Nosillacastaways now all LOVE ME. I just recently opened a FACEBOOK account and now ALL DA NOSILLACASTAWAYS have friended me – ALL TEN MILLION OF DEM, and dey all vant to take me to dinner to talk TECH. Now if I accept all dere invitations, my social calendar vill be filled until da year 2080, and I vill never get to have a date night vith my vife Elsa. So I told her Elsa I would write to dem, all da TEN MILLION NOSILLACASTAWAYS, and decline dere invitations, but I can’t figure out how to write one email to ALL my friends on FACEBOOK. And if I write dem all individually, ALL TEN MILLION OF DEM, I won’t be done until da year 2091! So now my vife Elsa has thrown me out of the house and I am living in da DOGHOUSE vith our 400 pound ST. BERNARD named Bernard – He is very sweet… but he has fleas.
So please help me out Allison with dis Dumb Question:
How do I write an email to ALL my friends on FACEBOOK so I can politely decline all da TEN MILLION Nosillacastaway’s invitations, so I can get out of the DOGHOUSE and back vith my vife?
Please help me out Allison, you ah da very best podcaster in da vurld,
da MAC MADONNA, da LADY GAGA of TECHNOLOGY. Help me out please, you ah so smart!
Well Professor Albert, I’m so sorry that my extreme fame has caused you so much distress on Facebook. Let’s see if we can come up with a workable solution. Inside Facebook they do have the ability to send messages, which show up in the recipient’s respective Facebook pages, and if they have it set up to the defaults will also send them an actual email. I ran a test and it turns out you can put people in lists, and then send to the entire list. Unless there’s more than 20 people in the list. I guess that solution is out.
The real answer here is to think differently about how to communicate in Facebook. The way you do that is simply post a message on your wall. Since all 10m of the NosillaCastaways will be watching their own News Feeds in desperate anticipation of a message from you, they will immediately see your message. You don’t have to spam…I mean delight your new fans with emails, they have opted IN to reading every word of your status updates.
You can include links, like one to the lovely photo you sent of yourself that I have posted in the shownotes. You can put links to Saint Bernard care in there too, and even solicit help with the flea issue. Since you are such a delightful person, your new fans will assuredly write back on your wall with their own suggests and praise for the very important research you do. I hope this gets you out of the dog house and back to Elsa. I’m betting Bernard would like his room back to himself as well.
Smile
You may have noticed by now that I never advertise for a service I don’t really really believe in. I don’t take on just anyone as an advertiser because I can’t sit here and read stock copy or pretend I think something is swell when I think it’s junk. Same reason I don’t review truly dreadful software, I just tell the developer what I think they need to improve and move on. That’s why when Jean from Smile approached me to advertise for them I was delighted. As a user of TextExpander for as far back as I can remember, I knew I’d be able to come up with weekly stories about how TextExpander saved me time. In writing the review of the HP Veer, I had to type WebOS over and over again. It’s only 5 characters so you’d think it wouldn’t be worth the time to create a TextExpander snippet, but since the W O and S are capitalized but the e and the b are not, I actually have to type capital w, e b, capital O, capital S. that’s actually EIGHT keystrokes. Instead I right clicked on it after I typed it once, and selected Create TextExpander snippet, and chose w-o-s as my snippet. In just 3 characters I can replace 8…and 8 ANNOYING characters at that. This is one of those tools that you should buy as a present for yourself. To become a faster typist, to save on repetitive stress injuries, to reduce typos – it’s all good. Why don’t you go over to smilesoftware.com and buy yourself a present today? Check out all their other fine products while you’re there, I’m sure you’ll find something you like and need. Be sure to tell them you heard about it here on the NosillaCast!
Chit Chat Across the Pond
Security Light
- Important cross-platform Flash update – ATTACKS IN THE WILD – adobe.com/support/security/bulletins/apsb11-13.html
- Reminder – next Tuesday is patch Tuesday for both MS and Adobe (patches promised for Windows, Office & Adobe Reader) – microsoft.com/technet/security/bulletin/ms11-jun.mspx and adobe.com/support/security/bulletins/apsb11-16.html
Main Topic – Understanding Digital Signatures
The same tech that underlies digital signatures underlies much of modern computer security, so I think it’s worth actually understanding it. It’s not magic, but it is imaginative and ingenious.
There are two fundamental concepts at the root of this stuff, both are mathematical, but you don’t need to understand the math at all to get how it works. Using just those two concepts you can build up an entire security architecture, including digital signatures, HTTPS, and VPNs.
1) Asymmetric Encryption – AKA Public Key Encryption
When we think encryption we normally think of symmetric encryption, you have one key, you use that key to turn your data into gibberish, and you later use that same key again to turn thatgibberishback into your data. Asymmetric encryption adds a small but VERY signifficant complication to this concept.
With Asymmetric encryption there are TWO keys, lets call them A & B. If you encrypt your data with key A, you can ONLY decrypt it with key B. Key A CANNOT un-encrypt the data. The same works the other way around, if you encrypt with B, you have to decrypt with A.
For so-called public-key-encryption we arbitrarily choose to keep one of the two keys secret, and to publish the other one. It doesn’t matter which we choose, but once we have chosen, we can’t change our mind safely. You MUST keep your private key completely secure, and you can give your public key to anyone without any security danger at all.
What does this let us do?
i) safely send data to someone without ever having to share secret information:
Allison is in a web cafe so all her traffic is being sniffed, she wants Bart to send her sensitive data in a secure way. With symmetric encryption this could never work, because Bart would have to send Allison the one and only key, and the attacker would then have both the key and the encrypted data! Asymmetric encryption to the rescue!
Bart asks Allison for her PUBLIC key, this can be safely sniffed by the bad guy in SBux, in fact, she could publish it on her web page safely. Bart uses Allison’s public key to encrypt the sensitive data and send it to Allison in the full knowledge that the badguy in sbux will see it. Allison then uses her PRIVATE key to decrypt the data. The bad-guy has captured every bit of data exchanged between Bart & Allison, but since Allison’s private key was never sent, the attacker can’t decrypt the data!
ii) secure key exchange:
It’s easy to imagine how Bart & Allison could exchange data over and back securely if both had a public and private key. Bart would encrypt with Allison’s public key, and Allison with Bart’s public key.
The problem is that asymmetric encryption and decryption is computationally difficult. The math is hard so it makes your poor CPU work very hard. Symmetric encryption is really easy by comparison, and is really easy on your CPU. So, how can you efficiently create an encrypted communication channel? Put the two ideas together!
You use asymmetric encryption to exchange a randomly generated key, then switch to symmetric encryption using that key!
This is how SSL works, and hence how you can create a secure VPN tunnel from an internet caffe where the bad guys can see every byte you exchange with your VPN server. This is also how HTTPS works, and how SSH works. This is why those secure technologies can be used from internet cafes.
iii) verify the sender of an encrypted file:
Imagine Bart has his public key on his website, and Allison wants him to send her something, but she needs to be certain it came from Bart. Bart would encrypt the file with his PRIVATE key, and then the only key in the world that could decrypt it is Bart’s PUBLIC key, so Allison can go to Bart’s website, get his key, and then decrypt the file. If the key works, Bart sent it!
2) Hashing Functions (AKA digital digests)
A hashing function is a piece of math that turns any piece of data, no matter how long, into a fixed-length blob of gibberish. There are two important points:
i) hashes are designed to be very sensitive to change, tiny changes to the input make massive changes to the output
ii) hashes are designed to be one-way functions. It takes minimal computer effort to go from the data to a hash, but it is effectively impossible to go from a hash back to the original data.
How on earth could a strange mathematical function like this be useful?
i) hashes are great for detecting transmission errors. If you have a file, then take a hash of it, and publish both the file and the hash to your website, you can verify that the download was notcorruptedby re-calculating the hash, and verifying that it’s the same as the one on the site.
ii) hashes let you store data without storing the data. It is used for passwords all the time. Websites (and even your Mac) store hashes of your passwords. Each time you log in the website hashes the password you give, and then compares that hash to the one they have saved, if they match, you get in, if not, you don’t. The key is that they never save your password, so if they are hacked, the bad guys don’t get the list of passwords.
Some hashing functions you may have heard of are MD5, SHA-1, or SHA-1’s younger brothers SHA-256 and SHA-512
3) AsymmetricEncryption+ hashing functions = digital signature
As un-obvious as it may sound, you can combine asymmetric encryption with hashing functions to generate digital signatures.
What do you need before you can start digitally signing things?
i) an Asymmetric key pair
ii) you need to publish your public key to either the world, or to those who you want to be able to verify your signature
How do you create a digital signature?
i) generate a hash of the document you want to sign
ii) encrypt that hash with your PRIVATE key
That’s it!
How do you verify a digital signature?
i) get the signer’s public key
ii) decrypt the encrypted hash (i.e. the digital signature)
iii) calculate the hash of the document youreceived
iv) compare the hash you got directly from the document with the hash you got by decrypting the signature, if they match, then you know that the document has not been changed since it was signed, and that it really was signed by the sender.
4) Pre-installed public-keys + Digital Certificates + Digital Signatures = Certificate Authorities = verifiable public key sharing
So far we have always made one assumption – that we are sure the public key we have really belongs to the person we think it belongs to. If some bad guy gave Allison their public key and managed to convince her it was Bart’s, then the whole thing breaks down!
So, we need one more piece of security magic to tie it all together, we need a way of verifying the ownership of a public key. This is where digital certificates come in.
What is a digital certificate? It’s a file that contains at least the following information:
i) the public key to be shared
ii) the name or email address or domain that the key will be linked to
iii) a date range over which the key is valid
iv) a digital signature of the certificate signed by a certificate authority
What a digital certificate does is digitally sign a union of a key and an identity. This shifts the problem from trying to verify the authenticity of every public key for every person or website you ever interact with, to trying to verify the public keys of a handful of Certificate Authorites (CAs), and we have a simple solution for that too – they come pre-installed as part of your OS, and are updated through software update!
Using only two pieces of math, asymmetric encryption and hashing functions we have now got a reliable digital signature!
What does a digital signature tell us?
i) if the digital signature matches then we know the file or app or email or what ever was definitely not altered since it was signed
ii) the person who’s identified as owning the public key that was used to sign the file or app or email is the person who sent it
That is ALL it tells us!A digital signature does NOT verify morality, it ONLY verifies integrity and source!
Digital signatures have many many uses in security, but just because an app is signed does not mean it is safe. It does mean that if it is malware you know where to point your lawyers later 🙂
Some examples of digital signatures in use:
i) in iOS, ALL apps MUST be digitally signed BY APPLE, or the OS will not run them. This means that only approved apps can run on iOS, so the digital signature verified that Apple have tested and approved the app. When you jail-break a phone you disable this digital signature check, so the OS will run any app, regardless of whether or not it’s signed.
ii) in OS X, digital signatures are used by the keychain to stop apps from accessing each other’s passwords. When you save a password in your keychain the password AND the digital signature are saved together, when the app asks the keychain for the password later, it will not give it if the app no longer matches the signature. When this happens they keychain will present you with a popup telling you that the app has changed, and asking you to verify that you understand that the app has changed, and that you are happy for the keychain to update it’s stored signature going forward. You see this every time you update an app (except through the Mac app store where the apps are all signed by Apple, and hence trusted by the OS).
iii) many OSes require that all drivers be digitally signed by the developer. This allows you to be sure that your printer driver really did come from HP etc..
Bart is such a wonderful instructor, I just love learning from him. You can tell the difference between someone who knows their stuff and someone who doesn’t by the way they answer your questions. Bart always encourages me to ask the question to make sure I get it, rather than those who can’t explain themselves well and make you feel like an idiot. In case you didn’t follow everything yourself, or if you want a resource to point to for others to understand, Bart did extensive shownotes which are all at podfeet.com for this show. I have a feeling I’ll be referring back to this particular episode to trigger my memory.
That’s going to wind this up for this week, many thanks to our sponsors for helping to pay the bills: ScreenSteps, and Smile. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter at twitter.com/podfeet. If you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time. Thanks for listening, and stay subscribed.

So glad to have you back Bart. You can take the most complex of topics and make them understandable for me.
Great to her you again, Bart. I hope you’ll fully recover shortly, so we can listen to you on weekly Basis again!
Welcome back Bart, we missed you !
I guessed what application Connor would be talking about, as I was listening to the podcast on Instacast at the time.
Also may inquire what microphone he was using to record that review.
Great Show as ever!