Hi, this is Allison Sheridan of the NosillaCast Apple Podcast, hosted at Podfeet.com, a technology geek podcast with an EVER so slight Apple bias. Today is Sunday, February 9, 2020, and this is show number 770.
Closed Captions on YouTube
Steve is still furiously creating the interview videos and audio from CES and we noticed something interesting. Remember I talked about the terrific service otter.ai that will create transcripts suitable for video subtitles last week? My free one-month trial is still going on so I thought I’d add subtitles to the video interviews while it was still free. Well, imagine my surprise when I checked a couple and they already had subtitles? I knew that Google had started doing some magic transcription, but I figured it would be pretty bad. So I produced the transcripts of a few videos using Otter.ai, but guess what? The Google ones are just as good! Both make mistakes, but they make different mistakes.
I wasn’t heartbroken that we didn’t have to do this extra work of course, but I was a little disappointed not to be able to use this new, shiny tool I’d found. But then Steve noticed that out of the 20 or so videos he’s produced so far, three didn’t have subtitles. And one of them had subtitles but they were mostly in Dutch! Even better, at one point in the video, the subtitles just said, “oh boy oh boy oh boy oh boy” for about two minutes! While that was entertaining, we decided to fix it. I taught Steve how to generate them using Otter (took about three minutes to teach him because it’s SO easy) and now they’re complete. He exports the full audio with the music on both ends, imports it to Otter.ai, they do the magic, he exports the SRT file and then imports it into the Captions section on YouTube.
It’s extra work for him but we think it’s really cool we’re able to do this. Not only does it make the videos accessible to those with hearing impairments, but sometimes people want to watch a video but are in an environment where they can’t play the audio so this can help in those situations too. Very cool all around.
Chit Chat Across the Pond
This week we sort of had two Programming By Stealth episodes. After Programming By Stealth 89, alert listener @lbutlr on Twitter pointed out that Bart’s maths were actually wrong in his solution to the currency conversion homework challenge. Bart took this as a learning opportunity for himself and for us. When he figured out where his logic went awry, he wrote it up including the solution to the problem as a blog post. Now it doesn’t exactly fit into the flow of the Programming By Stealth series, but we still wanted to talk about it. Figuring this could happen again, he dubbed this the inaugural episode of yet another series, Programming By Stealth Tidbit 1 of Y.
In Programming By Stealth 89, I asked the question of whether some currencies maybe don’t have 2 decimal places, and Bart thought they all did. @lbutlr also chimed in on this, telling us that Korean Won and Japanese Yen both don’t have anything past the decimal. I explain in this Tidbit segment that I realized the ISO 4217 database I’m using to scrape the names of the countries contains a field called Minor Unit, which is the number of decimal places for each currency. I discovered that some have 0, most have 2, but some have 3 and 4 decimal places! I decided to try to update my code to take this into account, and now Bart says I have to write a blog post about how I figure it out when I do. Great, more work to do!
In any can, the tidbit segment is quite short at less than 15 minutes.
Then we had the real Programming By Stealth episode where Bart Busschots explains JavaScript wrapping and boxing. It’s a really cool feature where JavaScript sort of helps us out when we need a little bit more out of some data than it’s originally meant to give us. Since we’ve now separated the challenge solutions into standalone shows, this episode of Programming By Stealth is also pretty short by PBS standards at under 44 minutes. Both are great fun. You subscribe to them in your podcatcher of choice by searching for Programming By Stealth and you can read along with Bart’s shownotes at pbs.bartificer.net/…
Update on Podfeet possible DDOS
Last week on the show I told you that podfeet.com was possibly under a denial of service attack. Bart had been working with me to try to figure out what was going on. We started a free trial of a service called Site24x7.com which would allow me to monitor the health of my server. Throughout much of last week we watched the site go down and then come back up. It was gruesome to just watch and wait while we tried to find a pattern to what was happening. By “we” of course I mean “Bart”.
The bad news is that we didn’t find a pattern, but Bart did find a knob he could turn to help solve the symptom. Let me do my best to explain my limited understanding of what he changed. A website needs web server software, and my website is run on the web server software called Apache. One of the settings for the web server is how many instantaneous web requests it will try to serve.
My server was set to allow 150 per second. That didn’t sound like a big number to me, but Bart pointed out this is all simultaneously. I asked if 150 is like CNN-level traffic and he said maybe not, but Leo LaPorte-level traffic. Now here’s the problem with allowing my server to have 150 simultaneous requests. Each request spawns what’s called a busy_worker. Each busy_worker needs some RAM. 150 busy_workers need more RAM than my server has. So when the anomaly occurred, my server ran out of RAM and shut down. Then it restarted itself and all was grand. Till the anomaly occurred again. We’re calling it an anomaly because technically we don’t know if it’s a malicious attack.
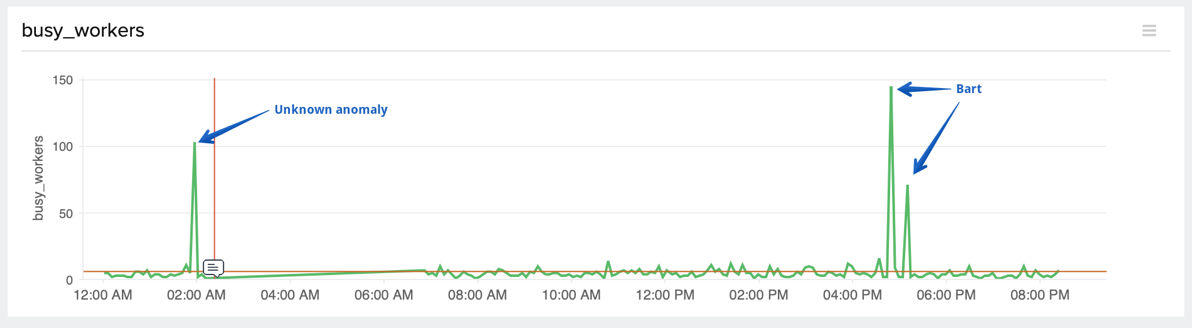
Bart sent me a note asking permission to do his own personal denial of service attack on podfeet.com. Well that sounds fun, “sure!” I replied. He wanted to do a controlled attack because he could test his theory about the number of busy_workers and then see if he could reduce the number until any attack didn’t cause the server to fall over in a heap. He got down to 60 simultaneous requests and it was still dying, but when he got down to 50 he could no longer knock it down.
Ever since then we’ve been watching, and these anomalies keep happening, usually twice a day but never at the same time. Sandy asked me whether I could see the IPs from which requests are coming at those times. I thought that was a grand idea to see who is attacking me. I caught the problem happening and quickly grabbed the log file of web requests and parsed it in Excel. I discovered that at any old point in time, two IPs in Romania are making 25% of the web requests and that’s when nothing bad is happening. During the anomalies I haven’t found any odd behavior by a set of IPs, and in fact the total number of hits does not go up.
I’m not at all convinced it is a denial of service attack yet, but for now Bart has been able to mitigate the issue. I’ve been keeping people up to date by posting in our Slack community at podfeet.com/slack, and in our Facebook community at podfeet.com/facebook, a bit on Twitter @podfeet, and of course I let our lovely Patrons know over at podfeet.com/patreon. I sure hope it stops, it’s been a lot of work to keep writing to all the different channels!
Blog Posts
I’d like to start with a quick little tip from good friend of the show, Trevor in Canberra:
Hi NosillaCastaways, Trevor from Canberra here with a wonderful discovery I found via a sponsored Facebook ad. Now we all love shopping on line and getting a bargain each time we purchase our new gadgets, well I’ve come across this fantastic extension for Safari that does all the leg work for you. It’s called “Honey” and its free. Don’t worry if you use another browser like Firefox or Google Chrome, there are extensions for them too!
The company blurb goes like this: “If you don’t already know, Honey is a free browser extension that automatically scans the Internet for every working coupon code while you’re shopping online. Then at checkout, it instantly applies the best deal to your cart!”
What’s not to like? Well, for a start, to allow “Honey” to do its so-called function you have to give it permission in Safari. But giving permission comes with this warning, Honey “Can read sensitive information from webpages including passwords, phone numbers and credit cards on all webpages”. It can also see your whole browsing history. Sounds really dodgy to me.
As Bart says: “Follow the Money” and in this case you don’t have to look very far. I don’t know if Honey even works as I deleted it as soon as I saw that warning.
I’ll get my bargains from Amazon using Allison’s affiliate links and we both benefit.
Wow, that’s pretty crazy, Trevor. I love to see the affect that Bart’s guidance has had on all of us. I never used to read privacy policies but I’m doing it more and more. Your story here works perfectly into Security Bits later in the show.
CES 2020: Top Greener In-Wall USB Power Receptacles
I loved Kyle’s absolute excitement about USB power receptacles. That’s a guy who loves what he does, isn’t it? They did look really cool. I also liked how he kept teasing the best one till the end!
CES 2020: Shure MV88+ Video Kit for Portable Recording
Tesla Tech – Range Anxiety is Real
CES 2020: iKuddle Smart Home for Cats
At first when I realized that there were five companies working on cat litter removal at CES, I thought I should interview them ALL! But sadly, iKuddle is the only cat litter interview we did at CES.
CES 2020: Wi-Charge Wireless Power Delivery
When Steve posted the link to the Wi-Charge video in our Slack, there were a couple of great questions. John Dawson questioned the marketing description we put in the video explanation. He said he’d really like to know if Allison was telling him it was true that it was as cool as it sounds. @lbutlr asked about some specifics on it about whether it’s really shipping and did we really think it could deliver the power that Yuval told me it could do.
Both of these are great questions. First of all, I don’t always know whether the devices are real and whether they will ever be real products. Steve explained on Slack that there are several different categories of devices and products shown at CES. He said that there are some more established companies (e.g. Brydge, Shure, Ring, Sense, Belkin, … ) that reliably ship what and when they say they will. In fact, many of these companies are shipping the products already that they show off at CES. Sense was an example of that.
Steve went on to explain that some smaller companies ship the product late, or possibly not at all. But sometimes they surprise you. Remember the Acouva earbuds with the removable batteries? As we walked away I told Steve I thought they were clearly not close to shipping because the models we saw didn’t appear to be production units. Imagine my surprise last week when I got an email from them saying that they’re shipping the product already!
There’s also the companies showing off really early development products. Remember Steve’s interview with Dr. Andrei Dragomir of Aquark Technologies, about compact quantum devices? Those were definitely prototypes but it’s still really cool to see the future before it gets here. Like Wi-charge, these won’t be devices you ever buy directly from these companies but rather their technology will hopefully be part of other devices in the future.
Overall we choose the vendors we interview based on whether the product seem to solve a real problem for people and then try to show it to you in a light where you understand whether the product is anywhere near being something we can actually buy.
Thanks for the great questions folks, keep them coming.
Support the Show
I mentioned our lovely patrons when I was talking about how I was messaging the community. You may be wondering what this is about, or this may be the 238th time you’ve heard me talk about it. The idea is that you can help support the production of the show financially by going to podfeet.com/patreon and deciding on a dollar amount per show that you’d like to pledge. Think about the value you get from the show: it might be learning new tools, it might be learning about a gadget you now know you can’t live without, it might be learning about how to diagnose a denial of service attack, or what things to be worried about or not worried about in Security Bits. If you get a dollar a week’s worth of value out of the show, go ahead and become a Patron. If you are having trouble making ends meet, I forbid you to become a patron. Seriously, don’t do it, and don’t feel badly about it. Only do this if you have the money to spare and would like to help keep the podcast going.
Security Bits — 9 February 2020
That’s going to wind this up for this week. Don’t forget to send in your Dumb Questions, comments and suggestions by emailing me at [email protected], follow me on twitter @podfeet. Remember, everything good starts with podfeet.com/. podfeet.com/patreon, podfeet.com/paypal, podfeet.com/facebook, podfeet.com/slack! And if you want to join in the fun of the live show, head on over to podfeet.com/live on Sunday nights at 5pm Pacific Time and join the friendly and enthusiastic NosillaCastaways. Thanks for listening, and stay subscribed.

